Cyber attribution is the method of monitoring and figuring out the perpetrator of a cyberattack or different cyber operation. In an attribution investigation, safety analysts try to grasp the ways, methods and procedures (TTPs) the attackers used, and the “who” and “why” of the assault.
A fancy enterprise, cyber attribution calls for important time and assets. Even then, there is no such thing as a assure investigators will determine the perpetrator with affordable actually. In the event that they do succeed, the group would possibly nonetheless chorus from making the findings public or pursuing authorized motion, relying on circumstances and the group’s priorities.
Cyberattacks can have severe penalties for companies when it comes to public relations, compliance, fame and funds. After an assault, a company will typically launch an attribution investigation to get a extra full image of the incident itself and to determine the menace actors.
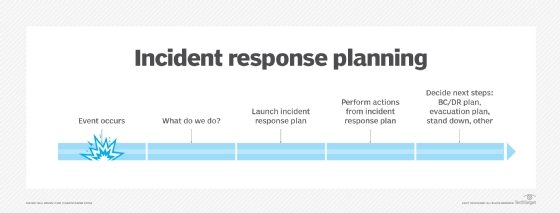
An attribution investigation is usually a part of a company’s bigger incident response plan. This method can assist a company reply to a cyberattack extra successfully whereas making it simpler to launch the attribution effort. The investigation may also be performed along with regulation enforcement businesses, cybersecurity companies or different organizations.
Cyber attribution is usually considered as a device for reinforcing accountability and bringing cybercriminals to justice. It may possibly additionally play an necessary function in defending towards future assaults. Safety groups would possibly higher perceive the TTPs cybercriminals used in addition to their goals and motivations. With such data, safety groups can plan higher protection and incident response methods. The data may yield perception into how greatest to prioritize their efforts and the place to speculate their assets.
Challenges of cyber attribution
Organizations typically lack the assets or experience wanted to do their very own cyber attribution, so they may rent outdoors safety consultants to help in or perform the investigation. Nonetheless, cyber attribution might be difficult even for them.
To determine the menace actors chargeable for a cyberattack, consultants typically conduct intensive forensic investigations. This contains analyzing digital proof and historic information, establishing intent or motives, and understanding the circumstances which may have performed a job within the assault. Nonetheless, the web’s underlying structure offers menace actors with a super surroundings for masking their tracks, making it powerful for investigators to trace down the perpetrators.
Hackers usually don’t perform assaults from their very own houses or locations of enterprise. Often, they launch their assaults from computer systems or units owned by different victims that the attacker has beforehand compromised. Hackers may spoof their very own Web Protocol (IP) addresses or use different methods, similar to proxy servers or digital non-public networks (VPNs), to confuse makes an attempt at identification.
Moreover, jurisdictional limitations can hinder attribution investigations in cross-border efforts as a result of investigators should undergo official channels to request assist. This will decelerate the method of gathering proof, which should happen as quickly as doable. As well as, there is no such thing as a worldwide consensus about the way to method cyber attribution, nor are there any agreed-upon requirements or ideas.
In some instances, cyber attribution efforts are difficult when assaults originate in nations that refuse to cooperate with investigators in different international locations. Such roadblocks can change into more and more problematic when political tensions are already excessive. Jurisdictional points can have an effect on the integrity of the proof and chain of custody.
What does cyber attribution determine in an investigation?
Safety consultants use a wide range of specialised methods when performing cyber attribution. Though these methods might be extremely efficient, producing definitive and correct cyber attribution is sort of troublesome and generally almost not possible. Nonetheless, many organizations and governments nonetheless imagine that attribution is well worth the effort.
Cybercrime investigators use evaluation instruments, scripts and packages to uncover crucial details about assaults. The investigators can typically uncover details about the applied sciences used, such because the programming language, program’s compiler, compile time, and software program libraries. They will additionally decide the order by which the assault occasions had been executed.
Info of every type can show helpful to the attribution course of. For instance, if investigators can decide {that a} piece of malware was written on a selected keyboard structure, similar to Chinese language or Russian, that data can assist slender down the listing of potential suspects.
Throughout the attribution course of, investigators additionally analyze any metadata related to the assault. The metadata would possibly embrace supply IP addresses, electronic mail information, internet hosting platforms, domains, area title registration data or information from third-party sources.
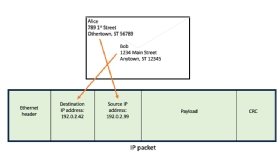
Metadata can assist make a extra convincing case for attribution. As an example, it’d present conclusive proof that the techniques used for the cyberattack communicated with nodes outdoors the focused community. Nonetheless, analysts should watch out when counting on such information as a result of information factors might be faked simply.
In some instances, investigators will analyze metadata collected from assaults which have focused totally different organizations. Doing so allows them to make assumptions and assertions primarily based on the recurrence of falsified information. For instance, analysts would possibly be capable of hyperlink an nameless electronic mail handle again to the attacker primarily based on the domains as a result of they’re related to a selected menace actor.
An necessary a part of any attribution effort is to look at the TTPs utilized in an assault. Attackers typically have their very own distinctive, recognizable kinds, and investigators can generally determine perpetrators primarily based on their assault strategies, similar to social engineering ways or kind of malware, as these may need been utilized in prior assaults.
As well as, understanding what’s taking place in associated industries or sure organizations can assist safety consultants predict assaults. As an example, corporations within the pure fuel trade spend more cash on exploration when fuel costs improve and, consequently, are at a better threat for theft of geospatial information.
Understanding the attacker’s motives may assist in cyber attribution. Safety consultants work to grasp the perpetrators’ goals, which is likely to be associated to monetary good points, political benefits or different components. Moreover, investigators attempt to uncover how lengthy the cybercriminals had been monitoring the focused techniques, whether or not they had been searching for particular information throughout their assault, and the way they will attempt to use what they discovered.
Though cyber attribution is not a precise science, these attribution methods can assist cybercrime investigators determine the attackers past an inexpensive doubt. The data can be helpful in defending towards future assaults.
Stopping cybercrime requires understanding how you’re being attacked. Study essentially the most damaging sorts of cyberattacks and what to do to stop them. Additionally, try our full information to incident response and enhance your individual cybersecurity implementation utilizing these cybersecurity greatest practices and suggestions.