A Story of Collaboration
Working Collectively To Preserve Open Supply Secure
Initially of 2023, prime researchers from industry-leading firms established the Provide Chain Assault Analysis (SCAR) group. To remain one step forward of this fixed race in opposition to malicious actors, the group agreed there was a must foster collaboration amongst specialists, outline environment friendly requirements, develop instruments to profit the worldwide group, and promote joint analysis and knowledge sharing.
Karine Ben-Simhon, VP of Buyer Advocacy at Trellix Superior Analysis Middle is among the founders of the SCAR discussion board. Whereas working at Citi’s Cyber Security Innovation Lab, she launched the SCAR discussion board with a robust emphasis on its cross-industry nature.
Determine 1: Provide chain safety by way of collaboration
Open Supply and Packages
90% of organizations use open-source sources, since they’re a good way for organizations to rapidly create and ship software program. Nonetheless, Third-party open supply dependencies additionally include inherent dangers. Open-source software program libraries (additionally known as packages) are printed to a number of internet hosting ecosystems, equivalent to NPM, PyPi, and GitHub, simply to call a number of.
There’s a dissonance between the amount of accessible open-source instruments that many organizations make the most of for code growth, whether or not they’re startups or massive entities that depend on open-source code or third-party elements utilizing open-source code, and the obtainable instruments to vet these packages. This results in a dependency which opens a large and fertile realm for menace actors to function in and leverage to get entry to organizations’ networks.

Determine 2: Software program developer shopping the online to obtain an open-source NPM bundle
Vulnerabilities and Malicious Code
Vulnerabilities are one of many many dangers of utilizing open-source code. Whereas vulnerabilities are often not purposely inserted by the authors, the potential exploitation could also be important (equivalent to Log4j RCE important vulnerability).
However, malicious code is totally different. Attackers publish malicious open-source packages that disguise themselves as reputable for builders and comprise dangerous code silently deployed on builders’ workstations, construct programs, manufacturing servers, and even end-consumers, equivalent to This marketing campaign of 900+ malicious typosquatting packages or These malicious packages dropping undetectable refined malware, and lots of extra.
Not Initially Designed for Safety
It’s simple to eat open-source packages, and for creators, even simpler to publish new content material to these open-source ecosystems. All a writer wants are an electronic mail deal with, and an open and distinctive bundle title. Creators can assign it to themselves and embrace any code below that title in a matter of seconds.
There’s nearly no vetting in any respect of the content material being printed to such open-source ecosystems. For instance, attackers benefit from the Starjacking assault method to offer an look of legitimacy to their packages, luring builders or end-users right into a lure that might not be significantly refined.
How Builders Select Open Supply
Let’s think about we’re software program builders. We have been assigned a brand new job so as to add a brand new characteristic to an present NPM challenge. As we attempt to arrange the environment, we’re getting the next error message:
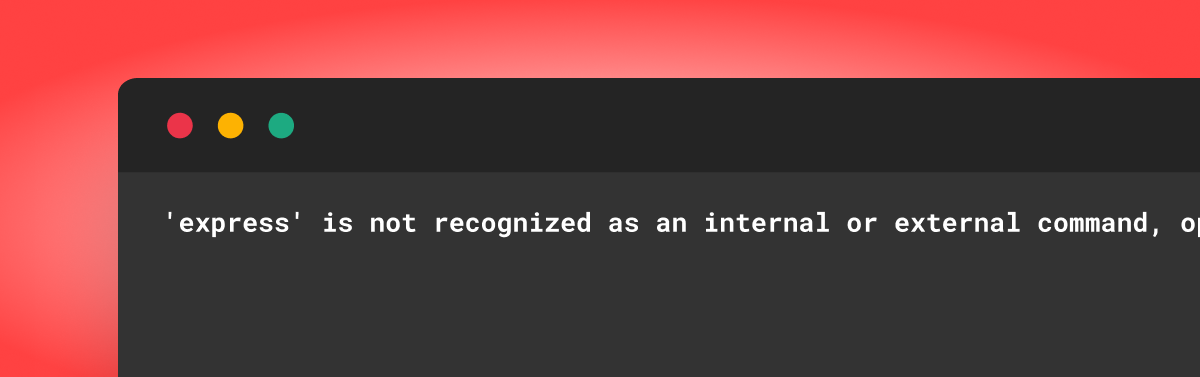
Determine 3: A screenshot of the error message when establishing new atmosphere
Drawback? “Google It”
Some builders making an attempt to unravel the problem might seek for an answer by way of search engines like google. Merely copying & pasting the error message right into a search engine affords some attention-grabbing, and related, results in an answer for a typical drawback.
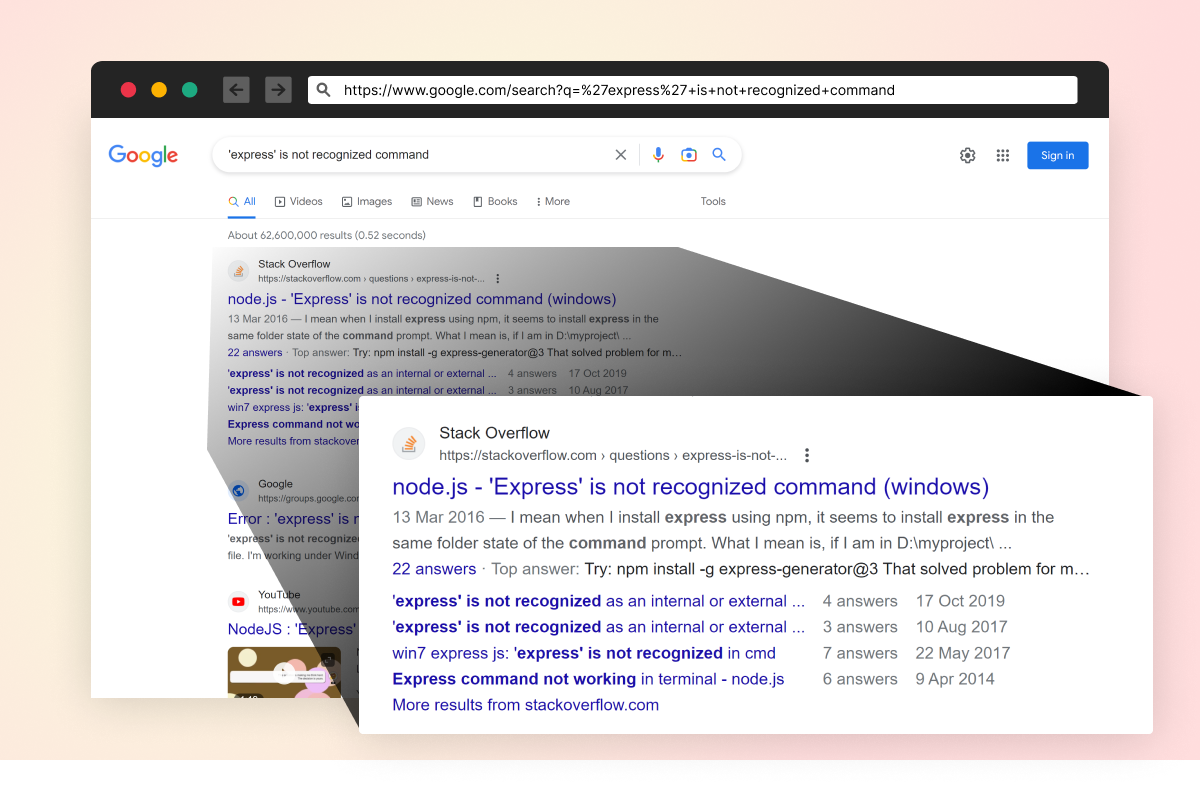
Determine 4: A screenshot of looking out the error in Google Search engine
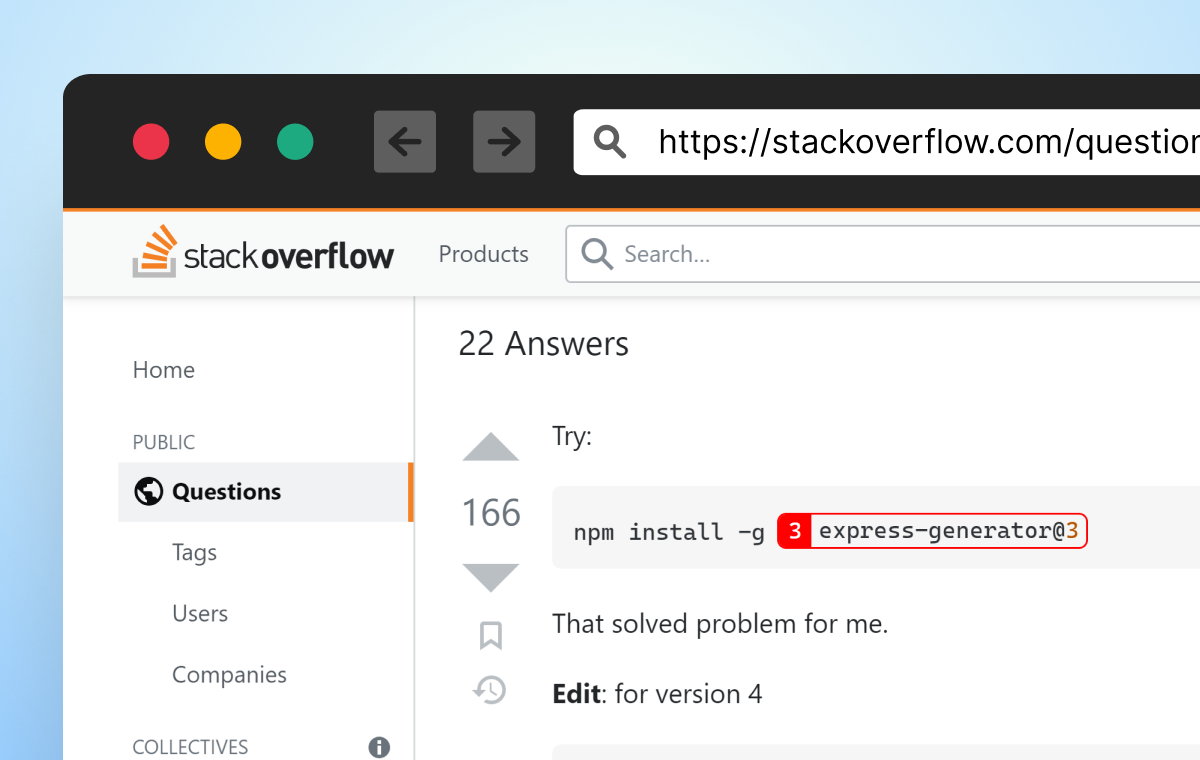
The highest result’s a StackOverflow thread that appears promising. Many solutions merely recommend putting in the express-generator bundle, with out rationalization. Nonetheless, simply because folks say it’s OK, it truly is?
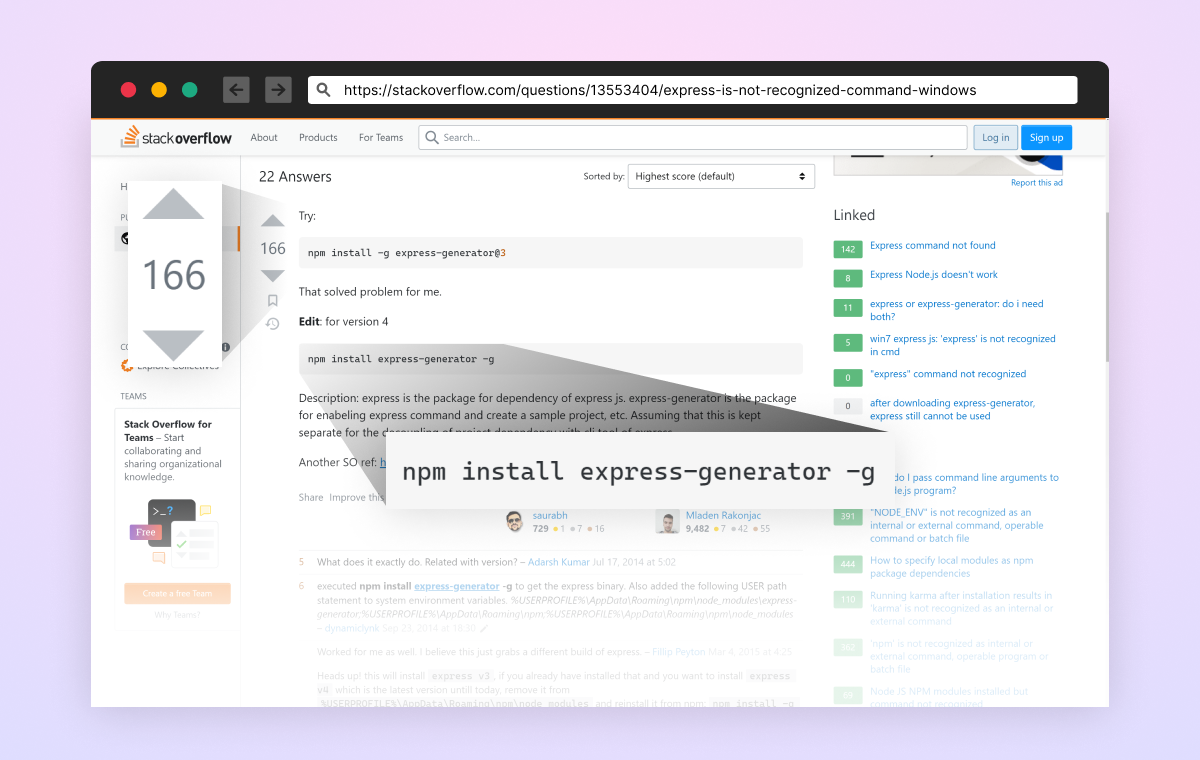
Determine 5: Screenshot from a preferred Stack Overflow reply, recommending utilizing express-generator npm bundle
The Troubleshooting Circle
Many builders who run into comparable solutions recommending putting in an open-source bundle would go forward and set up it on their native machine, by merely copying & pasting the steered set up command and executing it on their native growth environments.
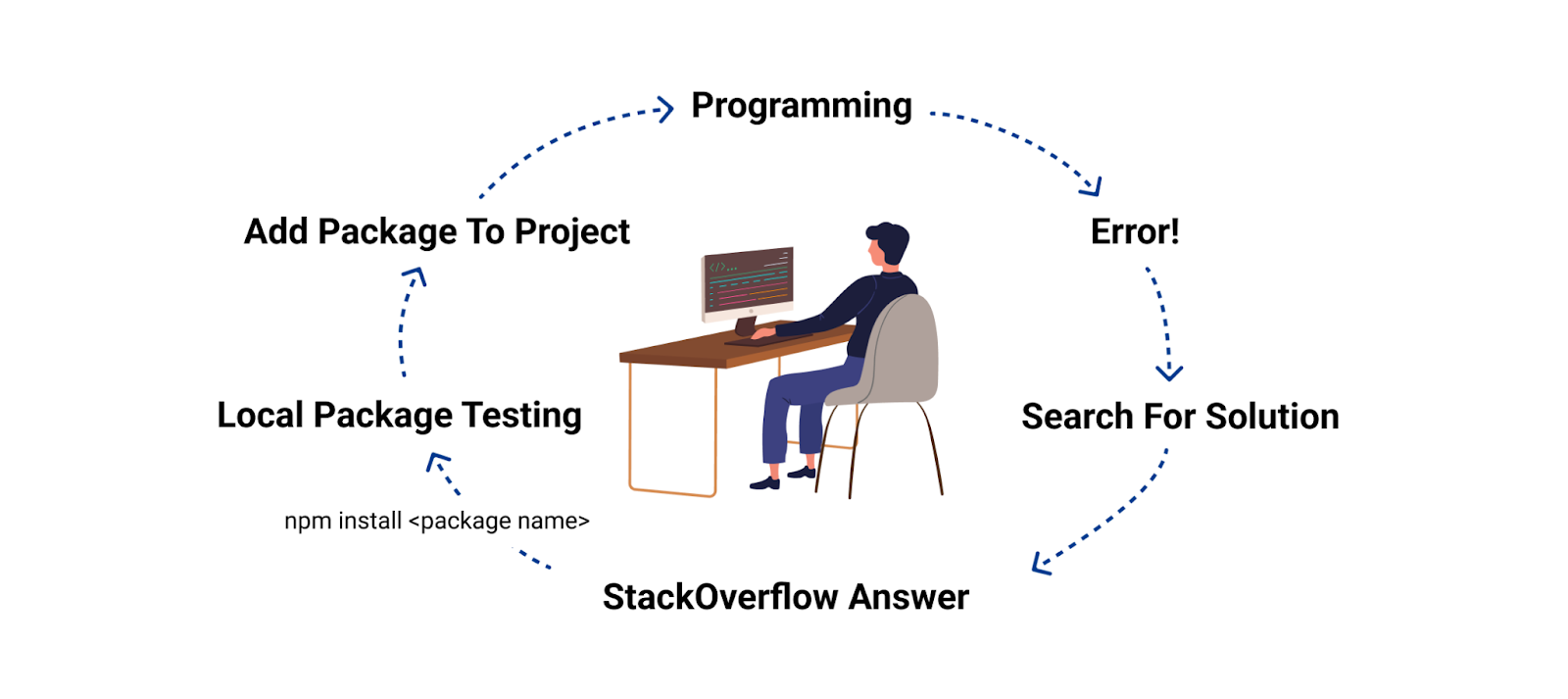
Determine 6: The troubleshooting circle
Evaluating Open-Supply Packages
Ought to builders be liable for safety? Sure. With nice energy comes nice accountability, and builders are liable for evaluating open-source packages earlier than utilizing them.
There are a number of parameters builders ought to verify earlier than putting in an open-source bundle. Some builders may concentrate on the license, others could also be extra fascinated by avoiding abandonware and specializing in maintained tasks, and others might keep away from tasks with unresolved safety points.
This vital step of a developer investing time in evaluating an open supply often contains handbook labor in evaluating the associated supply code repository with the precise bundle content material, reviewing the bundle contributors, viewing the challenge’s reputation and adoption, upkeep metrics equivalent to how briskly points are resolved, and extra.
That is time-consuming, however fortunately there are nice instruments equivalent to Socket, Snyk Advisor, Scorecard, and Debricked, that present these companies. Every of those instruments are designed to help software program builders in understanding the construction and safety of accessible open-source packages. Builders might use them to judge the packages they think about putting in and make accountable choices.
Sadly, though these instruments are accessible, not all builders possess an consciousness of their existence or incorporate them into their each day inner workflows.
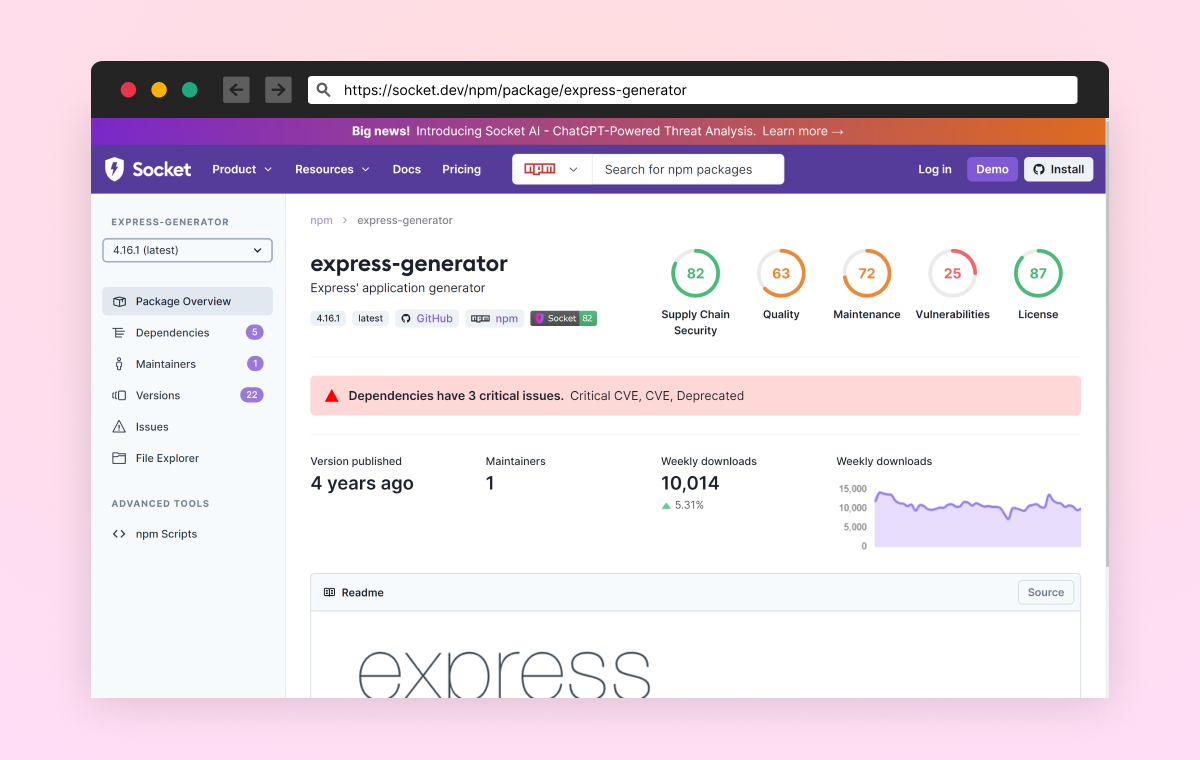
Determine 7: A screenshot of socket.dev, displaying the bundle report of the express-generator bundle
Builders often won’t exit of their analysis move to investigate the bundle safety degree, and there’s a low probability that builders will spend money on an analysis course of each time they’re contemplating a brand new bundle. Not as a result of they don’t care, however as a result of they don’t seem to be conscious of the threats, they don’t seem to be security-oriented customers and, due to this fact, a simple goal for menace actors.
We assume some builders are merely not conscious of this vital step that must be defaulted in their analysis move, whereas others could also be unaware of these free instruments.
The Resolution: Overlay Browser Extension
To maintain the developer’s expertise as native and intuitive as attainable, whereas helping the developer in being conscious of such instruments and free info associated to open-source packages, software program provide chain leaders Checkmarx and Illustria, members of the SCAR discussion board, joined their analysis forces for the great and created Overlay – an open-source browser extension.
The extension detects references to open-source packages and provides hyperlinks to quite a few free instruments provided by {industry} leaders offering further info to assist builders assess the bundle’s legitimacy, which is essential for the developer’s analysis course of.
Determine 8: A screenshot from StackOverflow reply after Overlay is put in on the browser
Floating Shortcuts
With minimal intrusion, the browser extension offers a configurable tooltip displaying key factors from every report.
Moderately than manually typing, looking out, and discovering info associated to the candidate bundle, with Overlay, builders get a tooltip with fast hyperlinks to these trusted sources talked about above.
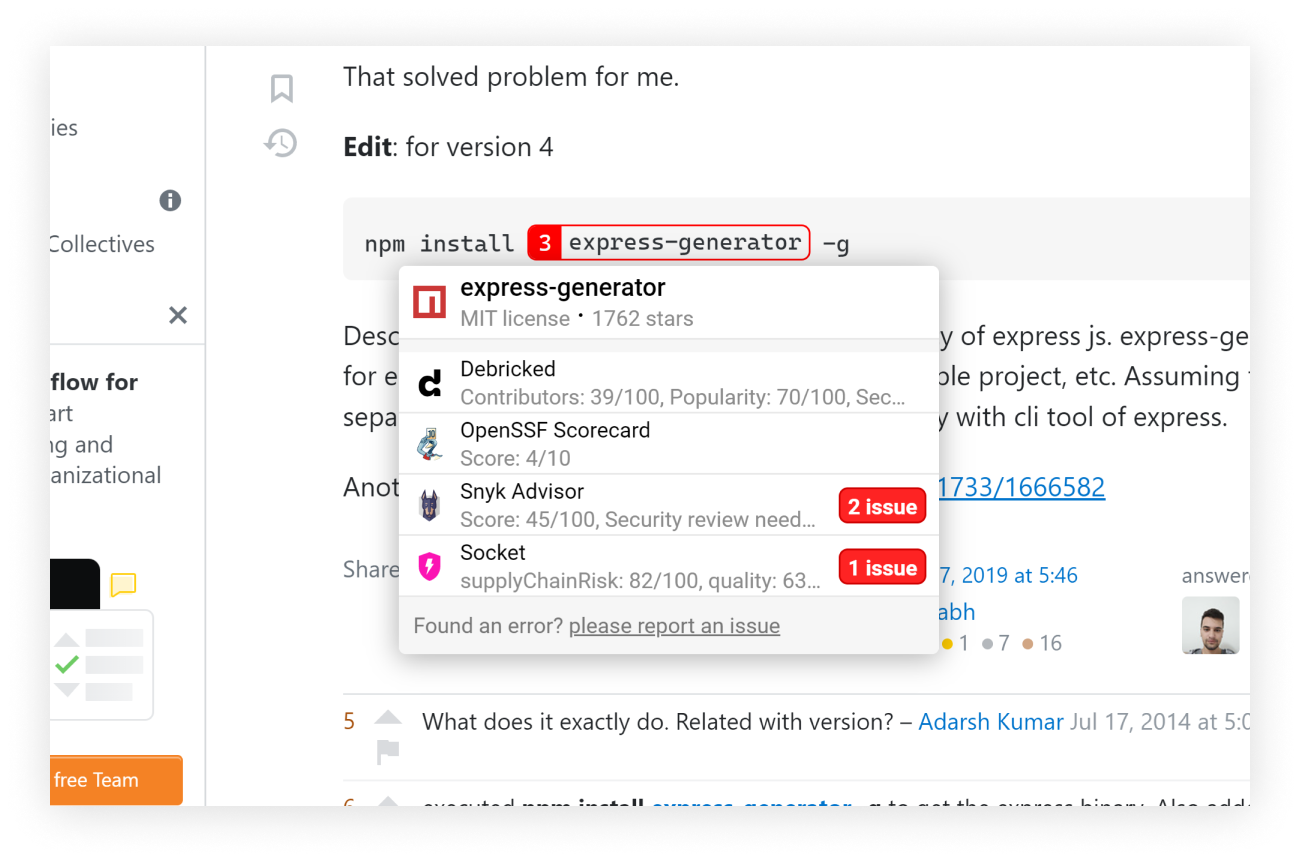
Determine 9: Screenshot from a preferred Stack Overflow reply with Overlay browser extension tooltip

Determine 10: A screenshot from the GitHub web page of Overlay https://github.com/os-scar/overlay
Abstract
Up to now, the Overlay challenge has obtained contributions from Checkmarx, Illustria, Vulcan, Maakaf, and extra particular person contributors. “Do not take code from strangers with out vetting,” suggested Baruch Odem, Senior Software program Engineer at Checkmarx and one of many main contributors to the Overlay challenge. This can be a nice instance of how distributors ought to collaborate regardless of being rivals and contribute again to the group.
The primary worth of Overlay is to supply builders an intuitive expertise whereas connecting them with safety advisories from respected sources and empowering builders with the mindset to take accountability for the code they intend to put in.
We encourage people and organizations of all scales, from startups to enterprises, to think about integrating Overlay into their workflow. We acknowledge that this course of might take time, and implementation depends upon the maturity of a company and different elements. We encourage builders to think about using Overlay even for private utilization.
Keep in mind that menace actors are aiming their focus previously few years on poisoning software program provide chain open-source dependencies and concentrating on builders and we have to work in collaboration as an {industry} in direction of a typical objective to not solely observe these malicious actions, share info and analysis, but additionally work collectively to create a safer open-source atmosphere.
