A year-long malware marketing campaign targets Roblox builders utilizing faux NPM packages mimicking “noblox.js” to steal knowledge. Regardless of takedowns, new threats proceed to emerge.
A persistent malware marketing campaign has been concentrating on Roblox builders by way of malicious NPM packages for over a yr, in line with a latest report from Checkmarx. The attackers have printed dozens of packages mimicking the favored “noblox.js” library, with the intention of stealing delicate knowledge and compromising programs.
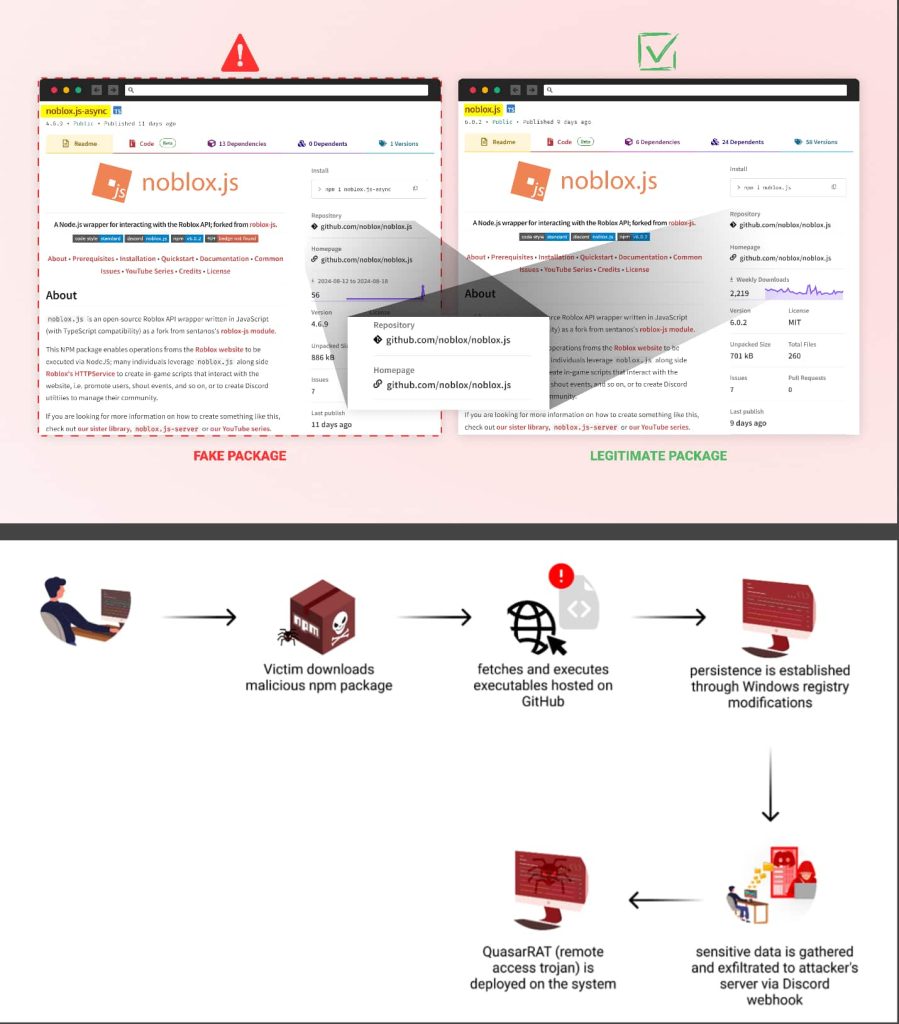
The marketing campaign, which started in August 2023, has continued regardless of a number of package deal takedowns, with new malicious packages nonetheless showing on the NPM registry on the time of publication. The attackers have used methods comparable to brandjacking, combosquatting, and starjacking to create a convincing look of legitimacy for his or her malicious packages.
The malware’s capabilities embrace Discord token theft, system data harvesting, system persistence, and the deployment of further payloads comparable to Quasar RAT. The malware additionally employs a classy persistence method by manipulating the Home windows registry, inflicting it to execute each time a consumer opens the Home windows Settings app.
Regardless of the removing of the recognized malicious packages from NPM, the attacker’s GitHub repository containing malicious executables stays lively, paving the best way for future assaults.
The attackers have used a classy strategy to craft an phantasm of authenticity round their malicious packages. They’ve mixed brandjacking and combosquatting, two strategies that fall below the broader class of typosquatting, to create the phantasm that their packages are both extensions of or carefully associated to the reputable “noblox.js” library.
The attackers have additionally used starjacking, a preferred methodology used to faux package deal stats. On this occasion, the malicious packages had been linked to the GitHub repository URL of the real “noblox.js” package deal, falsely inflating their perceived reputation and trustworthiness.
In keeping with Checkmarx’s report, the malware additionally employs techniques to disguise itself throughout the package deal itself. The attackers have meticulously mimicked the construction of the reputable “noblox.js” however launched their malicious code within the “postinstall.js” file. They’ve closely obfuscated this code, even together with nonsensical Chinese language characters to discourage simple evaluation.
The malicious code exploits NPM’s postinstall hook, guaranteeing automated execution when the package deal is put in. This hook is designed for reputable setup processes however turns into a gateway for operating the obfuscated malware with out the consumer’s information or consent.
The malware searches for Discord authentication tokens in a number of areas and validates them to make sure solely lively ones are exfiltrated. It additionally aggressively undermines the system’s safety measures, concentrating on Malwarebytes and Home windows Defender.
The malware expands its capabilities by downloading two further executables from the attacker’s GitHub repository. These recordsdata are then saved to the “C:WindowsApi” listing with randomized names, probably to assist the malicious recordsdata mix in with reputable system recordsdata.
To make sure long-term entry, the malware manipulates a Home windows registry key to make sure it runs persistently on the contaminated system. It additionally collects numerous kinds of delicate data from the contaminated system and sends it to the attacker’s command and management server utilizing a Discord webhook.
The ultimate stage entails deploying QuasarRAT, a distant entry software that provides the attacker intensive management over the contaminated system. The attacker maintains a second repository named “noblox-spoof”, which seems to deal with the most recent malicious npm package deal content material, instantly referencing the goal of this marketing campaign.
The latest malicious packages impersonating the favored noblox.js library have been taken down after being reported to npm’s safety staff. Nonetheless, the menace will not be fully neutralized, and the attacker’s continued infrastructure presence and persistence pose an ongoing menace.
Builders are strongly suggested to stay vigilant, verifying the authenticity of packages, particularly these resembling widespread libraries like noblox.js, to guard themselves and their customers from such refined provide chain assaults.
RELATED TOPICS
- Trojanized jQuery Infiltrates npm, GitHub, and CDNs
- Roblox Information Breach: PII of Hundreds of Builders Stolen
- Luna Grabber Malware Hits Roblox Devs Via npm Packages
- Faux ROBLOX, Nintendo recreation cracks drop ChromeLoader malware
- Protestware Makes use of npm Packages to Name for Peace in Gaza, Ukraine