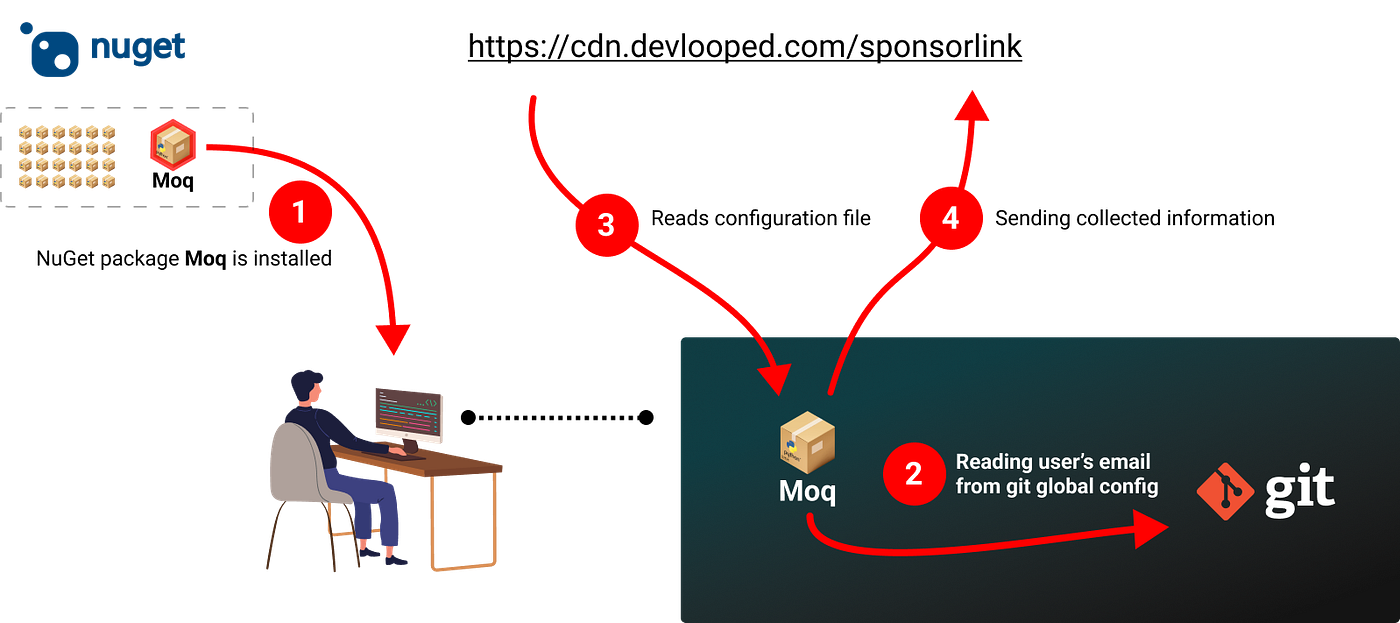
The extremely common NuGet package deal, Moq, with complete downloads of 475M+, launched a new variations 4.20.0 and 4.20.1 on August eighth with a brand new sub-dependency that has hidden executable code that reads the consumer’s native git config, extracting the developer’s electronic mail handle, hashing it, and sending it to a cloud service.
This incident was reported yesterday by Reddit consumer u/DinglDanglBob and in addition reported on the mission’s GitHub web page as a difficulty.
About Moq
Moq is a extremely common open-source mission to offer a mocking library for .NET purposes. From the mission’s GitHub web page:
Moq (pronounced “Mock-you” or simply “Mock”) is the one mocking library for .NET developed from scratch to take full benefit of .NET Linq expression timber and lambda expressions, which makes it the most efficient, type-safe and refactoring-friendly mocking library out there. And it helps mocking interfaces in addition to lessons. Its API is very simple and easy, and doesn’t require any prior data or expertise with mocking ideas.
Moq’s New Sub-Dependency – “SponsorLink”
Since model 4.20.0 of Moq, Devlooped.SponsorLink NuGet package deal has been added as a brand new dependency.
Because it turned out, Devlooped.SponsorLink is a closed-source mission, supplied as a compiled dll with obfuscated code, which scans the git config and sends the hashed electronic mail of the present developer to a cloud service. This code is executed through the utility construct and in case you are will depend on Moq there isn’t a choice to disable this.

Obfuscated Code
Consumer account d0pare commented and located that the library spawns an exterior git course of to get the developer’s electronic mail from the command git config --get consumer.electronic mail , then does some hashing and sends the end result to hxxps://cdn.devlooped[.]com/sponsorlink.
personal static string u00a0(string P_0) {
strive {
Course of course of = Course of.Begin(new ProcessStartInfo(
// that is obfuscated worth of "git"
6FA47342-3716-4274-AF01-7A37793E0E97.u206f(), // that is obfuscated worth of "config --get user.email"
6FA47342-3716-4274-AF01-7A37793E0E97.u3000()
) {
RedirectStandardOutput = true,
UseShellExecute = false,
CreateNoWindow = true,
WorkingDirectory = P_0
});
course of.WaitForExit();
if (course of.ExitCode != 0) {
return null;
}
return course of.StandardOutput.ReadToEnd().Trim();
} catch {}
return null;
}
He later found that the library additionally hundreds settings from the URL hxxps://cdn.devlooped[.]com/sponsorlink/settings.ini and is evasive in case one of many following surroundings variable exists
CI
TF_BUILD
TRAVIS
BUDDY
TEAMCITY_VERSION
APPVEYOR
JENKINS_URL
Customers Trying For Options
And I don’t blame them. Many customers appear involved about GDPR compliance as their merchandise are constructed utilizing Moq. This consumer commented that he will not be capable to use this package deal any extra:
It is a severe GDPR breach, and we received’t be capable to proceed utilizing this lib.
Additionally, having an obfuscated package deal included signifies that we are able to’t (simply) know what is occurring. It may harvest every other data from a developer’s machine with none consumer consent.
One other consumer, SefaOray additionally commented:
We’re eradicating moq instantly on account of this.
and lots of extra comparable feedback in this GitHub thread..
The Maintainer’s Response
GitHub consumer account kzu, the writer behind this, commented that it was merely a part of testing, and he marvel “why so much anger over sponsoring which can be done with as little as $1”

After posting this message, kzu in all probability panicked and determined to revert and unpublish variations 4.20.0 and 4.20.1 whereas shortly publishing 4.20.2with out the brand new dependency in Devlooped.SponsorLink NuGet package deal.
Abstract
Yesterday the proprietor of the favored NuGet package deal Moq included a brand new sub-dependency, which exfiltrates the consumer data with out his consent to hxxps://cdn.devlooped[.]com — a website owned by the writer of the Moq.
This sparked a debate on Reddit and GitHub, leaving many involved customers accusing this motion of GDPR violations and statements relating to the legitimacy of his motion.
Many organizations that constructed software program utilizing these releases are uncovered to GDPR compliance.
In my view, the writer didn’t intend to trigger any hurt however ended up damaging the belief of his customers. This might have been prevented if it had been open for dialogue previous to publishing the brand new modifications and accepting the content material of his customers.
We should perceive that it is our duty after we use open supply. That is why we have to assist open-source maintainers with a view to have a wholesome open-source ecosystem.
Timeline
2023–01–24: Creator printed a blogpost suggesting a brand new answer to open supply sustainability utilizing the SponsorLink service2023–02–04: Devlooped.SponsorLink first launch to NuGet2023–08–08: Moq launched new variations 4.20.0 and 4.20.1 with Devlooped.SponsorLink as a dependency2023–08–09: Moq launched model 4.20.2 eradicating the Devlooped.SponsorLink dependency
IOC
hxxps://cdn.devlooped[.]com/sponsorlink
Packages
Different NuGet Packages utilizing Devlooped.SponsorLink
devlooped.cloudstorageaccount.supply
devlooped.tablestorage
devlooped.cloudstorageaccount
devlooped.sponsorlink
isbn
gitinfo
thisassembly.assemblyinfo
thisassembly.constants
thisassembly.mission
thisassembly.git
thisassembly.strings
thisassembly.metadata
thisassembly.sources
nugetizer
devlooped.credentialmanager
websocketeer
websocketchannel
devlooped.internet
packagereferencecleaner
mvp.xml
devlooped.dynamically
thisassembly
