Checkmarx printed our annual ‘World Pulse on Software Safety‘ report yesterday, and there’s loads to speak about. Determine 1 [below] is definitely my least favourite statistic, as a result of it actually exhibits how arduous it’s to guard an software at this time. There are simply too some ways through which purposes may be, and are, breached. That is clearly an issue. It’s an issue for a corporation whose enterprise is impacted by a breach. Nevertheless it’s additionally an issue for folks whose jobs it’s to develop and/or safe these purposes.
As I stroll across the RSAC present ground at this time, I see the phrase, “platform,” in all places. Each safety vendor has a “platform.” Everyone’s speaking about their “platform.” I’m certain that lots of you may have an identical response — this can be a phrase that has misplaced its which means. Admittedly, we additionally discuss (loads!) about our Checkmarx One™ Software Safety Platform. So what does “platform” imply to us? And what ought to it imply to you?
After we have a look at the way you develop and safe your purposes, our job is to make your job simpler. So our platform combines the entire completely different instruments you might want to safe your software improvement, together with SAST, SCA, provide chain safety, API safety, Infrastructure-as-Code (IaC) safety, and container safety. You may set off all of those by means of a single scan. You may see and triage all of your vulnerabilities in a single place. You may deploy every little thing extra simply and automate throughout your purposes, with a single set of SDLC integrations. And you may make it simpler on your builders to make things better, with IDE integration, suggestions instrument integration, PR ornament, and extra.
Our platform can also be how we roll out new merchandise and capabilities. After we launch a brand new product, it’s mechanically integrated into your current workflows. After we launch new options, you mechanically get them in your current merchandise. And at this time, we’re introducing quite a few new and up to date merchandise and capabilities throughout our platform as a part of our April 2023 platform launch.
Dart and Flutter assist
Programming language assist is #8 on our Top 10 Key Issues when selecting a SAST resolution as a part of an AppSec platform. Most organizations even have a broad requirement, from present languages you’re coding with at this time, to the lengthy tail of older languages in your legacy purposes, to future languages that you just don’t find out about but.
With this launch, Checkmarx SAST introduces the trade’s first assist for Dart and Flutter, two of the quickest rising client-side programming languages and software improvement kits available on the market at this time. Dart and Flutter assist continues our dedication to have the broadest language assist available on the market, and helps you construct fashionable digital experiences that stretch throughout platforms however are more and more pushed by cell.
Non-public packages
Software program composition evaluation (SCA) has historically centered on open supply dangers, together with license dangers and recognized vulnerabilities. Extra just lately, Checkmarx launched detection of malicious packages in open supply software program because the second step in software program provide chain safety (with SBOM usually considered step one).
Now, we’re introducing assist for personal packages — software program packages and libraries that aren’t publicly out there, usually saved in non-public package deal repositories or inside registries. Checkmarx SCA can now scan and analyze non-public packages and determine vulnerabilities which will exist inside them, offering organizations with a complete view of their software program stack and broadening what’s usually included in software program composition evaluation.
You may learn extra about Non-public Packages on Thursday in a weblog submit from our of Head of Product, Steve Boone.
Exploitable path for C#
Is a vulnerability truly exploitable? Each SCA resolution can let you know if a vulnerability is current in an open supply package deal utilized by your software, however that doesn’t imply it’s exploitable.
After we speak about “platform” at Checkmarx, we discuss loads about synergies between the completely different AST options that we provide on our platform. Exploitable path is a extremely cool characteristic that mixes the perception from Checkmarx SAST and SCA merchandise, and tells you when your proprietary code truly calls susceptible code in an open supply package deal. This can be a highly effective characteristic that depends on having SAST and SCA capabilities not simply on the identical platform, however speaking to one another in helpful methods.
With this launch, Checkmarx SCA provides C# to the checklist of supported programming languages the place this characteristic is out there.
SCA out there for all builders in Visible Studio Code
For builders utilizing Visible Studio Code, Checkmarx has at all times provided a Visible Studio plugin that brings the outcomes of Checkmarx One (SAST, SCA, and IaC) scans straight into your IDE. Now, we’re making Checkmarx SCA out there at no cost by means of the Visible Studio plugin, so that each one builders (no matter whether or not you’re a Checkmarx buyer) can scan and analyze their open supply packages for vulnerabilities.
New DAST providing
For organizations seeking to take a look at all through your SDLC, Checkmarx is bringing our DAST providing straight onto Checkmarx One. This implies you can now scan your proprietary code utilizing SAST on the identical platform that you just use to scan your compiled purposes with DAST. Enabling frequent integrations implies that each SAST and DAST scans may be automated as a part of your SDLC. Extra importantly, you possibly can see all your vulnerabilities in a single place, triage on your builders utilizing the identical workflow, and ship to them to repair utilizing the identical suggestions instrument integrations (e.g., JIRA). You may learn extra about Checkmarx DAST on this weblog submit by Andrew Schmit, and see it in motion right here.

Simpler shadow API detection
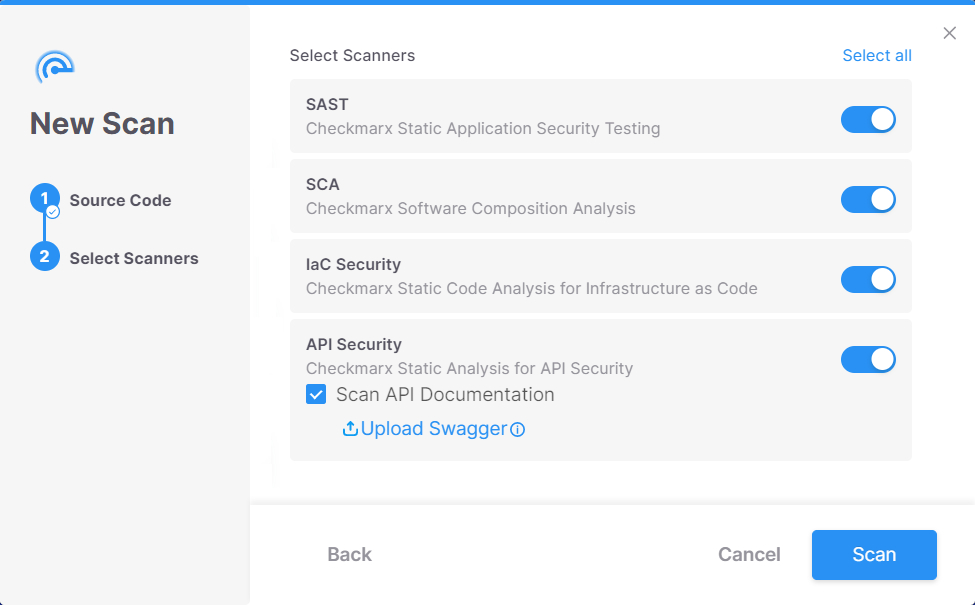
Final August, we launched the trade’s first “shift left” API Safety resolution that recognized API vulnerabilities in code, slightly than ready for purposes to be constructed and deployed. One of many central benefits was that we might scan proprietary code to find and stock your API endpoints outlined in code, and examine that to the checklist of documented APIs, and determine your shadow APIs earlier than they get out to manufacturing.
With the April 2023 platform launch, we’re making it simpler to take action by permitting you to arrange API documentation scanning as a part of your unified scans for any software program challenge. You may see Checkmarx API Safety in motion right here.
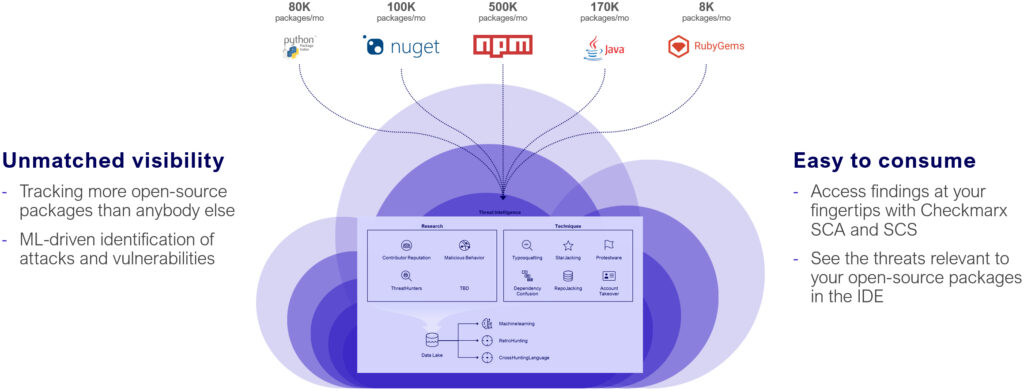
Provide Chain Menace Intelligence
In case you missed it, Checkmarx introduced the supply of our Provide Chain Menace Intelligence providing again in January. Provide Chain Menace Intelligence takes all of our newest menace intelligence on malicious packages, utilized by our safety researchers to determine attackers resembling RED-LILI and Lofygang, and makes them out there to prospects by way of a easy API name. This lets you construct that intelligence into your automated SDLC workflows, even if you happen to’re not a Checkmarx One buyer.
New secrets and techniques detection engine
Lastly, Checkmarx is releasing a brand new secret detection engine, aptly named Too Many Secrets and techniques (2MS). Within the context of purposes, secrets and techniques are delicate data resembling passwords, API keys, cryptographic keys, and different confidential information that an software must perform however shouldn’t be uncovered to unauthorized customers. As a part of the event course of, builders usually use collaboration instruments like Confluence to share secrets and techniques essential to develop an software. After which, as a result of all of us overlook about issues, these secrets and techniques may be by accident printed and disclosed.
2MS is an open supply challenge devoted to serving to folks defend their delicate data like passwords, credentials, and API keys from showing in public web sites and communication providers. Learn extra about 2MS tomorrow in a weblog submit from its product supervisor, Bryant Schuck, and obtain the challenge your self from GitHub.
Be taught extra
We’re excited to introduce these new capabilities as a part of our April 2023 Platform Launch, as we proceed to boost our platform to make your jobs simpler. For Checkmarx prospects, please attain out to your account group to study extra about these (and extra).
