The Chinese language Winnti hacking group is utilizing a brand new PHP backdoor named ‘Glutton’ in assaults on organizations in China and the U.S., and in addition in assaults on different cybercriminals.
Chinese language safety agency QAX’s XLab found the brand new PHP malware in late April 2024, however proof of its deployment, together with different recordsdata, dates again to December 2023.
XLab feedback that, whereas Glutton is a sophisticated backdoor, it has notable weaknesses in stealth and encryption, which is perhaps a sign that it is in an early growth part.
Winnti, often known as APT41, is a infamous Chinese language state-sponsored hacking group recognized for cyberespionage and monetary theft campaigns.
Since its look on the scene in 2012, the group has focused organizations within the gaming, prescription drugs, and telecommunications industries, whereas it has additionally attacked political organizations and authorities companies.
New Glutton backdoor
Glutton is an ELF-based modular backdoor that gives flexibility and stealth to the Winnti hackers, permitting them to activate particular parts for tailor-made assaults.
Its core parts are ‘task_loader,’ which determines the surroundings; ‘init_task,’ which installs the backdoor; ‘client_loader,’ which introduces obfuscation; and ‘client_task,’ which operates the PHP backdoor and communicates with the command-and-control (C2) server.
“These payloads are highly modular, capable of functioning independently or being executed sequentially via task_loader to form a comprehensive attack framework,” explains XLab.
“All code execution occurs within PHP or PHP-FPM (FastCGI) processes, ensuring no file payloads are left behind, thus achieving a stealthy footprint.”
The backdoor, which masquerades as a ‘php-fpm’ course of, facilitates fileless execution by dynamic in-memory execution and injects malicious code (‘l0ader_shell’) into PHP recordsdata on ThinkPHP, Yii, Laravel, and Dedecms frameworks.
Glutton modifies system recordsdata like ‘/and many others/init.d/community’ to ascertain persistence between reboots and can even modify Baota panel recordsdata to take care of foothold and steal credentials and configurations.
Other than Baota, the malware can even exfiltrate system info and information from the filesystem.
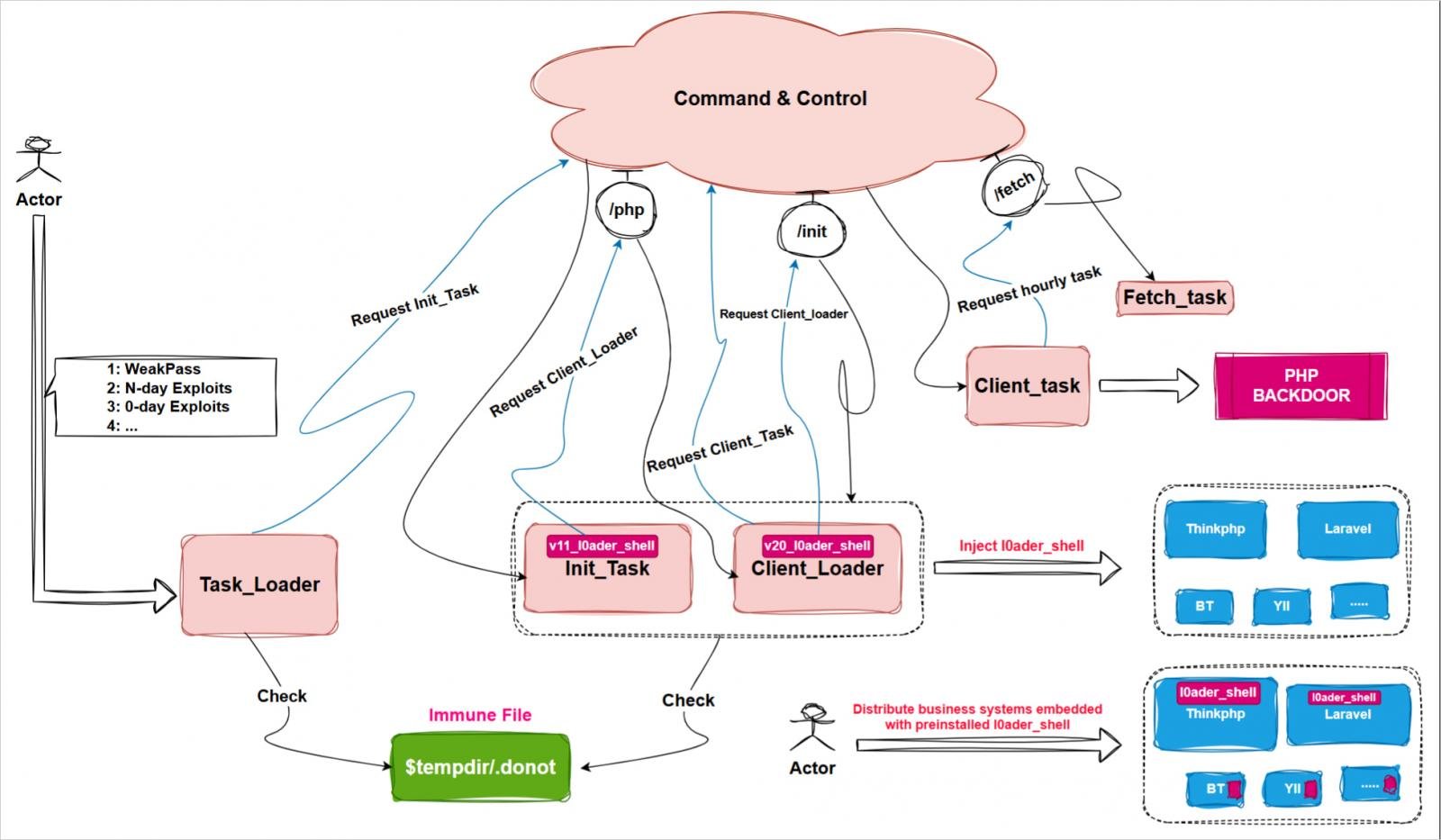
Supply: XLab
Glutton helps 22 instructions obtained from the C2 server, which order the next actions:
- Create, learn, write, delete, and modify recordsdata
- Execute shell instructions
- Consider PHP code
- Scan system directories
- Retrieve host metadata
- Change between TCP and UDP connections
- Replace the C2 configuration
Concentrating on different cybercriminals
XLab says Winnti has deployed Glutton on targets in China and the USA, primarily concentrating on IT companies, social safety companies, and internet app builders.
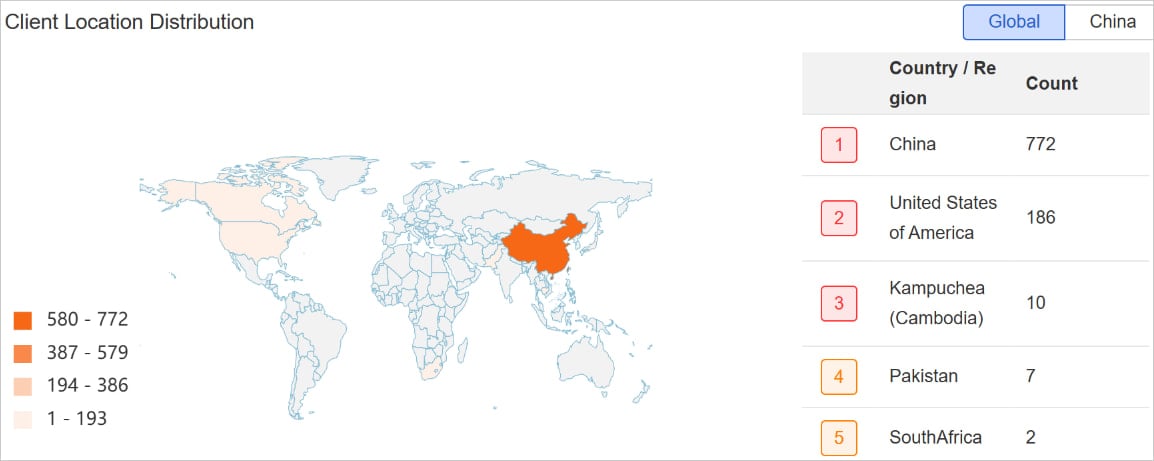
Supply: XLab
Code injection is used towards standard PHP frameworks used for internet growth, generally present in business-critical purposes, together with ThinkPHP, Yii, Laravel, and Dedecms.
The Baota internet panel, a well-liked server administration instrument in China, can be focused as it’s generally used to handle delicate information, together with MySQL databases.
The risk actors are additionally actively utilizing Glutton to actively hunt different hackers, embedding it inside software program packages bought on cybercrime boards like Timibbs. These trojanized software program packages impersonate playing and gaming techniques, faux cryptocurrency exchanges, and click-farming platforms.
As soon as the cybercriminals’ techniques are contaminated, Glutton deploys the ‘HackBrowserData’ instrument to extract delicate info from internet browsers, resembling passwords, cookies, bank cards, obtain historical past, and looking historical past.
“We hypothesize that HackBrowserData was deployed as part of a “black eats black” strategy,” explains XLabs.
“When cybercriminals attempt to locally debug or modify backdoored business systems, Glutton’s operators deploy HackBrowserData to steal high-value sensitive information from the cybercriminals themselves. This creates a recursive attack chain, leveraging the attackers’ own activities against them.”
XLabs shared indicators of compromise associated to this Winnti marketing campaign, which has been underway for over a yr. Nonetheless, the preliminary entry vector stays unknown.
