What’s Azure Coverage? Azure Coverage is a service inside Microsoft Azure that enables organizations to create, assign, and handle insurance policies. These insurance policies outline guidelines and results over sources, identities, and teams, in an effort to make sure compliance and uphold safety. Enforcement is available in two kinds – flagging non compliance so your workforce can remediate the priority or just blocking deployment.
Earlier than delving deeper into Azure Coverage, let’s slim in on what a safety coverage is, particularly within the context of the Cloud. A safety coverage in cloud computing is a algorithm and tips that management the safety of cloud-based techniques and knowledge.
Safety insurance policies are an vital a part of sturdy cloud identification and entry administration (IAM). IAM insurance policies are essential for safeguarding knowledge by limiting the identities with entry to vital functions and property.
To drive this level dwelling, IBM’s 2022 Cloud Risk Panorama Report famous that identities had been excessively privileged in 99% of the cloud breach circumstances their groups analyzed.
Working multi-cloud? Study AWS Service Management Insurance policies right here and Google Cloud Group Coverage right here.
Core Ideas of Azure Coverage
Insurance policies and Initiatives
On the coronary heart of Azure Coverage are two core elements: insurance policies and initiatives. Insurance policies in Azure are the precise guidelines or tips, whereas initiatives are collections of insurance policies that assist obtain a broader compliance objective. Let’s break down the elements of insurance policies under.
Definitions, Parameters Assignments, and Azure Coverage Results
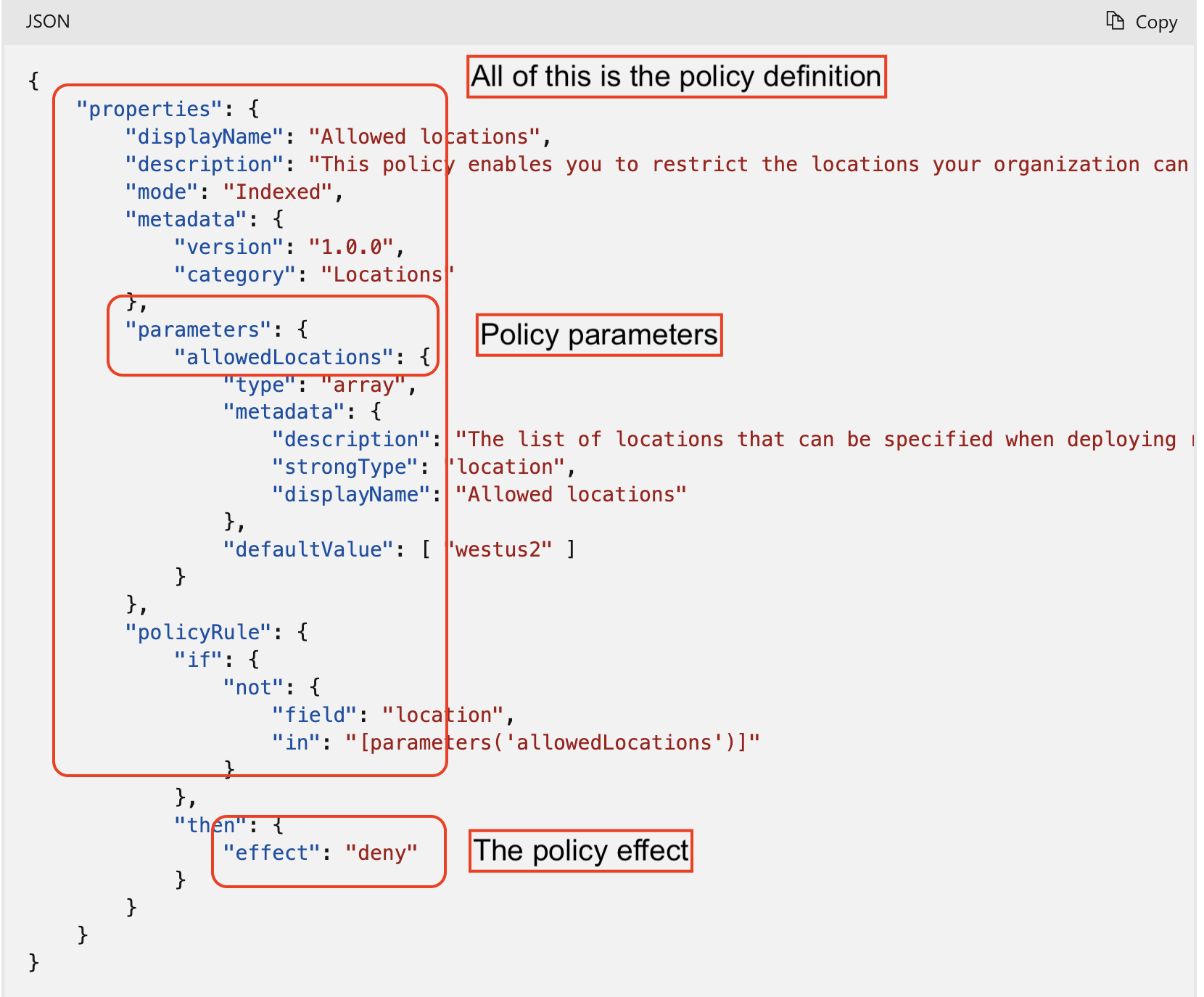
Coverage Definitions: A coverage definition expresses what to judge and what motion to take. Every coverage definition in Azure Coverage has a set of situations underneath which it’s enforced and an accompanying impact that takes place if the situations are met.
Azure Coverage Results: What occurs when the situations are met. Some widespread results embody: Deny, Audit, Append, Disabled, and DeployIfNotExists
Coverage Parameters: Parameters are used to supply flexibility and scale back coverage definition redundancy. They will let you reuse the coverage definition for various situations. Consider them as fields on a kind to fill out – title, metropolis, birthdate, handle, and many others. They continue to be, however the way you fill them out can change.
Coverage Assignments: Assignments are the applying of a coverage or initiative to a selected scope (subscription, administration group, and many others.)
Why Use Azure Coverage?
Useful resource Consistency
Azure Coverage ensures constant useful resource configuration throughout your setting, that is particularly useful in giant scale enterprise environments with varied tenants, subscriptions, and groups.
Regulatory Compliance
It helps in sustaining regulatory compliance by guaranteeing that sources and identification entry adheres to company requirements and authorized laws.
Safety
Azure coverage enhances safety by imposing restrictions on useful resource configurations and companies. Management over developer testing and deployment and common worker or machine identification privilege is vital for safeguarding your small business. Unauthorized entry and extreme privilege is a frequent and critical concern resulting in safety breach and enterprise disruption.

Hierarchy of various Azure scopes.
Forms of Azure Coverage Scopes
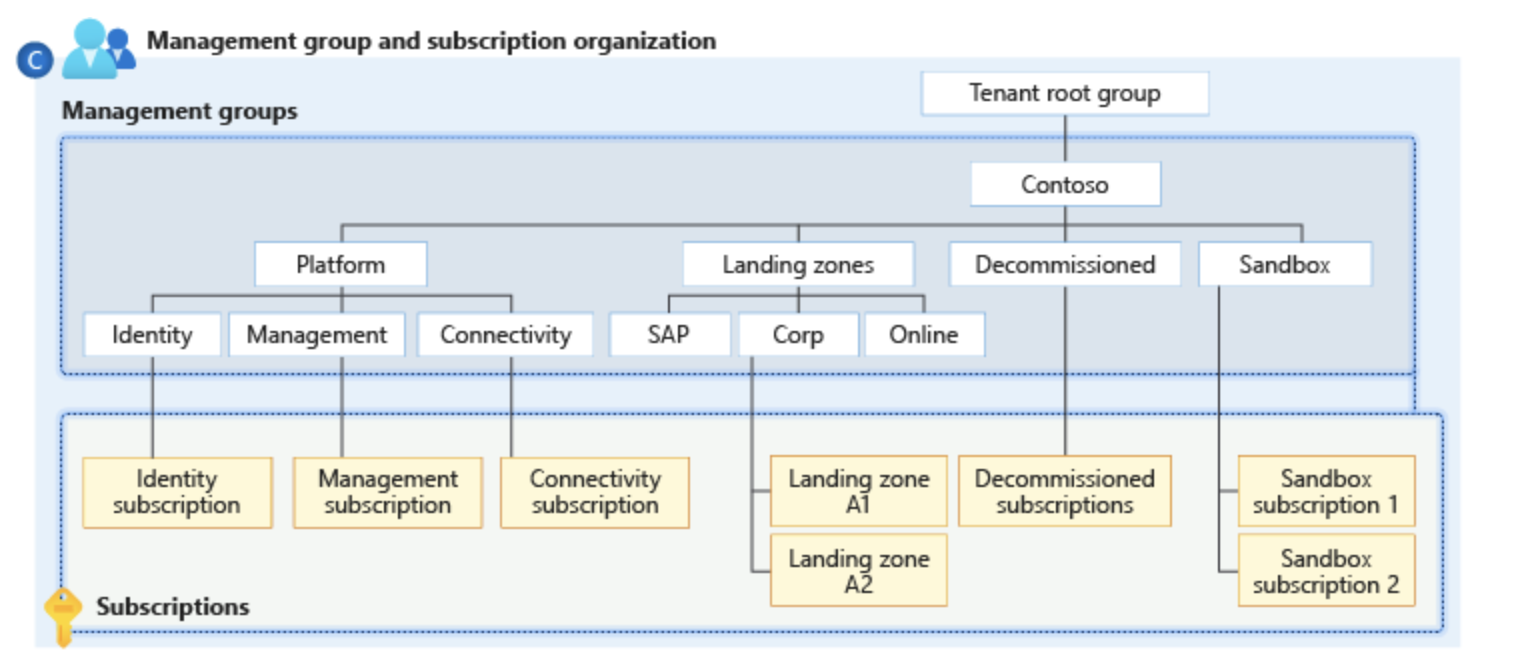
Administration Teams
Administration teams in Azure Coverage present a technique to handle entry, coverage, and compliance throughout a number of Azure subscriptions. They act as overarching safety guardrails.
Subscriptions
Insurance policies may be utilized to whole subscriptions, affecting all sources inside.
Useful resource Teams
Useful resource teams are one other stage at which insurance policies may be utilized, affecting all sources inside the group.
Particular person Assets
Insurance policies can be focused at particular sources, offering granular management.
The Energy of Coverage in Administration Teams
As talked about above, administration teams are a mechanism to assist group collectively Azure subscriptions. This could be a highly effective instrument when used accurately. Administration teams will let you handle a number of subscriptions alike, with out having to implement controls on the particular person subscriptions.
When constructing Azure insurance policies, you possibly can set the scope to “management group” to make sure safety practices are enforced throughout subscriptions. For instance, when you carried out role-based entry management to raised shield knowledge and sources, all of the subscriptions inside that administration group inherits the RBAC. It is a good technique to construct far-reaching safety guardrails.
You’ll be able to set up completely different administration teams to mirror your small business (regional items, groups, and many others.) or deployment phases (e.g. growth, testing, manufacturing.)
With many ranging scopes of coverage, differing inheritance processes and hierarchical buildings, Azure governance can get sophisticated. Beneath, we’ll talk about challenges related to it.
Azure Coverage vs Azure Position-Based mostly Entry Management
Azure Coverage and Azure Position-Based mostly Entry Management (RBAC) differ considerably. Whereas Azure Coverage focuses on useful resource properties, RBAC concentrates on person actions. Azure Coverage enforces properties on the time of useful resource creation or replace, whereas RBAC controls what customers can do with present sources.
In line with Microsoft, Azure administration teams assist Azure RBAC. Any function may be assigned to a gaggle and it’ll inherit down the hierarchy – for e.g. a job ‘vm contributor’ assigned to a useful resource group will lead all digital machines within the group to inherit the function.
What Are Widespread Challenges for Azure Insurance policies?
Coverage Hierarchy Complexity
The hierarchy of Azure insurance policies provides a layer of complexity, notably in giant organizations with a number of ranges of administration and sources. The challenges embody:
1. Visibility and Traceability: With insurance policies set at varied ranges – from the tenant stage all the way down to particular person companies – it turns into tough to have clear visibility into how these insurance policies work together and what their cumulative impact is. Insurance policies set at excessive ranges imply sources and identities down the hierarchy inherit these insurance policies and permissions.
2. Consistency and Battle Decision: Guaranteeing consistency of insurance policies throughout completely different ranges and resolving conflicts when overlapping insurance policies are utilized could be a tough process if performed manually.
3. Complexity in Troubleshooting: When points come up, diagnosing and troubleshooting change into extra advanced as a result of a number of layers of insurance policies that is likely to be affecting a useful resource or a service.
Get rid of coverage hierarchy complexity with Sonrai’s Poisonous Permission Analyzer.
Coverage Implementation
Implementing Azure insurance policies, particularly in advanced environments, may be difficult. The important thing points embody:
1. Understanding the Scope and Impression: Directors should completely perceive the scope and potential influence of a coverage earlier than implementation to keep away from unintended service disruptions.
2. Aligning Insurance policies with Enterprise Goals: Insurance policies have to be aligned with enterprise goals and compliance necessities, which requires a deep understanding of each the organizational targets and the technical elements of Azure companies.
3. Steady Monitoring and Adjustment: Insurance policies will not be set-and-forget. They require steady monitoring and changes to adapt to modifications within the cloud setting and organizational wants.
Compliance Requirements
Adhering to compliance requirements with Azure insurance policies entails a number of challenges:
1. Conserving Up with Regulatory Modifications: Compliance requirements will not be static. They evolve, and insurance policies have to be up to date accordingly, which requires fixed vigilance and flexibility, particularly if performed manually.
2. Mapping Compliance Necessities to Technical Controls: Translating compliance necessities into technical controls inside Azure insurance policies may be advanced and requires a deep understanding of each the regulatory panorama and Azure companies.
3. Proof of Compliance: Organizations typically want to supply proof of compliance, which implies they will need to have mechanisms in place to doc and report on coverage adherence and effectiveness.
How one can Use Azure Insurance policies
- Create the Coverage Definition: Begin by making a coverage definition that outlines the precise guidelines and situations. That is both a customized definition or one in all Microsoft’s built-in definitions.
- Create an Initiative Definition: Group a number of insurance policies into an initiative for broader governance targets. Once more, this may be customized or built-in.
- Outline Scope of the Initiative: Outline the scope of your initiative, whether or not it’s a administration group, subscription, or useful resource group. This defines how and the place your coverage is utilized.
- Decide Compliance: Consider the compliance standing of your sources in opposition to the outlined insurance policies and initiatives.
Azure Coverage Greatest Practices
Some ideas to bear in mind when constructing out insurance policies:
- Begin with an Audit or AuditIfNotExist Impact: Start with insurance policies that audit somewhat than implement, to know the influence with out disrupting present sources.Consider this as a trial run or take a look at.
- Think about Organizational Hierarchies: Align your insurance policies together with your organizational construction for efficient governance. This implies first organizing your teams by roles or groups, after which making use of insurance policies to those completely different buildings.
- Use Parameters: As we mentioned above, using parameters makes insurance policies extra versatile and reusable, taking guide effort off your workforce.
- Create and Assign Initiative Definitions: Use initiative definitions to bundle associated insurance policies into teams for simpler administration.
- Repeatedly Overview Insurance policies: Repeatedly overview and replace your insurance policies as groups, initiatives, priorities, and compliance laws evolve.
Azure Coverage Examples
Let’s take into account some azure coverage examples.
First, take into account a coverage set on the administration group stage solely permitting particular useful resource sorts. This coverage ensures that solely authorized kinds of Azure sources may be created inside all of the subscriptions underneath that administration group.
As an illustration, a company would possibly wish to limit the creation of sure kinds of storage accounts that aren’t compliant with regulatory requirements. By making use of this coverage on the administration group stage, the group ensures a uniform compliance posture throughout all its Azure subscriptions.
Additional, one other azure coverage instance could possibly be managing entry to manufacturing vs non manufacturing workloads. You need to use a administration group coverage to implement that developer roles have contributor permissions in non-production environments, and read-only permissions for manufacturing environments.
Lastly, let’s check out a selected coverage set on the administration group scope that’s defining a customized function with the next permissions in JSON format:
{
“Name”: “MG Test Custom Role”,
“Id”: “id”,
“IsCustom”: true,
“Description”: “This role provides members with custom roles.”,
“Actions”: [
“Microsoft.Management/managementgroups/delete”,
“Microsoft.Management/managementgroups/read”,
“Microsoft.Management/managementgroup/write”,
“Microsoft.Management/managementgroup/subscriptions/delete”,
“Microsoft.Management/managementgroup/subscriptions/write”,
“Microsoft.resources/subscriptions/read”,
“Microsoft.Authorization/policyAssignments/*”,
“Microsoft.Authorization/policyDefinitions/*”,
“Microsoft.Authorization/policySetDefinitions/*”,
“Microsoft.PolicyInsights/*”,
“Microsoft.Authorization/roleAssignments/*”,
“Microsoft.Authorization/roledefinitions/*”
],
“NotActions”: [],
“DataActions”: [],
“NotDataActions”: [],
“AssignableScopes”: [
“/providers/microsoft.management/managementGroups/ContosoCorporate”
]
}
Safety Visibility Problem with Azure Coverage
The complexity of managing a number of overlapping insurance policies in Azure can result in a scarcity of visibility and management. It’s essential to have a complete understanding of the cumulative impact of those insurance policies in your Azure setting to keep away from potential challenges.
With out correct visibility, your identities would possibly find yourself with entry that was by no means supposed. Within the cloud, privileges may be inherited in methods that aren’t instantly obvious, making it tough to trace them ‘on paper.’ Any such hidden privilege can create alternatives for lateral motion inside your community, which malicious attackers may exploit.
Conversely, when you implement an excessively conservative technique with strict denial via Azure Coverage, you might face growth disruptions and inefficient request processes.
Improve Azure Insurance policies with Sonrai
This weblog answered the query, ‘what is azure policy?’ Azure Coverage is a key factor of Azure’s safety and governance framework. With acceptable instruments and practices, managing Azure insurance policies can change into an environment friendly and integral a part of your cloud safety technique.
Implementing and managing Azure insurance policies may be advanced, however instruments like Sonrai’s cloud infrastructure entitlement administration answer could make this course of extra manageable. Sonrai’s patented permission analytics take into account each kind of coverage – Azure AD group coverage, useful resource group insurance policies, administration group insurance policies, and extra. This gives your groups with a transparent view of the efficient privileges of each identification in your setting and higher administration over sources.
This perception, mixed with steady monitoring of permission and entry modifications, helps alert groups to any potential identification dangers, reminiscent of unintended privileges or assault paths to delicate knowledge.
Uncover Sonrai’s CIEM answer right here. Or discover how Sonrai secures Azure environments

FAQ
Azure roles deal with person actions and permissions, whereas Azure insurance policies implement guidelines on useful resource properties and configurations.
Azure Coverage ensures that sources adjust to company requirements and regulatory necessities, thereby enhancing compliance.
Azure Coverage is built-in inside the Azure ecosystem, offering seamless governance and compliance capabilities in comparison with different cloud companies.
Sure, Azure Coverage may be utilized throughout a number of subscriptions and administration teams, permitting for broad governance and compliance enforcement.
Azure Coverage integrates with Azure companies like Azure Monitor via Azure Useful resource Graph for enhanced safety and compliance monitoring, offering a unified view of compliance standing throughout sources.
Managing a lot of Azure Coverage definitions and initiatives successfully entails grouping associated insurance policies into initiatives for simpler administration, utilizing hierarchical administration teams for coverage task, and leveraging tags for group and filtering. These practices assist keep an organized, environment friendly coverage administration framework.