Since we first made KICS (Holding Infrastructure as Code Safe) by Checkmarx accessible in November of 2020, we’ve seen over a million downloads, and the counter retains clicking. In actual fact, KICS has been so efficient and so standard that it was built-in into model 14.5 of the GitLab DevOps Platform as its default infrastructure-as-code scanning instrument. As one developer mentioned on Twitter: “IMO, KICS is one of the best IaC open source solution[s].”
After greater than one million downloads, are there new capabilities to tempt builders who have to scan IaC information to detect insecure configurations that would expose purposes, knowledge, and providers to assault? In a phrase: sure. On this weblog put up, we’ll deal with the auto-remediation functionality that was made accessible in model 1.6. Right here’s a video demonstration explaining the way it works.
How one can Use Auto-remediation
As proven within the video demonstration above, Checkmarx KICS auto-remediation is accessible throughout the free Checkmarx One™ Visible Studio Code plugin. This can be a free instrument supplied by Checkmarx for all VS Code customers, and doesn’t require the consumer to submit credentials for a Checkmarx One™ account. With each the plugin and Docker put in in your native machine, it detects supported Infrastructure-as-Code (IaC) file varieties and initiates a KICS scan mechanically.
Upon scan completion, the plugin highlights findings, and proposals throughout the IaC file and thru a single click on, lets you mechanically apply KICS remediation suggestions to safe your IaC. To study extra, checkout the KICS Auto Scanning Extension for Visible Studio Code documentation.
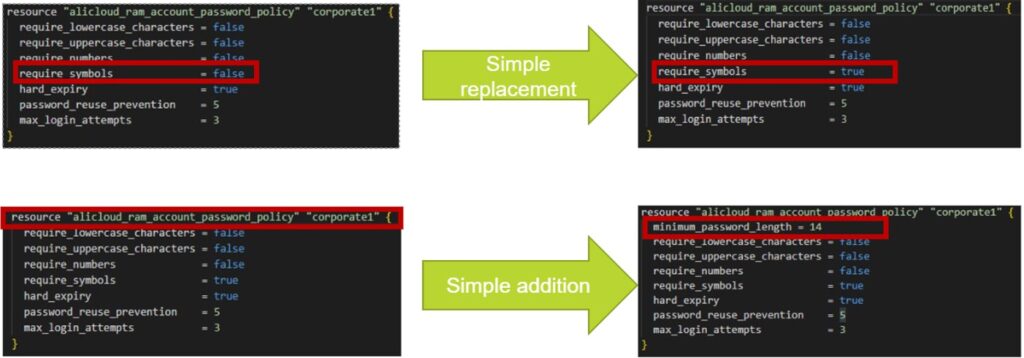
If you happen to’re not utilizing VS Code as your IDE or don’t wish to set up the plugin, you possibly can leverage auto-remediation inside KICS itself for easy replacements and additions in a single line.
Step one is to scan your undertaking/file and generate a JSON report.
Instance:
docker run -v /house/cosmicgirl/:/path/ kics scan -p /path/pattern.tf -i “41a38329-d81b-4be4-aef4-55b2615d3282,a9dfec39-a740-4105-bbd6-721ba163c053,2bb13841-7575-439e-8e0a-cccd9ede2fa8” –no-progress -o /path/outcomes –report-formats json
If KICS gives a remediation for a outcome, it would outline the fields remediation and remediation_type. Right here’s an instance:
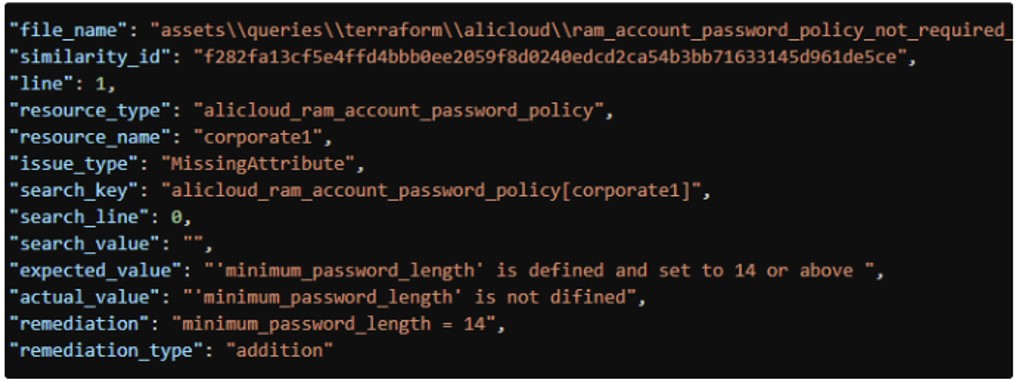
In case your JSON report has any outcome with remediation, run the brand new KICS command: remediate. To permit KICS to remediate all reported points, merely run:
docker run -v /house/cosmicgirl/:/path/ kics remediate –outcomes /path/outcomes/outcomes.json -v
To specify which remediation KICS ought to repair, you should use the flag –include-ids. On this flag, it is best to level to the similarity_id of the outcome. For instance:
docker run -v /house/cosmicgirl/:/path/ kics remediate –outcomes /path/outcomes/outcomes.json –include-ids “f282fa13cf5e4ffd4bbb0ee2059f8d0240edcd2ca54b3bb71633145d961de5ce” -v
Have you ever downloaded KICS but? You may do this proper right here. Need extra KICS suggestions and methods? Try these different sources: