The Sysdig Home windows agent is a game-changer for cloud infrastructure, significantly with regards to securing Home windows containers in Kubernetes environments. Whereas many endpoint safety brokers are designed to supply safety for conventional Home windows hosts, Sysdig goes a step additional by incorporating Kubernetes-specific context into its system introspection. This integration is important as enterprises more and more undertake hybrid cloud and containerized infrastructure, and securing each Linux and Home windows workloads inside Kubernetes turns into a necessity.
What’s the Sysdig Home windows agent?
Your Home windows system is a excessive safety museum with priceless artifacts (just like the Louvre) and our agent is a group of specialised guards, consistently patrolling the halls, stopping patrons from touching artifacts, and guaranteeing everybody follows the strict guidelines to maintain your treasures secure. Leveraging the facility of open-source Falco, the agent ensures strong workload safety by detecting sudden behaviors and imposing compliance insurance policies.
What makes Sysdig’s method distinctive is that it brings the identical visibility & safety historically present in Kubernetes pods operating on Linux nodes to workloads operating on Home windows servers.
Why the Sysdig Home windows agent is important for contemporary cloud environments
In a cloud-native world, organizations have already quickly adopted Kubernetes and containers to scale their purposes and companies. Whereas Linux has been the dominant participant in cloud environments, Home windows workloads stay a vital element for a lot of companies, and are solely rising in significance, particularly when operating legacy purposes or particular enterprise companies with hyperconverged infrastructure (HCI) options that host Home windows and Linux containerized workloads and hosts.
With the Sysdig Home windows agent, enterprises achieve visibility and safety for Home windows workloads operating in Kubernetes environments, guaranteeing that safety insurance policies are uniformly utilized throughout all workloads. This consistency is important for sustaining compliance with laws like PCI, GDPR & HIPAA, in addition to for guaranteeing that Home windows workloads aren’t the weak hyperlink in your safety posture.
Furthermore, by integrating with Sysdig’s backend, the Home windows Agent can seamlessly accumulate and analyze information, enabling real-time detection and prevention of malicious actions reminiscent of unauthorized entry, file tampering, and runtime anomalies.
What units the Sysdig Home windows agent other than a typical EDR agent?
1. Native Kubernetes help: One of many standout options of the Sysdig Home windows agent is its capacity to run natively in Kubernetes. This functionality differentiates it from different Home windows endpoint safety brokers available on the market, which can focus solely on standalone Home windows techniques. By working instantly inside a Kubernetes node, the agent can accumulate Kubernetes-specific context, reminiscent of pod metadata, enabling extra granular visibility into Home windows containers.
2. Uniform detection rule semantics throughout a number of clouds: This functionality is essential for enterprises working advanced multi-cloud or hybrid environments that mix Linux & Home windows containers. With Sysdig, organizations can guarantee constant detection guidelines throughout various workloads, whether or not they’re operating on Linux or Home windows in the identical Kubernetes cluster.
3. Non-intrusive instrumentation by way of ETW: Lastly, the Sysdig agent leverages Occasion Tracing for Home windows (ETW) in a non-intrusive option to interface with the Home windows Kernel, eliminating the necessity for an additional kernel probe or driver to gather telemetry information. The ETW API provides a option to hint & log occasions generated by each user-mode apps and kernel-mode drivers. Built-in instantly within the Home windows OS, ETW gives builders with a quick and versatile method to Home windows detection and response.
Sysdig Home windows agent stipulations and set up
The Sysdig Home windows Agent presently helps the most recent Home windows builds, with Home windows Server 2019 and above being the minimal required model. This is applicable to each standalone Home windows server deployments and Kubernetes-based deployments utilizing Helm.
Putting in the Sysdig Home windows agent by way of CLI
For many who favor the command line, the set up course of is easy. You’ll be able to set up the Sysdig Home windows Agent in silent mode utilizing the next Command Line or PowerShell command:
msiexec /i sysdig-agent.msi COLLECTOR_URL=<COLLECTOR> COLLECTOR_PORT=6443 ACCESS_KEY=<AGENT_ACCESS_KEY> ACCEPT_TERMS_CONDITIONS=True /qnCode language: Perl (perl)On this command:
- Exchange
<COLLECTOR>with the URL of your Sysdig collector. - Exchange
<AGENT_ACCESS_KEY>along with your Sysdig entry key.
Putting in Sysdig Home windows agent on Kubernetes by way of Helm
For Kubernetes customers, Sysdig provides a Helm chart that permits the set up of the Home windows Agent with ClusterShield enabled. ClusterShield enhances Kubernetes metadata enrichment, offering extra detailed insights into your workloads.
Right here’s the Helm command to put in the Sysdig Home windows Agent:
helm repo add sysdig https://charts.sysdig.com
helm set up sysdig-agent --namespace sysdig-agent --create-namespace
--set international.sysdig.accessKey=<ACCESS_KEY>
--set international.sysdig.area=<SAAS_REGION>
--set nodeAnalyzer.enabled=false
--set international.clusterConfig.title=<CLUSTER_NAME>
--set agent.home windows.enabled=true
--set clusterShield.enabled=true
--set clusterShield.cluster_shield.log_level=warn
--set clusterShield.cluster_shield.options.kubernetes_metadata.enabled=true
sysdig/sysdig-deployCode language: Perl (perl)Key Helm flags
—set international.sysdig.accessKey=<ACCESS_KEY>
This flag specifies your Sysdig entry key.
—set international.clusterConfig.title=<CLUSTER_NAME>
This units the title of your Kubernetes cluster.
—set agent.home windows.enabled=true
This allows the Sysdig Home windows agent.
—set clusterShield.enabled=true
Permits the ClusterShield characteristic for enhanced safety.
—set clusterShield.cluster_shield.log_level=warn
Units the log degree to “warn,” which means solely warnings and significant points are logged.
—set clusterShield.cluster_shield.options.kubernetes_metadata.enabled=true
This allows Kubernetes metadata enrichment, offering detailed context for Kubernetes workloads operating on Home windows nodes.
Writing detection guidelines for Home windows
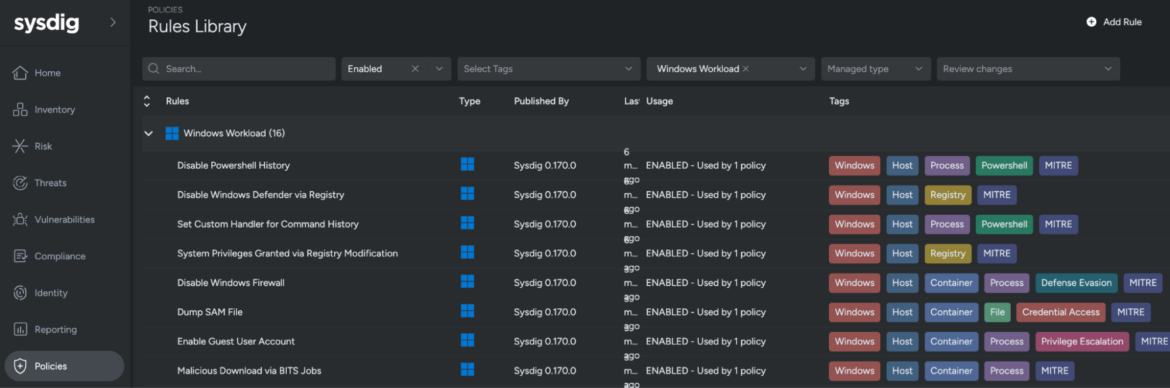
The Sysdig CNAPP platform provides managed Falco guidelines tailor-made for Home windows workloads, overlaying container and host actions. These managed guidelines are aligned with established safety frameworks like MITRE ATT&CK, guaranteeing a extra strong cybersecurity method. With pre-configured guidelines accessible out-of-the-box, Sysdig permits customers to shortly implement efficient risk detection on Home windows techniques.
Detection guidelines based mostly on Falco
DevOps engineering groups are already well-acquainted with Falco, the CNCF graduate undertaking used for real-time risk detection by way of syscall monitoring. As a substitute of making a brand new resolution, leveraging the identical know-how trusted by the cloud-native group is extra environment friendly. Home windows detection guidelines are written in YAML and observe the identical abstractions because the open-source Falco undertaking, streamlining the method for groups. This consistency permits safety groups to shortly develop detection guidelines for each Linux and Home windows workloads, avoiding the necessity to be taught yet one more proprietary detection logic.
Under is a fundamental instance of a Falco Rule for detecting command shell processes executed inside a pod.
- rule: Home windows Shell Spawned Inside Container
desc: Detects when the command shell is spawned inside a container.
situation: >-
process_execute and container_windows and proc.title in
(windows_shell_binaries)
output: >-
Shell Spawned in Container (evt.sort=%evt.sort evt.args=%evt.args
proc.title=%proc.title proc.pname=%proc.pname gparent=%proc.aname[2]
ggparent=%proc.aname[3] ggparent=%proc.aname[4] container.id=%container.id
container.title=%container.title container.picture=%container.picture)
precedence: important
tags:
- Home windows
- Container
- MITRE_TA0002_execution
supply: home windowsCode language: Perl (perl)In a Falco rule, you may reference a Record Useful resource to specify the Home windows shell binaries you need to monitor, enabling you to scope the method names for detection.
- checklist: windows_shell_binaries
gadgets: [cmd.exe, powershell.exe, putty.exe, git-cmd.exe, pwsh.exe]Code language: Perl (perl)As soon as the rule is triggered, you may look at the parent-child relationship by way of the Course of Tree occasion. This lets you see which processes had been executed, together with their related command-line arguments, throughout the Home windows container. Moreover, you may achieve detailed insights into the precise system name occasion varieties concerned.
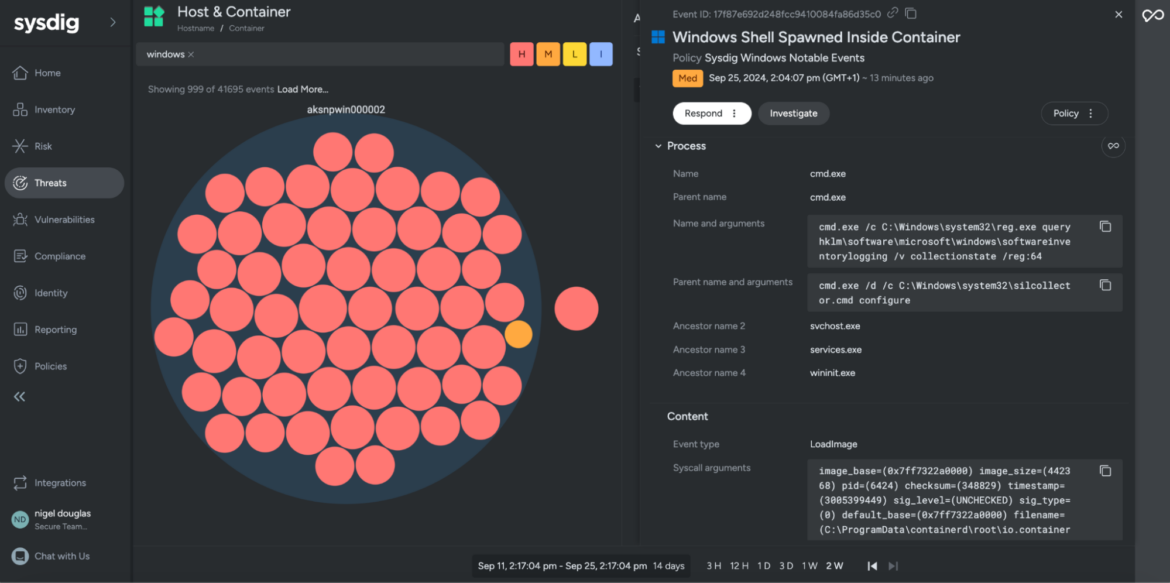
Efficient incident response in Kubernetes environments requires DevSecOps engineers to correlate course of and container exercise with Kubernetes metadata, reminiscent of Pod, Node, Deployment, Namespace, and Cluster title. This built-in context permits safety groups to reply to incidents on Home windows techniques with out manually piecing collectively info from a course of to the Kubernetes abstractions. This streamlined method considerably enhances the velocity and precision of risk response.
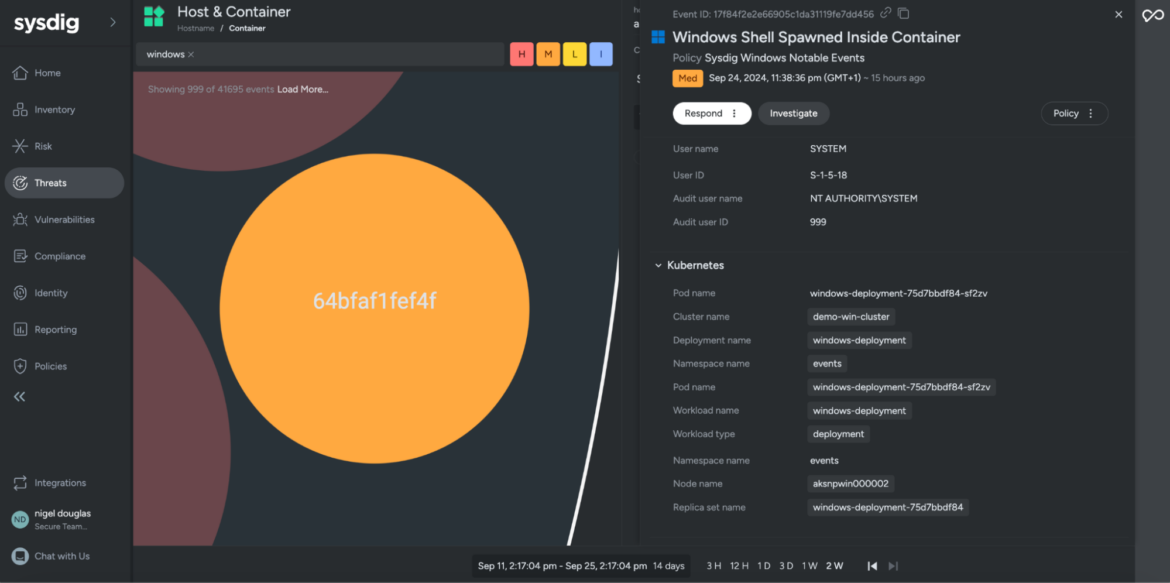
Advantages of Kubernetes Context for Home windows Workloads
By operating natively in Kubernetes, the Sysdig Home windows Agent gives a number of benefits:
- Enhanced Visibility: The agent captures detailed Kubernetes metadata, together with pod and container info, making it simpler to grasp how your Home windows workloads are behaving throughout the broader Kubernetes surroundings.
- Unified Safety Posture: Whether or not your workloads are on Linux or Home windows, Sysdig applies the identical insurance policies and protections, guaranteeing Detection and Response efforts are constant.
- Scalability: Sysdig’s structure is designed to scale along with your Kubernetes surroundings, which means that as you add extra nodes and workloads, Sysdig mechanically adjusts to supply steady CDR safety by way of Runtime Insights.
Conclusion
As organizations transfer in direction of hybrid and multi-cloud environments, it turns into important to have instruments that supply cross-platform, cloud-native and on-premise safety. The Sysdig Home windows Agent extends Sysdig’s already strong safety capabilities to Home windows workloads, significantly in Kubernetes environments. By accumulating Kubernetes-specific context and integrating seamlessly with the Sysdig platform, the Home windows Agent ensures that each one your workloads, Linux or Home windows, are protected, compliant, and monitored for potential threats.
For enterprises looking for to modernize their cloud infrastructure whereas sustaining stringent safety requirements, the Sysdig Home windows Agent represents a important addition to their present safety toolset. Whether or not you’re operating legacy Home windows purposes or fashionable microservices, the Sysdig Home windows Agent ensures that your Home windows workloads usually are not left susceptible in an more and more advanced cyber risk panorama. If you happen to’re new to the idea of operating Home windows Containers in Kubernetes, you may take a look at the official Kubernetes Consumer Information.