2023 culminated with an intensified wave of assaults on the software program provide chain. Listed below are just some that our Software program Provide Chain Analysis Workforce helped expose within the month of December alone:
- North Korea used public open-source and personal package deal poisoning through the GitHub platform to infiltrate organizations and compromise their software program provide chains (report)
- Attackers revealed malicious packages to PyPl, utilizing varied ways, together with combining obfuscation with encryption/decryption strategies to cover their malicious intent, using fileless malware to keep away from detection, and leveraging the status of an especially fashionable challenge (report)
- The Ledger Join Package suffered a big provide chain assault ensuing within the theft of over $700,000 from customers’ wallets. The assault was facilitated by the takeover of a former Ledger worker’s npmjs account, which led to the discharge of compromised variations. This incident highlights the restrictions of relying solely on Software program Invoice of Supplies (SBOMs) to detect such assaults. (report)
All of us hoped the beginning of a brand new 12 months would convey new tidings. Sadly, NPM consumer account gdi2290, aka PatrickJS, revealed a troll marketing campaign to the NPM registry by importing a package deal named “everything,” which depends on each different public NPM package deal, leading to hundreds of thousands of transitive dependencies. (report).
Jerry Gamblin, vulnerability researcher at Cisco, lately identified on LinkedIn that for the primary time ever we have now hit over 30,000 CVE’s revealed in a single 12 months.
These developments, among the many many others that preceded, emphasize the restricted capability of conventional safety measures and the necessity for complementing them with superior and dynamic approaches.
4 classes realized in 2023
- Attackers are ingeniously stitching collectively numerous ways.
- Misleading maneuvers, exemplified by social engineering and bogus contributions, have grow to be a staple in attackers’ arsenals.
- Deserted digital belongings will not be relics of the previous; they’re ticking time bombs.
- The risk panorama’s relentless evolution emphasizes the significance of predictive risk looking.
NSA’s beneficial practices for securing the software program provide chain
December was additionally a month for renewed steerage from the US Authorities. The Nationwide Safety Company (NSA), Workplace of the Director of Nationwide Intelligence (ODNI), the Cybersecurity and Infrastructure Safety Company (CISA), and business companions have launched a cybersecurity technical report (CTR), “Securing the Software Supply Chain: Recommended Practices for Managing Open Source Software and Software Bill of Materials,” which builds on the “Enhancing the Security of the Software Supply Chain through Secure Software Development Practices” paper launched by the Workplace of Administration and Price range (OMB).
Even with this in-depth steerage, most prospects we discuss to are underneath the belief that having a well-defined SBOM (Software program Invoice of Supplies) is the one tangible method to a software program provide chain safety technique.
Checkmarx’ end-to-end software program provide chain safety to facilitate SLSA attestation
Our imaginative and prescient is to convey collectively the concept of understanding what goes by the method, equivalent to dependencies and software program artifacts, with the event atmosphere itself, all underneath the Provide-chain Ranges for Software program Artifacts (SLSA) framework. This primary-to-market method creates true visibility past what an SBOM can supply and helps get nearer to offering attestation for SLSA compliance.
Stopping secrets and techniques from leaking on exterior instruments with Secrets and techniques Detection
Secrets and techniques, equivalent to passwords, API keys, cryptographic keys, and different confidential knowledge, are a frequent goal of a distributed supply-chain assault.
Menace actors are mining for secrets and techniques by scrapping public documentation, public repositories, and compromised non-public software program repositories, and compromised construct techniques.
Every onerous coded secret is now a brand new assault vector.
Secret Detection will show you how to take away onerous coded passwords out of your software program provide chain by checking developer communication, shared instruments, and elements used throughout the availability chain.
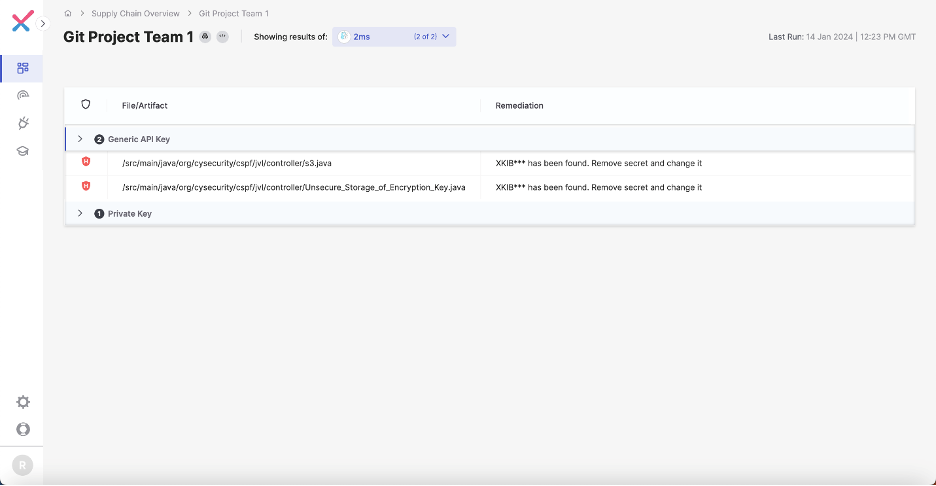
Secrets and techniques Detection integrates and expands deeper scanning capabilities of 2MS, one of the fashionable open-source instruments for secret detection with over 2 million downloads, immediately into Checkmarx One.
Expanded capabilities embrace:
- Help for Confluence, Slack and Discord
- The power to customizable guidelines and insurance policies
Making a streamlined degree of accountability with automated SBOM
SBOMs may be generated robotically immediately from the UI, in SPDX and CycloneDX codecs. This protects you time and a headache, and ensures you will have an up-to-date stock of third-party packages getting used inside your software program provide chain.
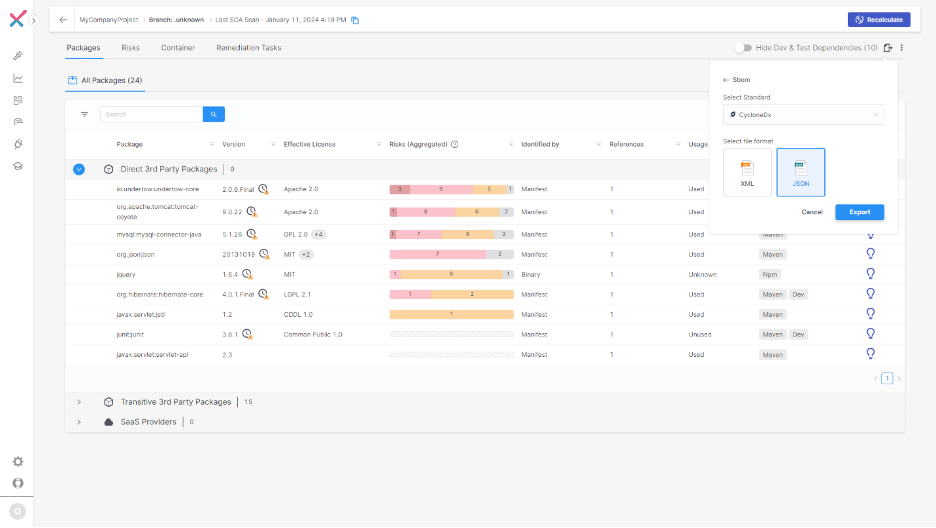
Since Checkmarx maintains a historic document of all scans carried out, we are able to retrieve a point-in-time SBOM from earlier scans or code checking occasions. This eliminates the necessity for us to construct preserve and again up a catalog of SBOM information in a file share, saving effort and time whereas making certain you may be compliant with historic SBOM requests.
Checkmarx helps a big selection of languages and package deal managers so there’s no must implement preserve or replace a number of SBOM options on a per challenge, or per language, degree.
Tackling probably the most weak inside initiatives first with Safety Scorecard Engine
Checkmarx Scorecard allows organizations to test their very own initiatives shortly and see probably the most weak or at-risk initiatives, permitting enterprises to prioritize which to sort out first.
Scorecard leverages the format from a preferred instrument, the OSSF Scorecard, which assesses open-source initiatives for safety dangers by a sequence of automated checks.
These checks cowl varied components of the software program provide chain together with supply code, construct, and dependencies, and assigns every test a rating of 1-10. An auto-generated “security score” helps customers as they determine the belief, threat, and safety posture for his or her particular utility.
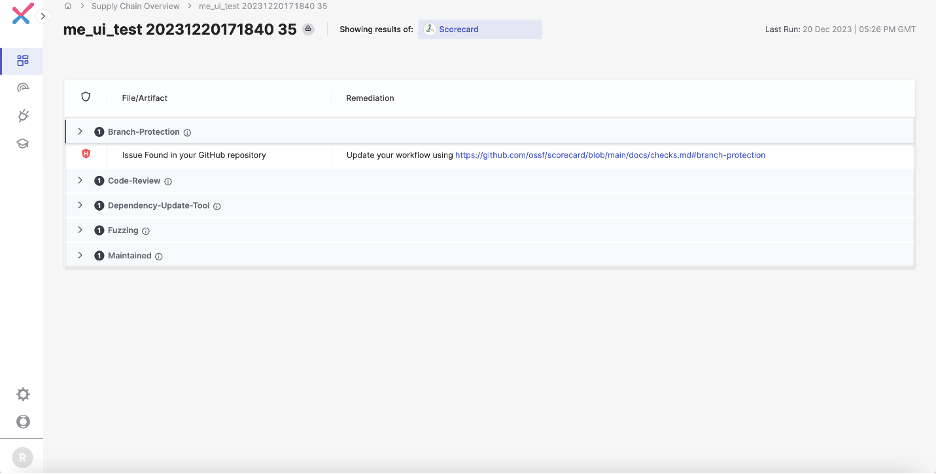
With Scorecard, customers can auto-generate a safety rating for their very own initiatives primarily based on a sequence of checks, together with:
- Binary Artifacts – Is the challenge freed from checked-in binaries?
- Department Safety – Does the challenge use department safety?
- CI (Steady Integration) Assessments – Does the challenge run assessments in CI, e.g., GitHub Actions, Prow?
- Code evaluate – Does the challenge observe code evaluate earlier than code is merged?
- Harmful workflow – Does the challenge keep away from harmful coding patterns?
- Vulnerabilities – Does the challenge have unfixed vulnerabilities?
Integrating new instruments is a frictionless, one-click integration. As soon as you choose a brand new instrument, it will get scanned, and the outcomes are displayed in a devoted view inside Checkmarx One.
Gaining risk intelligence and eliminating guide evaluation with Malware Detection
Within the SLSA framework, malicious packages are a type of dependency assault the place attackers inject or contribute malicious code into open-source initiatives that your builders obtain after which construct into your purposes. As soon as downloaded, the attacker’s malicious code is operating inside your purposes, with no matter unknown intent the package deal carries.
Our analysis workforce has inspected over 8 million open-source packages for all types of threats, discovering 200,000+ malicious packages. We make that risk intelligence obtainable to you, both within the UI, immediately in builders’ IDE, or by an API-based risk intelligence feed.
Securing containerized purposes all through the availability chain
Securing your containers is a key half in stopping third events from exploiting vulnerabilities that may result in the impairment of your infrastructure, knowledge leaks, and different sorts of assault. 87% of container pictures in manufacturing have important or high-severity vulnerabilities.
The Checkmarx Container Safety Resolution simplifies picture scanning, displays Docker environments, and helps swiftly resolve vulnerabilities. Determine, prioritize, and tackle safety flaws throughout the SDLC to preempt points in manufacturing workloads.
- Container Picture Scanning – Scan static container pictures to establish weak code in open-source software program and remediate points earlier than they’re deployed.
- Runtime Insights Correlation – Correlate pre-production and runtime knowledge to establish exploitable vulnerabilities in operating container pictures, scale back noise by as much as 95%, and prioritize remediation efforts.
Software program provide chain safety is a journey, and it is very important take steps to safe your software program provide chain at this time; detecting provide chain assaults in code packages, securing your developer’s evolving workstations helps speedy improvement whereas decreasing threat.