A brand new pressure of ransomware dubbed ShrinkLocker is being utilized by cyberattackers to focus on enterprise computer systems. It exploits the Microsoft BitLocker encryption characteristic to encrypt all the native drive and take away the restoration choices earlier than shutting down the PC. ShrinkLocker was found by cybersecurity agency Kaspersky, and analysts have noticed variants in Mexico, Indonesia and Jordan.
BitLocker has been used to stage ransomware assaults previously, however this pressure has “previously unreported features to maximise the damage of the attack,” Kaspersky stated in a press launch. ShrinkLocker is exclusive in that it might verify the model of a tool’s Home windows working system to make sure it permits the suitable BitLocker options, however deletes itself if it might’t.
Cristian Souza, incident response specialist at Kaspersky World Emergency Response Staff, stated within the press launch, “What is particularly concerning about this case is that BitLocker, originally designed to mitigate the risks of data theft or exposure, has been repurposed by adversaries for malicious ends. It’s a cruel irony that a security measure has been weaponized in this way.”
Who’s weak to ShrinkLocker assault?
Firms in metal and vaccine manufacturing, in addition to a authorities entity, have been focused with ShrinkLocker to this point. Nonetheless, Souza advised TechRepublic there “is no evidence to believe that this group is targeting specific industries,” as victims are from totally different nations and sectors.
BitLocker is at present solely accessible on the Professional, Enterprise, Training and Final editions of Home windows working methods, however it will likely be included and routinely activated in all variations with the discharge of Home windows 11 24H2 later this yr. This considerably will increase the potential scope of ShrinkLocker victims.
“Infections by ShrinkLocker can be critical if the victim does not have adequate proactive and reactive measures in place,” Souza added. “Since BitLocker is a native Windows feature, any machine with Windows Vista+ or Server 2008+ could be affected.”
How does ShrinkLocker work?
Though ShrinkLocker self-deletes after encrypting the goal, Kaspersky analysts had been capable of uncover the way it works by finding out a script left behind on a drive on a PC that was contaminated however didn’t have BitLocker configured.
Attackers may deploy ShrinkLocker on a tool by exploiting unpatched vulnerabilities, stolen credentials or internet-facing providers to realize entry to servers. A consumer can also unintentionally obtain the script, for instance, by means of a hyperlink in a phishing e-mail.
“Once they have access to the target system, the attacker can try to exfiltrate information and finally execute the ransomware to encrypt the data,” Souza advised TechRepublic.
As soon as the script is triggered, it makes use of Home windows Administration Instrumentation extensions and the Win32_OperatingSystem class to question details about the system’s working system and area. If the system runs on Home windows XP, 2000, 2003 or Vista, or the present area of the queried objects doesn’t match the goal, the script deletes itself.
SEE: Is there a easy strategy to get better encrypted BitLocker drives?
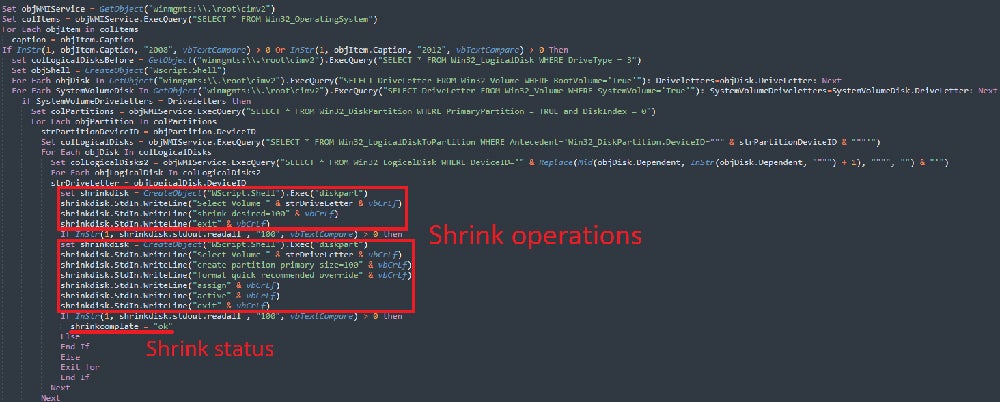
Nonetheless, if the PC is utilizing Home windows 2008 or earlier, the script will transfer on to resizing its native fastened drives. It shrinks non-boot partitions by 100MB to create unallocated disk house, which is why it has been dubbed ShrinkLocker. New main partitions are created within the unallocated house, and the boot information are reinstalled so the system might be rebooted with the encrypted information by the sufferer.
Subsequent, the script modifies Home windows registry entries to disable Distant Desktop Protocol connections and implement BitLocker settings like PIN necessities. It then renames the boot partitions with the attacker’s e-mail — onboardingbinder[at]proton[dot]me or conspiracyid9[at]protonmail[dot]com — and replaces current BitLocker key protectors to forestall restoration.
ShrinkLocker creates a brand new 64-character encryption key utilizing the random multiplication and substitute of the next parts:
- A variable with the numbers zero to 9.
- The pangram “The quick brown fox jumps over the lazy dog,” which incorporates each letter of the English alphabet, in lowercase and uppercase.
- Particular characters.
It then permits BitLocker encryption on all the system’s drives. ShrinkLocker solely encrypts the native, fastened drive of the contaminated PC and doesn’t infect community drives seemingly to assist evade detection.
The 64-character key and a few system info are despatched to the attacker’s server by way of an HTTP POST request to a randomly generated subdomain of ‘trycloudflare[dot]com.’ This can be a reputable area from CloudFlare that’s meant for use by builders for testing out CloudFlare Tunnel with out including a website to CloudFlare’s DNS. The attackers exploit it right here to cover their actual handle.
Lastly, ShrinkLocker self-deletes its script and scheduled duties, clears the logs, activates the firewall and deletes all the foundations earlier than forcing a shutdown. When the consumer reboots the system, they’re introduced with the BitLocker restoration display screen with no restoration choices accessible — all of the PC’s information is encrypted, locked and out of attain.
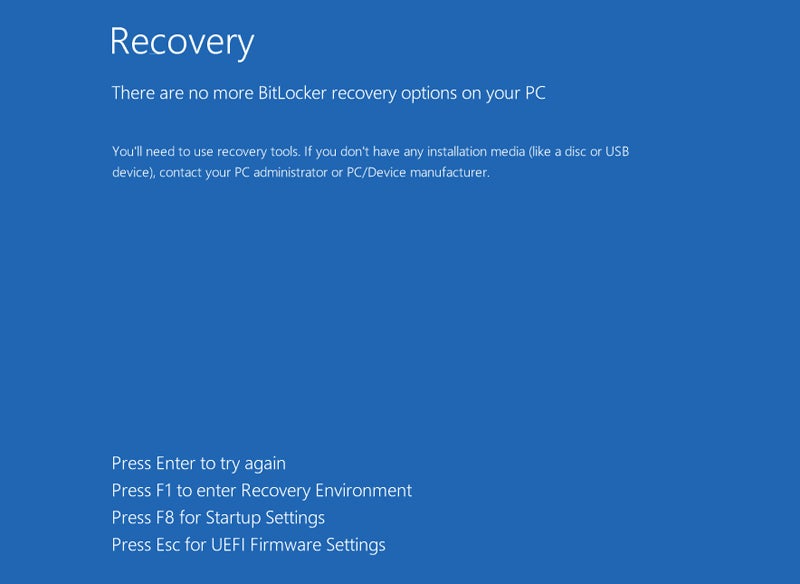
The brand new drive labels with the attacker’s e-mail instruct the consumer to contact them, implying a ransom demand for the decryption key.
In a technical evaluation, Kaspersky analysts describe each the detection of a ShrinkLocker assault and the decryption course of as “difficult.” The latter is especially arduous as a result of the malicious script incorporates variables which are totally different for every affected system.
Who’s answerable for the ShrinkLocker assaults?
Kaspersky specialists have, to this point, not been capable of determine the supply of the ShrinkLocker assaults or the place the decryption keys and different system info are despatched. Nonetheless, some details about the attackers might be gleaned from the malware script.
The analysts stated that the script, written in VBScript, “demonstrates that the malicious actor(s) involved in this attack have an excellent understanding of Windows internals.”
The labels containing the attacker’s e-mail handle can solely be seen if the contaminated system is booted by an admin in a restoration setting or with diagnostic instruments, in response to BleepingComputer. Moreover, the BitLocker restoration display screen can have a customized be aware added, but the attackers particularly selected to not create one.
The truth that the attackers seem to have deliberately made it tough to contact them suggests their motives are disruption and destruction slightly than monetary acquire.
“For now, we know we are dealing with a very skilled group,” Souza advised TechRepublic. “The malware we were able to analyse shows that the attackers have a deep understanding of the operating system’s internals and various living-off-the-land tools.”
How can companies shield themselves towards ShrinkLocker?
Kaspersky offers the next recommendation to companies trying to shield their units from the ShrinkLocker an infection:
- Use strong, correctly configured endpoint safety platforms to detect potential malicious exercise earlier than encryption.
- Implement managed detection and response to proactively scan for threats.
- Guarantee BitLocker has a powerful password and the restoration keys are saved in a safe location.
- Restrict consumer privileges to the minimal required to do their job. This fashion, no unauthorised personnel can allow encryption options or change registry keys on their very own.
- Allow community site visitors logging and monitoring, capturing each GET and POST requests, as contaminated methods could transmit passwords or keys to attacker domains.
- Monitor for VBScript and PowerShell execution occasions, saving logged scripts and instructions to an exterior repository to retain exercise even when native information are deleted.
- Make backups continuously, retailer them offline and check them.
How has BitLocker been focused previously?
BitLocker has been focused by unhealthy actors quite a few instances previously, nicely earlier than the emergence of ShrinkLocker. In 2021, a hospital in Belgium had 40 servers and 100 TB of its information encrypted after an attacker exploited BitLocker, resulting in delays in surgical procedures and the redirection of sufferers to different services.
The next yr, one other attacker focused one among Russia’s largest meat suppliers in the identical method, earlier than Microsoft reported the Iranian authorities had sponsored plenty of BitLocker-based ransomware assaults that demanded hundreds of U.S. {dollars} for the decryption key.