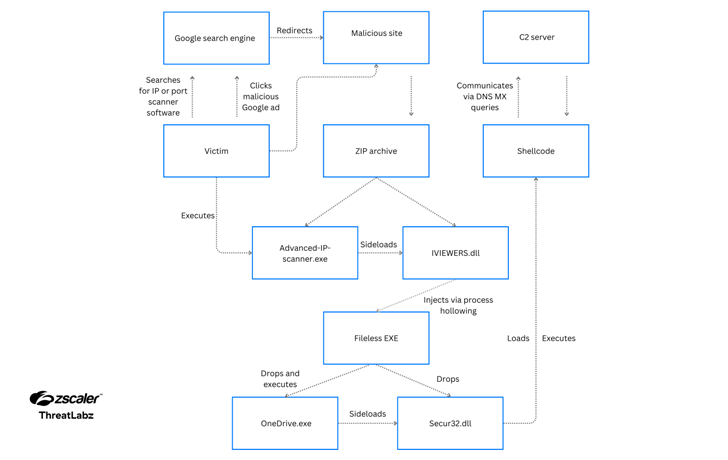
A brand new Google malvertising marketing campaign is leveraging a cluster of domains mimicking a authentic IP scanner software program to ship a beforehand unknown backdoor dubbed MadMxShell.
“The threat actor registered multiple look-alike domains using a typosquatting technique and leveraged Google Ads to push these domains to the top of search engine results targeting specific search keywords, thereby luring victims to visit these sites,” Zscaler ThreatLabz researchers Roy Tay and Sudeep Singh mentioned.
As many as 45 domains are mentioned to have been registered between November 2023 and March 2024, with the websites masquerading as port scanning and IT administration software program reminiscent of Superior IP Scanner, Offended IP Scanner, IP scanner PRTG, and ManageEngine.
Whereas that is not the primary time risk actors are banking on malvertising methods to serve malware through lookalike websites, the event marks the primary time the supply automobile is getting used to propagate a complicated Home windows backdoor.
Thus, customers who find yourself trying to find such instruments are displayed bogus websites that embrace JavaScript code designed to obtain a malicious file (“Advanced-ip-scanner.zip”) upon clicking the obtain button.
Current inside the ZIP archive is a DLL file (“IVIEWERS.dll”) and an executable (“Advanced-ip-scanner.exe”), the latter of which makes use of DLL side-loading to load the DLL and activate the an infection sequence.
The DLL file is chargeable for injecting the shellcode into the “Advanced-ip-scanner.exe” course of through a method referred to as course of hollowing, following which the injected EXE file unpacks two further recordsdata – OneDrive.exe and Secur32.dll.
OneDrive.exe, a authentic signed Microsoft binary, is then abused to sideload Secur32.dll, and in the end execute the shellcode backdoor, however not earlier than organising persistence on the host by the use of a scheduled process and disabling Microsoft Defender Antivirus.
The backdoor – so named for its use of DNS MX queries for command-and-control (C2) – is designed to assemble system info, run instructions through cmd.exe, and carry out fundamental file manipulation operations reminiscent of studying, writing, and deleting recordsdata.
It sends requests to the C2 server (“litterbolo[.]com”) by encoding the information within the subdomain(s) of the Totally Certified Area Identify (FQDN) in a DNS mail change (MX) question packet and receives instructions encoded inside the response packet.
“The backdoor uses techniques such as multiple stages of DLL side-loading and DNS tunneling for command-and-control (C2) communication as a means to evade endpoint and network security solutions, respectively,” Tay and Singh mentioned.
“In addition, the backdoor uses evasive techniques like anti-dumping to prevent memory analysis and hinder forensics security solutions.”
There may be presently no indication of the place the malware operators originate from or what their intentions are, however Zscaler mentioned it recognized two accounts created by them on felony underground boards like blackhatworld[.]com and social-eng[.]ru utilizing the e-mail handle wh8842480@gmail[.]com, which was additionally used to register a website spoofing Superior IP Scanner.
Particularly, the risk actor has been discovered partaking in posts providing methods to arrange limitless Google AdSense threshold accounts manner again in June 2023, indicating their curiosity in launching their very own long-lasting malvertising marketing campaign.
“Google Ads threshold accounts and techniques for abusing them are often traded on BlackHat forums,” the researchers mentioned. “Many times they offer a way for the threat actor to add as many credits as possible to run Google Ads campaigns.”
“This allows the threat actors to run campaigns without actually paying until the threshold limit. A reasonably high threshold limit lets the threat actor run the ad campaign for a significant amount of time.”