After a yr of cyber assaults making headlines worldwide, many organizations, comparable to MGM Resorts, Clorox, and T-Cell, have taken a reputational hit much like SolarWinds. Sysdig’s 2024 Cloud-Native Safety and Utilization Report supplied some informative key takeaways that CISOs can hone in on to enhance their safety posture. As a CISO, you do not need to catch your group on that record; mitigating reputational threat is part of your job.
This seventh-annual report relies on real-world knowledge. It isn’t skewed by opinions, so it offers factual info relating to the present state of cloud safety. As such, this weblog highlights just a few of the important thing takeaways from the report and offers ideas for safety threat discount measures that you would be able to implement instantly in your group. Critically, we aren’t maintaining tempo with the pace of our adversaries, and we have to up our recreation. Stay by this mantra as you stage up your cybersecurity posture over the subsequent a number of months.
Come to phrases with assault, response, and disclosure speeds
Are you aware how shortly the workloads that energy your purposes stay and die? 70% of containers stay for five minutes or much less. Trying via rose-colored lenses, this implies an attacker solely has 5 minutes to make their transfer laterally in the event that they enter via a susceptible container earlier than it dies and they’re booted out. Sadly, although, they know they’ll get one other probability in the event that they fail the primary time. If the attacker is profitable in shifting previous that container in 5 minutes, your safety workforce could miss out not solely on fast containment but additionally on amassing that forensic knowledge for incident response actions.
So how do you counteract the idea of short-lived workloads being no match for the pace of cloud assaults? First, prioritize mitigation of vulnerabilities in use at runtime. Don’t go away recognized vulnerabilities open and out there to attackers! The report signifies that during the last yr, runtime prioritization has decreased important and excessive vulnerabilities in use by almost 50%. This prioritization reduces the alternatives an attacker has within the first place by closing open doorways. Repair what issues most in your group’s surroundings, not what others may deem crucial.
- Prioritize vulnerabilities working in your surroundings, particularly these which can be being actively exploited, which could possibly be discovered on CISA’s web site. Addressing vulnerabilities that aren’t in your manufacturing surroundings wastes valuable time that could possibly be spent on those who really put your group in danger, and vulnerabilities with out an lively exploit are much less dangerous than these which can be being exploited by dangerous guys.
- When there’s a new important, exploitable vulnerability within the wild, and it’s everywhere in the information, and there are CISA and FBI alerts, don’t panic. Oftentimes safety leaders will overreact after studying the information, and it seems that the susceptible device, picture, no matter it could be, is nowhere in your surroundings. At this level, rely your blessings and ignore the media frenzy. If it does affect you, comply with steering, and your safety workforce and builders ought to know what to do.
Subsequent, you might want to have sturdy real-time detection of potential attacker behaviors. An attacker could be in and shifting in 5 minutes, lower than the period of time it most likely takes to complete your first cup of espresso or learn your emails in the beginning of the day. The one strategy to fight that is to act on an alert as quickly because the attacker makes their first transfer.
Within the 2023 International Cloud Menace Report and thru Sysdig’s 5/5/5 Benchmark, the Sysdig Menace Analysis Workforce (TRT) supplied a number of examples of cloud assaults going from zero to cryptominer, knowledge exfiltration, or worse in a median of 10 minutes thanks, partially, to using automation. This benchmark units an aspiration and affords prescriptive suggestions in your safety program to operationalize with respect to detection, knowledge correlation, and response. Problem your safety groups to work towards a clock by utilizing a cloud assault the place time is of the essence, comparable to ransomware or a SCARLETEEL assault. It will offer you a baseline with which you need to use to change instruments, purposes, and processes to enhance your detection and response occasions.

- Take just a few hours (I hope it doesn’t take any longer) and run a tabletop train together with your safety workforce in actual time. Get all palms on deck and have your crimson workforce or a 3rd social gathering provoke an assault. This could provide you with a place to begin for streamlining your safety processes. Use the train to validate your preparedness to detect and reply to extremely automated assaults.
When safety incidents occur, speedy detection and response come in useful on the board stage too. With the quick timelines set forth by regulatory disclosure necessities, such because the SEC’s 4 enterprise days for materials incidents, CIRCIA’s 72-hour requirement to report back to CISA, or EU NIS2’s detect inside 24 hours and disclose inside 72 hours, the earlier you’ve an understanding of the incident, the higher.
Overview and validate these timescales together with your workforce. Ask your workforce the place they suppose automation could be launched into the detect and reply processes.
- Take into account automating safety processes at this level. Notice that I stated automation and never AI (although this isn’t a nasty use case for an LLM both). Take into account automating a number of the knowledge correlation processes so groups can soar proper to knowledge evaluation. Automate response actions. If responses are usually not already automated, work together with your workforce to find out the place automation could be carried out. Drift management is a good instance of an automatic safety response in which you’ll be able to shut down workloads which can be modified throughout runtime. You’ll be able to learn extra about this within the full report.
Reel in your permissions
Identification administration is a bane for many CISOs and safety groups. Assaults usually start with both an exploited vulnerability or an identification situation. Even exploited vulnerabilities nonetheless contain identification in some trend, as attackers use account entry and privileges to collect knowledge and transfer via the community. The report famous that 98% of account permissions go unused. That’s far an excessive amount of pointless threat.
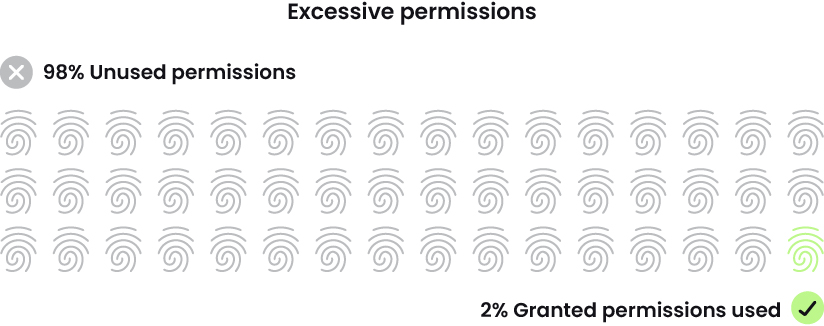
This yr’s utilization report additionally famous that solely 20% of our prospects are utilizing our Cloud Infrastructure Entitlement Administration (CIEM) weekly. They could possibly be utilizing a distinct CIEM, however that also doesn’t clarify the speed of extreme permissions.
- Determine the place your group stands with permission opinions. Is your group reviewing permissions on a weekly, month-to-month, quarterly, or annual foundation? Is there an ordinary in your group for the way these opinions are performed? If not, think about implementing an identification administration evaluate course of to reduce overly permissive human and machine identities.
Frankly, I’d wish to say there isn’t any excuse for this lack of consideration, particularly in the case of machine (nonhuman) identities. Nevertheless, as a consequence of its technical complexity, it’s fairly obscure each permission a human person or machine wants at a given second primarily based on their positions, initiatives, and regular behaviors. The report said that some machine customers have 1000’s of unused and untouched permissions, primarily offering a free-for-all to the attacker who can entry that identification. The truth that the numbers are so astronomical speaks to how tough the issue is. There are approaches, nonetheless, that assist handle this complicated problem.
- Have conversations together with your employees relating to the standing of identification administration in your group. Decide what the cadence is for permission opinions and determine if present practices adequately scale back threat.
- Take and implement the steering of reviewing nonhuman permissions upon preliminary provisioning and constantly afterward, following your set cadence.
- If these conversations have occurred and your granted permissions are nonetheless working rampant, decide why and the place communication is breaking down, and in case your transparency is missing. Safety groups could very properly be overloaded or just lack sufficient tooling or processes to help acceptable entry controls.
- Decide and implement permission parameters. These may embody customers with particular job titles or on sure initiatives and timeline limitations, comparable to permission elimination following no use for 90 days (think about using 60- or 30-day parameters for high-risk identities). These parameters could be automated, however ought to nonetheless be a part of common opinions.
Velocity helps enterprise, comfort hurts safety
Are you aware the place your utility packages come from or how they’re saved? The report states {that a} majority of organizations (66%) depend on public sources for his or her pictures. These sources could also be assumed both to be fairly secure as a consequence of the place they got here from or scanned as soon as and thought of vetted from that time ahead.
Sure, this use of public pictures is cheaper as a result of you aren’t paying for vendor-managed providers or dedicating workers and time to personal registry upkeep. It’s, nonetheless, necessary to acknowledge that these public registries include decreased safety management enforcement (it’s out of your group’s palms) and subsequently go away you susceptible to software program provide chain threat. In case you are utilizing public sources, ensure they’re being scanned usually and persistently at a tempo that your group deems manageable. Keep in mind, you shouldn’t depend on an open-source entity to handle scanning and remediation.
- Think about using automated tooling known as software program composition evaluation (SCA) to determine and analyze your open-source software program and generate software program payments of supplies (SBOMs) in your purposes.
- As recommended earlier, prioritize your vulnerabilities and dangers and remediate them accordingly to scale back assault dangers. Give attention to known-exploited vulnerabilities and those who affect your workloads at runtime.
One other space the place comfort could trump safety is in your useful resource constraints. Sadly, many organizations don’t set most limits or obtain alerts on CPU and reminiscence use. That is what attackers are relying on after they drop cryptominers in your surroundings and make you pay for his or her useful resource consumption. There’s an opinion that limits hinder growth and productiveness, so limitless sources equals quicker enterprise operations and subsequently extra revenue. Nevertheless, that revenue shall be diminished if it’s permitting cryptominers to make use of the sources you’re paying for.
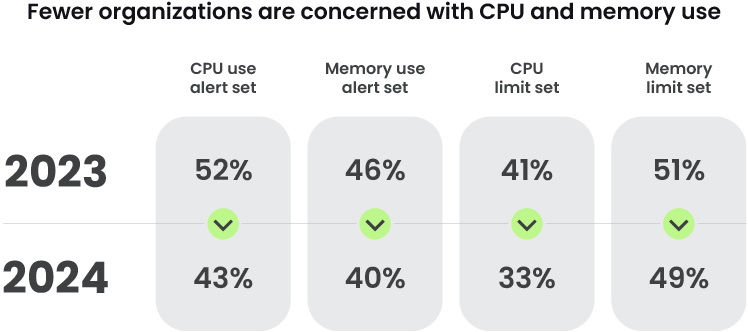
- Implement useful resource limits and activate alerts for useful resource consumption to set off at 80% (or no matter you deem acceptable), revisiting the boundaries as essential.
- Set up a capability plan and guarantee availability by implementing useful resource parameters for particular workloads, initiatives, and so on. to make sure built-in resiliency within the case of an incident. For instance, compartmentalize surroundings’s or workload’s limits and, between two of them, set every restrict to 40% in order that if one facet fails or have to be pulled down, the opposite facet can assume the workload with further headroom.
Conclusion
The best CISO cloud safety takeaway from Sysdig’s latest report is that organizations routinely place operations and expediency forward of governance and safety. This can lead to unanticipated dangers and is, frankly, avoidable.
Safety should function on the pace of enterprise to mitigate dangers, and for CISOs, maintaining tempo with the enterprise is a high precedence. Time-sensitive disclosure necessities (suppose the latest SEC guidelines) and high-profile breaches now have govt and board-level consideration. CISOs want to repeatedly consider how well timed they’ll detect and reply to dangers. To function on the pace of the enterprise, CISOs and their groups should be laser-focused on telemetry and automation.
As a CISO, it’s your accountability to convey safety into the enterprise irrespective of how a lot others could push again. You need to be certain that your safety actions are aligned with the enterprise, so it’s in your greatest curiosity to spend time with your small business colleagues to raised perceive their priorities and initiatives so you’ll be able to work to make sure that your safety initiatives are aligned accordingly.
Capturing and mitigating dangers early reduces the danger of distractions which can undermine company values. Remind others of the large breaches within the information, comparable to SolarWinds, T-Cell, and Equifax. Does your CEO or CFO need to find yourself like them? The reply is probably going “no,” So it’s as much as your workforce to start out placing safety on the forefront of enterprise and to take motion.
