A gaggle of suspected Chinese language cyberespionage actors named ‘Velvet Ant’ are deploying customized malware on F5 BIG-IP home equipment to achieve a persistent connection to the inner community and steal knowledge.
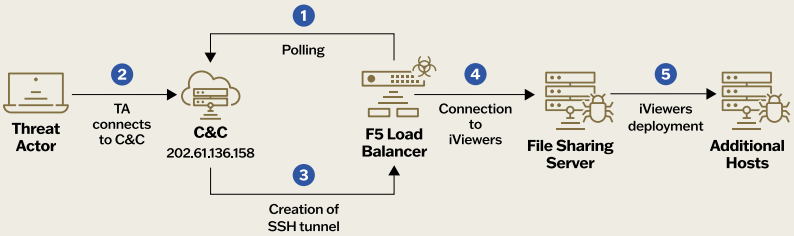
In keeping with a Sygnia report who found the intrusion after they have been known as in to analyze the cyberattack, Velvet Ant established a number of footholds utilizing varied entry factors throughout the community, together with a legacy F5 BIG-IP equipment that served as an inside command and management (C2) server.
Utilizing the compromised F5 BIG-IP gadgets, the menace actors may stealthily steal delicate buyer and monetary data from the corporate for 3 years with out being detected.
Utilizing F5 BIG-IP malware in assaults
The assault noticed by Sygnia began by compromising two outdated F5 BIG-IP home equipment the sufferer group used for firewall, WAF, load balancing, and native visitors administration.
Each home equipment have been uncovered on-line and have been working weak OS variations. Sygnia says they have been each compromised utilizing recognized distant code execution flaws to put in customized malware on the networking gadgets.
Subsequent, the attackers used this entry to achieve entry to inside file servers the place they deployed PlugX, a modular distant entry Trojan (RAT), which varied Chinese language hackers have been utilizing for knowledge assortment and exfiltration for over a decade now.
Different malware deployed on the F5 BIG-IP equipment contains:
- PMCD: Connects to the C&C server hourly, executes instructions obtained from the server through ‘csh’, sustaining distant management.
- MCDP: Captures community packets, executed with the ‘mgmt’ NIC argument, guaranteeing persistent community monitoring.
- SAMRID (EarthWorm): An open-source SOCKS proxy tunneler used for creating safe tunnels, beforehand utilized by varied Chinese language state-sponsored teams.
- ESRDE: Just like PMCD it makes use of ‘bash’ for command execution, permitting distant command management and persistence.
The attackers used the compromised F5 BIG-IP equipment to retain persistence on the community, permitting them to achieve entry to the inner community whereas mixing attacker visitors with legit community visitors, making detection tougher.
This methodology bypasses company firewalls and lifts outbound visitors restrictions, enabling attackers to steal buyer and monetary data with out elevating alarms for practically three years.
Supply: Sygnia
Sygnia reviews that regardless of in depth eradication efforts following the breach’s discovery, the hackers re-deployed PlugX with new configurations to keep away from detection, utilizing compromised inside gadgets just like the F5 home equipment to retain entry.
Protection suggestions
Counteracting refined and chronic menace teams like Velvet Ant requires a multi-layered and holistic safety method.
Sygnia recommends the next measures to detect assaults like these:
- Limit outbound connections to attenuate C&C communications.
- Implement strict controls over administration ports and improve community segmentation.
- Prioritize changing legacy methods and tightening safety controls.
- Deploy sturdy EDR methods with anti-tampering options and allow safety measures like Home windows Credential Guard.
- Improve safety for edge gadgets by way of patch administration, intrusion detection, and migration to cloud-based options.
As edge community gadgets don’t generally assist safety options and are supposed to be uncovered to the web, they’ve develop into well-liked targets for menace actors to achieve preliminary entry to a community.
In 2023, China-linked hackers exploited Fortinet zero-days to put in a customized implant to steal knowledge and pivot to VMWare ESXi and vCenter servers.
Weeks later, a suspected Chinese language hacking marketing campaign focused unpatched SonicWall Safe Cell Entry (SMA) home equipment to put in customized malware.
In April 2023, the US and UK warned that the Russian state-sponsored APT28 hackers have been deploying a customized malware named ‘Jaguar Tooth’ on Cisco IOS routers.
In Might 2023, Barracuda ESG gadgets have been exploited for seven months to deploy customized malware and steal knowledge. The compromise on these gadgets was so pervasive that Barracuda beneficial that firms substitute breached gadgets fairly than attempt to restore them.
Extra not too long ago, suspected state-sponsored menace actors exploited a Palo Alto Networks zero-day to put in a customized backdoor to breach inside networks and steal knowledge and credentials.
