An operator of the HelloKitty ransomware operation introduced they modified the identify to ‘HelloGookie,’ releasing passwords for beforehand leaked CD Projekt supply code, Cisco community info, and decryption keys from previous assaults.
The risk actor who made the announcement goes by the identify ‘Gookee/kapuchin0’ and claims to be the unique creator of the now-defunct HelloKitty ransomware.
As first reported by risk researcher 3xp0rtblog on Thursday, the rebranding coincides with the launch of a brand new darkish net portal for HelloGookie.
To have a good time the launch, the risk actor launched 4 non-public decryption keys that can be utilized to decrypt recordsdata in older assaults, in addition to inner info stolen from Cisco in a 2022 assault and passwords for the leaked supply code for Gwent, Witcher 3, and Pink Engine stolen from CD Projekt in 2021.
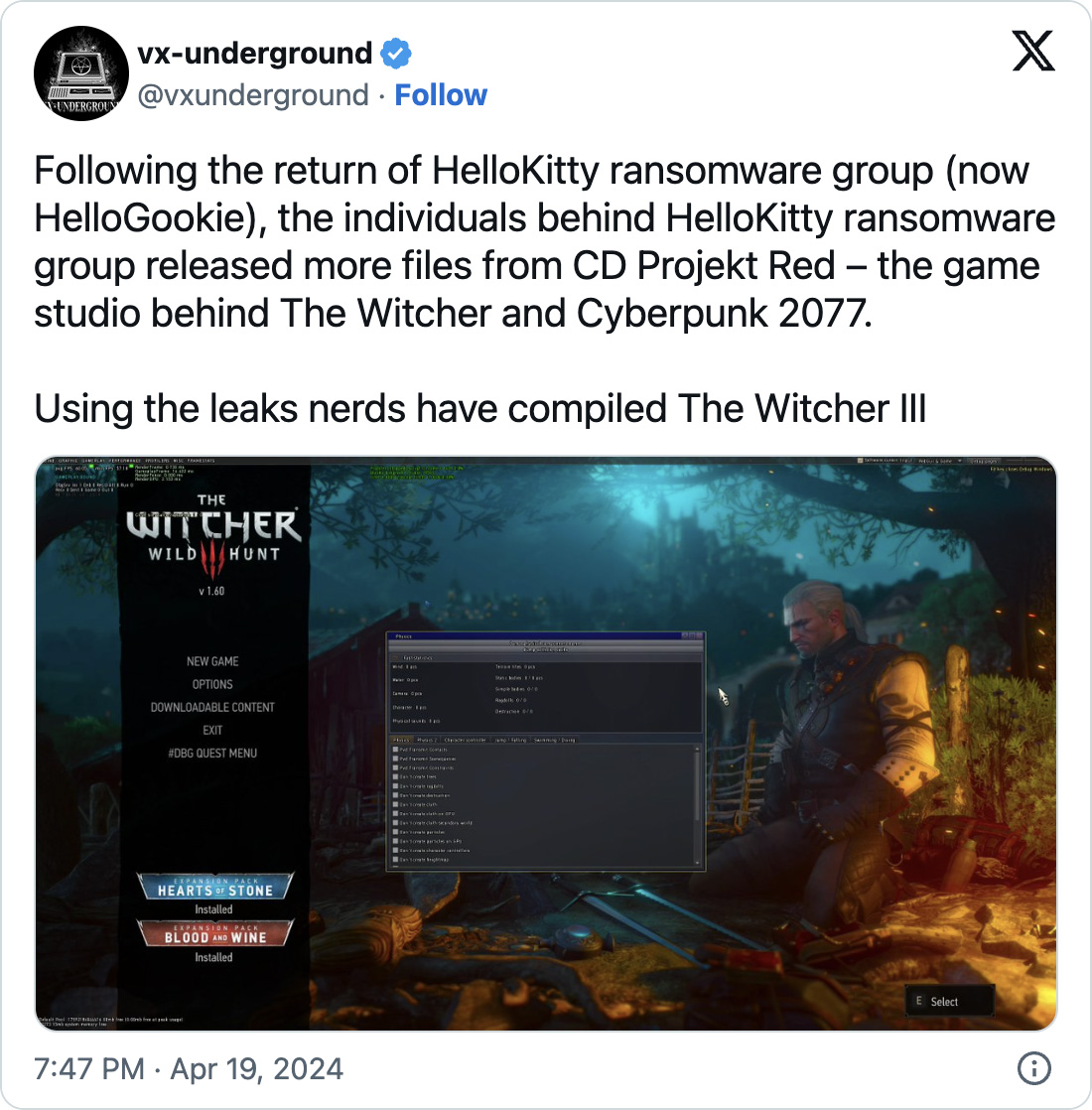
As first noticed by VX-Underground, a gaggle of builders have already compiled Witcher 3 from the leaked supply code, sharing screenshots and movies of improvement builds.
One consultant of the group compiling Witcher 3 often called ‘sventek’ informed BleepingComputer that the leaked CD Projekt knowledge is 450 GB uncompressed and accommodates supply code for Witcher 3, Gwent, Cyberpunk, varied console SDK (PS4/PS5 XBOX NINTENDO), and a few construct logs.
BleepingComputer was informed that the leaked supply code accommodates binaries permitting the launch of a developer construct of Witcher 3. The builders at the moment are engaged on compiling the sport from the supply, sharing a video and screenshots with BleepingComputer that they are saying have been taken from an early construct.
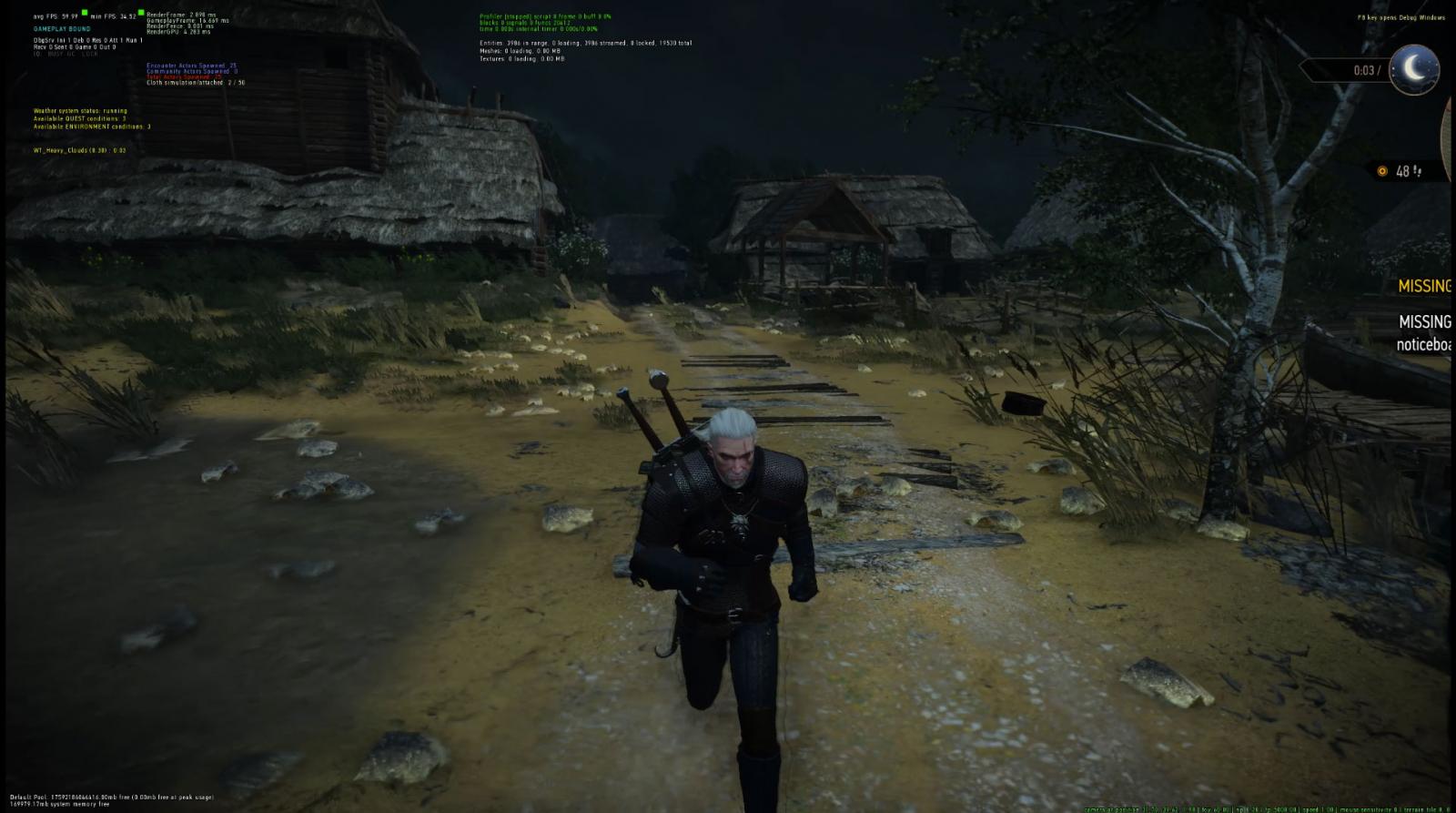
Supply: Sventek
Sventek informed BleepingComputer that they have been beforehand in a position to compile Cyberpunk 2077 from the CD Projekt’s leak and have been behind the earlier GTA V supply code leak.
Who’s HelloKitty
HelloKitty was a ransomware operation launched in November 2020, infamous for attacking company networks, stealing knowledge, and encrypting techniques.
Their first high-profile assault occurred in February 2021, after they breached CD Projekt Pink, the creator of the Cyberpunk 2077, Witcher 3, and Gwent titles. The ransomware gang encrypted the corporate’s servers and stole supply code as a part of the assault.
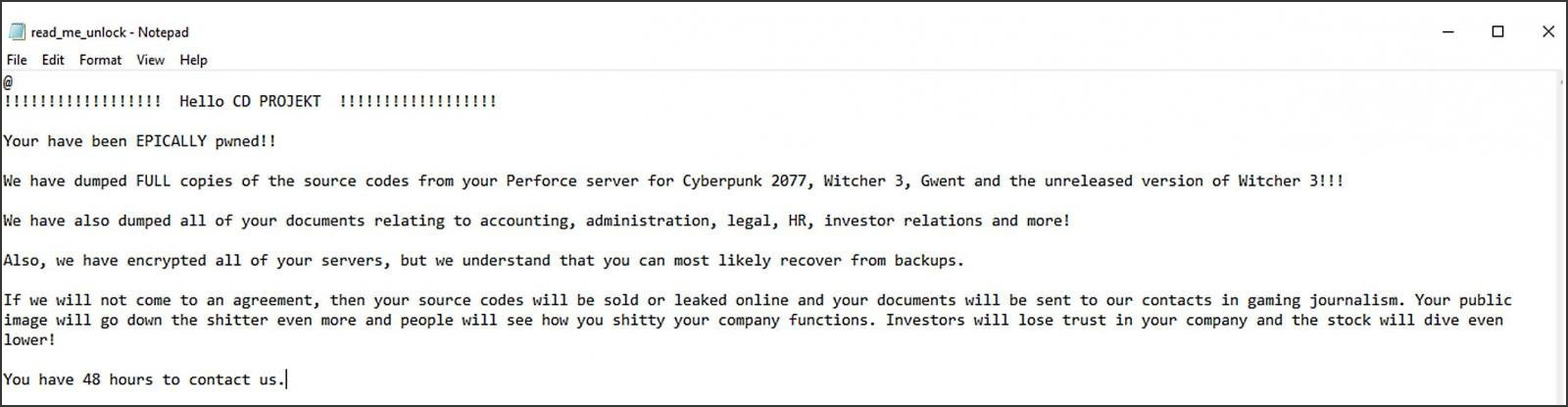
Supply: BleepingComputer
HelloKitty later claimed that they had offered the information on the darkish net, together with the code for the then unreleased Witcher 3.
The ransomware operation step by step grew bigger, releasing a Linux-focused variant in mid-2021 that focused VMware ESXi, creating further profit-making alternatives for its associates.
In 2022, the information leak web site for one more ransomware operation, Yanluowang, was allegedly hacked to leak conversations between the members. These conversations revealed that Yanluowang was tightly related to the developer of HelloKitty, who used the identify Guki within the conversations.
In October 2023, Gookee/kapuchin0 leaked the HelloKitty builder and supply code on a hacker discussion board, marking the tip of operations.
Returns as HelloGookie
The risk actor now claims that they rebranded the ransomware operation as HelloGookie however has not revealed any new victims and has no proof of current assaults.
Nevertheless, the risk actor has launched stolen info from older assaults on CD Projekt Pink and Cisco. The info leak web site additionally consists of 4 non-public decryption keys for an older model of the HelloKity ransomware encryptor, which may enable some victims to get well their recordsdata without cost.
Researchers informed BleepingComputer that they’re at present investigating the keys to find out which variations of the encryptor they work with.
.png)
BleepingComputer
The Cisco entry on the information leak web site accommodates an inventory of NTLM (NT LAN Supervisor) hashes (encrypted account passwords) supposedly extracted throughout a safety breach.
Cisco beforehand admitted in 2022 that it had been hacked by the Yanluowang ransomware group, an incident allegedly restricted to the theft of non-sensitive knowledge from a single compromised account.
Kapuchin0’s entry to this knowledge and a shout-out to Yanluowang present a better collaboration between the 2 teams than initially identified.
“Cisco is aware of the recently published information referencing a security incident in May 2022. A detailed summary of the incident can be found in this August 2022 blog post by Cisco Talos, our threat intelligence research organization,” Cisco informed BleepingComputer right now relating to the leak of knowledge.
It stays to be seen whether or not HelloGookie will attain the operational success, assault volumes, and notoriety ranges of HelloKitty.