Each a number of years, a boring previous downside turns into related once more, sometimes as a result of those that develop new applied sciences fail to be taught classes from the errors of those that developed previous ones.
That is apparently the case with Cross-Web site Request Forgery (CSRF) and GraphQL server applied sciences.
In REST APIs, state-changing operations are explicitly linked to sure HTTP verbs: creation is carried out with POST, up to date with PUT or PATCH, and destructed with DELETE.
GraphQL additionally clearly distinguishes between operations used to fetch/learn knowledge (queries) and state-changing operations (mutations), which ought to be executed solely utilizing POST requests.
One may argue that GraphQL reduces the chance of state-changing operations being deliberately applied utilizing GET requests … nevertheless it seems, GraphQL servers are nonetheless simply as prone to be susceptible to unintentional misconfiguration.
For instance, in November 2019, GitHub discovered that defective validation logic of their Ruby-on-Rails-based software resulted in HEAD requests being dealt with as authenticated POST requests, successfully bypassing their OAuth controls.
Lower than two years later, a HackerOne report disclosed how an attacker may bypass Gitlab’s X-CSRF-Token header validation within the particular GraphQL mutations through the use of the GET requests: “When we send a GET request, the backend does not expect the X-CSRF-Token header. Using this, an attacker could leverage this to bypass the existing CSRF protection”.
So, HTTP Methodology/Verb Confusion, as soon as previous, turns into new once more.
Alternatively, most GraphQL APIs use POST requests for all their state-changing operations; nonetheless, they’re nonetheless susceptible to CSRF below sure situations.
Assuming that there isn’t a efficient anti-CSRF mechanism in place, an attacker can leverage sure content material sort misconfigurations with the intention to exploit CSRF.
From the docs:
By design, GraphQL APIs ought to solely settle for POST requests that use the software/json content material sort.
However it’s not unusual for attackers to ship seemingly unsupported knowledge codecs with the best variety of middleware-related shenanigans.
Once more, that is nothing new, it’s a widely known difficulty in REST APIs, and it’s very a lot price checking in GraphQL.
BatchQL is a “security auditing script” that checks among the situations described on this article, as proven under:
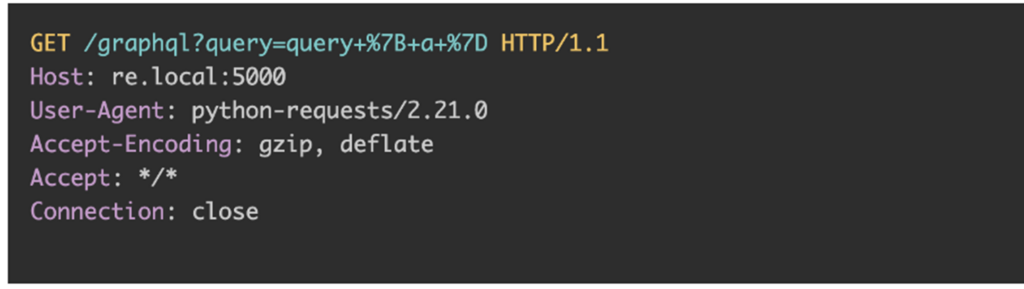
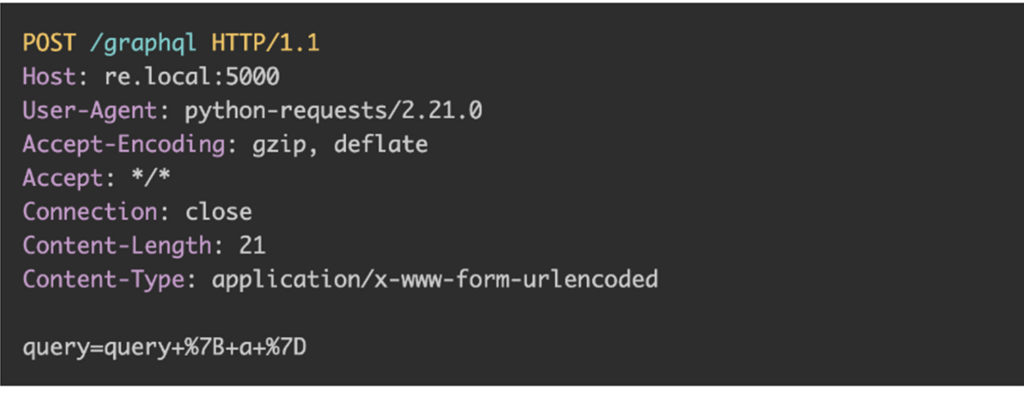
Because the device’s documentation explains, this isn’t “a foolproof way to determine whether a GraphQL API is vulnerable to CSRF attacks; however, it is a good indicator to perform further analysis to confirm if CSRF is possible.”
Okay, so how can we be taught from the errors of the previous?
We don’t must re-invent the wheel. Fortunately, the technical half was found out way back.
We have to be sure that the GraphQL servers are safe by default, and securing functions towards CSRF is solely the builders’ accountability.
Out of the field, servers ought to solely permit mutations to be executed in the event that they’re despatched through POST requests, whereas POST requests ought to solely be accepted in the event that they use the software/json content material sort.
Since builders typically mistakenly implement state-changing operations as queries, servers also needs to strongly encourage (if not merely implement) queries to be applied through POST.
Moreover, servers ought to assist builders perceive the impression of their CORS and cookie configurations. Good documentation and safe default choices go a great distance, in addition to alerting customers at any time when they make harmful choices, equivalent to accepting incoming requests from all origins (Entry-Management-Permit-Origin: *) or setting their cookies with the SameSite=None directive.
Lastly, these servers should help and undertake robust anti-CSRF mechanisms, equivalent to Anti-Forgery Tokens, by default.