Bogus installers for Adobe Acrobat Reader are getting used to distribute a brand new multi-functional malware dubbed Byakugan.
The start line of the assault is a PDF file written in Portuguese that, when opened, exhibits a blurred picture and asks the sufferer to click on on a hyperlink to obtain the Reader software to view the content material.
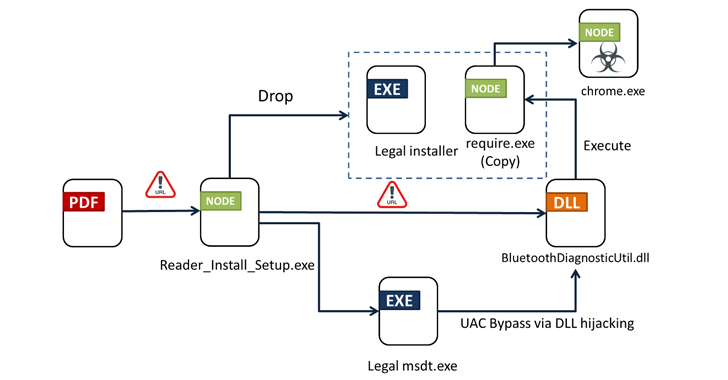
Based on Fortinet FortiGuard Labs, clicking the URL results in the supply of an installer (“Reader_Install_Setup.exe”) that prompts the an infection sequence. Particulars of the marketing campaign have been first disclosed by the AhnLab Safety Intelligence Middle (ASEC) final month.
The assault chain leverages strategies like DLL hijacking and Home windows Consumer Entry Management (UAC) bypass to load a malicious dynamic-link library (DLL) file named “BluetoothDiagnosticUtil.dll,” which, in flip, hundreds unleashes the ultimate payload. It additionally deploys a respectable installer for a PDF reader like Wondershare PDFelement.
The binary is provided to assemble and exfiltrate system metadata to a command-and-control (C2) server and drop the primary module (“chrome.exe”) from a distinct server that additionally acts as its C2 for receiving recordsdata and instructions.
“Byakugan is a node.js-based malware packed into its executable by pkg,” safety researcher Pei Han Liao stated. “In addition to the main script, there are several libraries corresponding to features.”
This consists of establishing persistence, monitoring the sufferer’s desktop utilizing OBS Studio, capturing screenshots, downloading cryptocurrency miners, logging keystrokes, enumerating and importing recordsdata, and grabbing information saved in net browsers.
“There is a growing trend to use both clean and malicious components in malware, and Byakugan is no exception,” Fortinet stated. “This approach increases the amount of noise generated during analysis, making accurate detections more difficult.”
The disclosure comes as ASEC revealed a brand new marketing campaign that propagates the Rhadamanthys info stealer underneath the guise of an installer for groupware.
“The threat actor created a fake website to resemble the original website and exposed the site to the users using the ad feature in search engines,” the South Korean cybersecurity agency stated. “The malware in distribution uses the indirect syscall technique to hide from the eyes of security solutions.”
It additionally follows a discovery {that a} manipulated model of Notepad++ is being employed by unidentified risk actors to propagate the WikiLoader malware (aka WailingCrab).