By Avia Yaacov, Product Supervisor, Pentera
Cryptojacking. It’s not as loud as ransomware or headline-grabbing knowledge breaches, however it’s quietly draining sources and racking up prices. As an alternative of locking you out of your techniques, cryptojacking silently hijacks your computing energy—whether or not it’s in your servers or within the cloud—and mines cryptocurrency with out you even figuring out.
It’s costing corporations greater than they notice, and it’s time to handle this menace earlier than it causes extra hurt.
In 2023, cryptojacking assaults surged by 659%, in accordance with SonicWall. For each $1 price of cryptocurrency mined, corporations are left paying round $53 in cloud prices. And since cryptojacking doesn’t instantly disrupt techniques like ransomware, it typically goes unnoticed—leaving organizations to find the injury lengthy after it’s been carried out.
With extra companies shifting to cloud environments and containerized infrastructures, cryptojackers are discovering new methods to take advantage of these techniques. The query is: how do you defend your group towards an assault that’s designed to remain hidden?
What’s Cryptojacking and How Does it Sneak In?
Cryptojacking entails the unauthorized use of your computing sources—whether or not it’s your CPU, GPU, or cloud infrastructure—to mine cryptocurrency like Bitcoin or Monero. The purpose isn’t to steal your knowledge, however your processing energy. And attackers have developed a number of strategies to get cryptomining code into your techniques.
Right here’s how they usually infiltrate:
- Drive-by Downloads: When customers go to compromised web sites, malicious cryptomining scripts can mechanically execute within the background. The BianLian ransomware group used this strategy in 2023, spreading cryptomining scripts to unknowing guests.
- Phishing Emails: Click on on a hyperlink or obtain a file from a phishing e mail, and you would be unknowingly downloading cryptomining malware. In 2024, a marketing campaign utilizing obfuscated SVG information bypassed defenses and deployed cryptojacking malware.
- Unpatched Vulnerabilities: Attackers love unpatched techniques. Cryptojackers typically exploit vulnerabilities in Apache servers, for instance, to unfold cryptomining malware throughout networks.
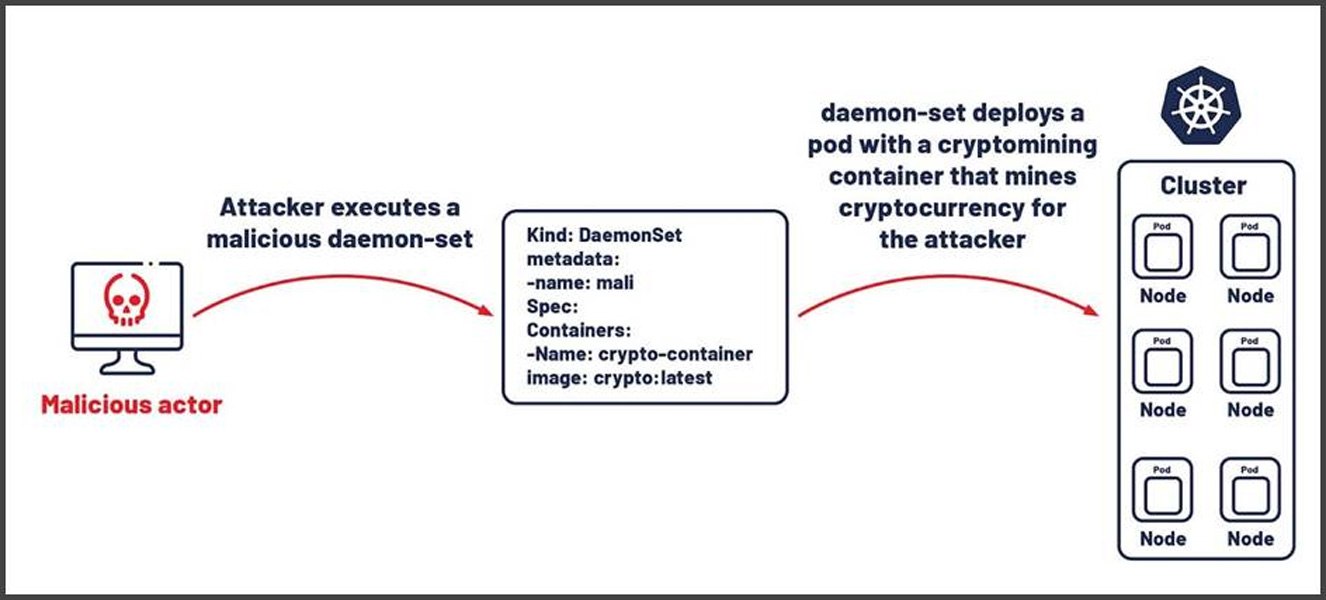
- Containerized Environments: As extra corporations undertake containers, cryptojackers are embedding mining scripts inside container pictures saved in public repositories. The 2024 Commando Cat marketing campaign exploited uncovered Docker APIs to deploy cryptominers.
Why Ought to You Care? The Actual-World Impression of Cryptojacking
Whereas cryptojacking would possibly look like a minor inconvenience in comparison with knowledge theft, its influence might be way more pricey than most companies notice.
- Efficiency Takes a Hit: Cryptojacking drains your CPU and GPU sources, which slows down your techniques. This ends in sluggish efficiency, making it tough to your servers to deal with reliable visitors. Moreover, the extreme energy consumption will increase power payments, strains {hardware}, and might result in overheating or gear injury. Customers expertise delays and productiveness suffers.
- Cloud Prices Surge: Cryptojacking on cloud environments can result in skyrocketing payments. Since cloud suppliers cost based mostly on useful resource utilization, compromised digital machines or containers operating mining malware devour huge quantities of CPU, GPU, and reminiscence, leading to sudden and infrequently astronomical payments.
- Downtime and Productiveness Losses: Overworked techniques can crash or decelerate to the purpose the place operations grind to a halt. It might not lock you out like ransomware, however cryptojacking may cause vital productiveness loss.
- Safety Vulnerabilities: Cryptojackers typically exploit the identical vulnerabilities that may result in bigger, extra damaging assaults. On condition that they have already got a foothold on the compromised useful resource, the attacker can leverage that at any time to take a unique assault tactic for additional system compromise – a typical secondary danger of cryptojacking.
Actual-World Case Research: The place Cryptojacking Hits Dwelling
Cryptojacking doesn’t simply goal smaller organizations. Main enterprises throughout industries, from tech to healthcare, have fallen sufferer to those assaults.
A tech firm noticed its AWS cloud sources hijacked for cryptomining, leading to $100,000 of sudden cloud prices. In the meantime, a healthcare supplier skilled important efficiency points, with cryptojacking slowing down their techniques and not directly exposing delicate knowledge.
In 2024, incidents surged throughout a number of sectors. The infamous TeamTNT group exploited uncovered Docker daemons, compromising cloud infrastructure, whereas one other marketing campaign focused Docker Engine APIs to infiltrate containerized environments.
Even enterprise-grade instruments weren’t spared: a important Atlassian Confluence vulnerability allowed attackers to deploy XMRig miners inside company networks. Misconfigured Kubernetes clusters turned a first-rate goal for deploying Dero miners, whereas the Migo malware compromised Redis servers by disabling safety features to hijack computing sources.
This rising menace underscores the significance of proactive defenses to keep away from probably devastating monetary and operational penalties.
Find out how to Detect and Forestall Cryptojacking: Sensible Options
To remain forward of cryptojackers, organizations want a proactive, multi-layered protection. Right here’s the way to get began:
- Endpoint Safety: Immediately’s endpoint safety instruments typically embrace cryptojacking detection. They monitor spikes in useful resource consumption and flag uncommon exercise, alerting admins to cryptomining scripts earlier than they trigger vital hurt.
- Community Monitoring: Cryptojacking typically leaves traces in community visitors. Instruments that analyze visitors patterns for uncommon connections to mining swimming pools that are networks that mix computing energy from compromised techniques to mine cryptocurrency extra effectively might help detect and stop cryptojacking early on.
- Cloud Monitoring: Platforms like AWS CloudWatch and Azure Monitor might help observe spikes in CPU or GPU consumption. A sudden bounce in useful resource consumption might be an indication of cryptojacking.
But it surely’s not sufficient to easily deploy these instruments. They must be configured appropriately and constantly up to date to make sure they’re efficient towards the most recent cryptojacking threats.
Steady Validation: Preserving Your Defenses Sturdy
Even probably the most superior instruments can’t assure 100% safety. With out common testing and validation, gaps in your defenses should still exist. That is the place steady safety validation is available in.
Steady validation ensures your defenses are at all times up-to-date by safely emulating cryptojacking assaults.
Utilizing protected variations of replicated cryptojacking malware, check how effectively your techniques can face up to an assault earlier than your setting is challenged within the wild.
The Backside Line
Cryptojacking could also be stealthy, however its influence is something however. From inflated cloud payments to sluggish efficiency and oblique safety dangers, it’s a rising menace that corporations can’t afford to disregard. However with a proactive strategy organizations can keep forward of cryptojackers and hold their sources protected.
By constantly testing your techniques with Pentera, you’ll know whether or not your defenses are sturdy sufficient to dam cryptojacking earlier than it prices your enterprise extra time, cash, and safety.
Get in contact with Pentera for an illustration.
Sponsored and written by Pentera.
