Regulation enforcement authorities from 12 international locations arrested 4 suspects linked to the LockBit ransomware gang, together with a developer, a bulletproof internet hosting service administrator, and two folks linked to LockBit exercise.
This joint motion additionally led to seizures of LockBit infrastructure servers and concerned cops in Operation Cronos, a job pressure led by the U.Ok. Nationwide Crime Company (NCA) behind a world LockBit crackdown and an investigation that started in April 2022.
In keeping with Europol, a suspected LockBit ransomware developer was arrested in August 2024 on the request of French authorities whereas on vacation outdoors of Russia.
The identical month, the U.Ok.’s Nationwide Crime Company (NCA) arrested two extra people linked to LockBit exercise: one believed to be related to a LockBit affiliate, whereas the second was apprehended on suspicion of cash laundering.
In a separate motion, at Madrid airport, Spain’s Guardia Civil arrested the administrator of a bulletproof internet hosting service used to protect LockBit’s infrastructure.
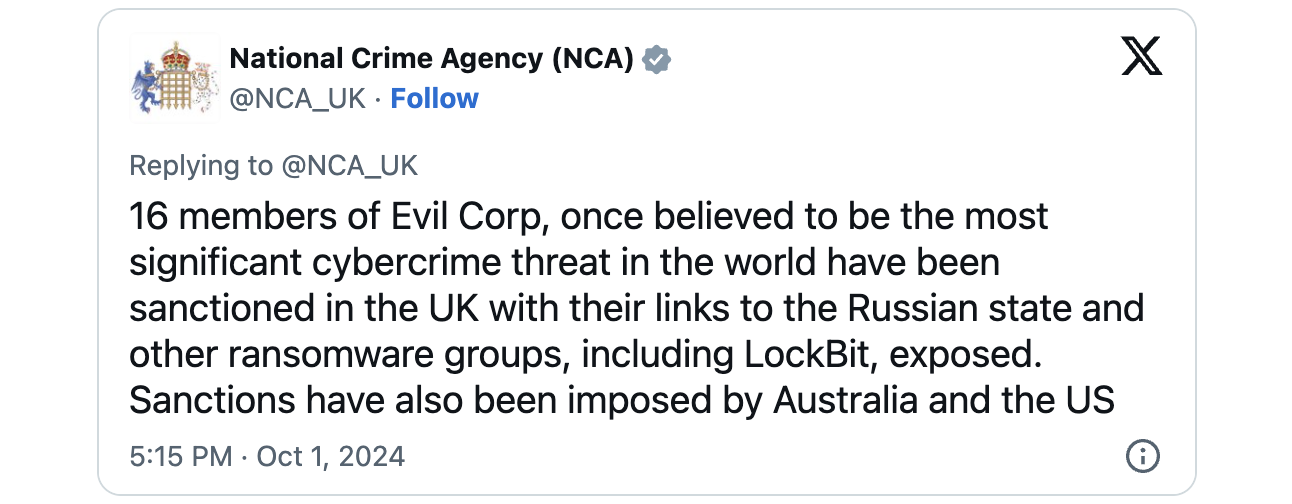
At the moment, Australia, the UK, and the USA additionally revealed sanctions in opposition to a person the UK NCA believes is a prolific LockBit ransomware affiliate linked to Evil Corp.
The UK sanctioned 15 extra Russian nationals concerned in Evil Corp’s legal actions, whereas the USA sanctioned six people and Australia focused two.
“These actions follow the massive disruption of LockBit infrastructure in February 2024, as well as the large series of sanctions and operational actions that took place against LockBit administrators in May and subsequent months,” Europol mentioned.
Further LockBit arrests and fees
LockBit emerged in September 2019 and has since claimed accountability for and been linked to assaults in opposition to many high-profile firms and organizations worldwide, together with Financial institution of America, Boeing, the Continental automotive large, the Italian Inner Income Service, and the UK Royal Mail.
In February 2024, Operation Cronos shut down LockBit’s infrastructure and seized 34 servers containing over 2,500 decryption keys that had been later used to create a free LockBit 3.0 Black Ransomware decryptor.
The U.S. Division of Justice and the UK NCA estimate that the gang has extorted as much as $1 billion following no less than 7,000 assaults between June 2022 and February 2024.
Earlier arrests of Lockbit ransomware actors (a few of them already charged for numerous offenses) embrace Mikhail Pavlovich Matveev (aka Wazawaka) in Might 2023, Artur Sungatov and Ivan Gennadievich Kondratiev (aka Bassterlord) in February 2024, and Dmitry Yuryevich Khoroshev (aka LockBitSupp and putinkrab) in Might 2024.
In July, Russian nationals Ruslan Magomedovich Astamirov and Canadian/Russian nationwide Mikhail Vasiliev additionally admitted to collaborating in no less than a dozen ransomware assaults as associates of the LockBit ransomware-as-a-service operation.
Astamirov was arrested in Arizona in June 2023 and charged with deploying LockBit ransomware. Vasiliev, who was extradited to the USA in June, has already been sentenced to 4 years in federal jail.