Web Archive’s “The Wayback Machine” has suffered an information breach after a menace actor compromised the web site and stole a consumer authentication database containing 31 million distinctive information.
Information of the breach started circulating Wednesday afternoon after guests to archive.org started seeing a JavaScript alert created by the hacker, stating that the Web Archive was breached.
“Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!,” reads a JavaScript alert proven on the compromised archive.org website.
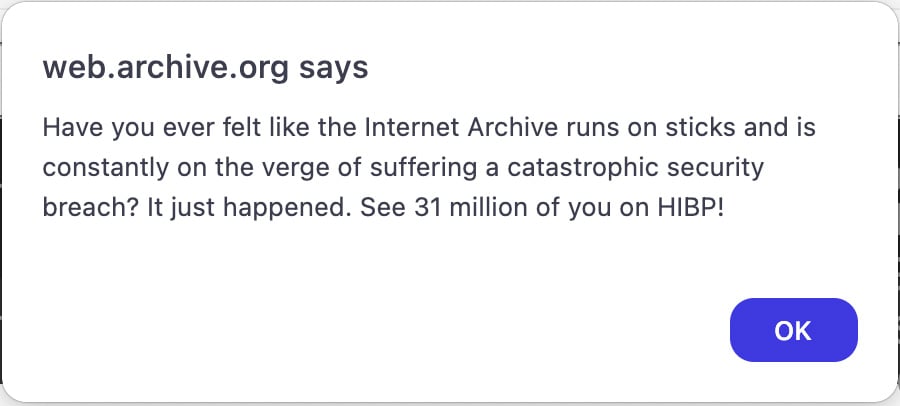
Supply: BleepingComputer
The textual content “HIBP” refers to is the Have I Been Pwned information breach notification service created by Troy Hunt, with whom menace actors generally share stolen information to be added to the service.
Hunt instructed BleepingComputer that the menace actor shared the Web Archive’s authentication database 9 days in the past and it’s a 6.4GB SQL file named “ia_users.sql.” The database comprises authentication data for registered members, together with their e mail addresses, display screen names, password change timestamps, Bcrypt-hashed passwords, and different inside information.
Hunt says there are 31 million distinctive e mail addresses within the database, with many subscribed to the HIBP information breach notification service. The info will quickly be added to HIBP, permitting customers to enter their e mail and make sure if their information was uncovered on this breach.
The info was confirmed to be actual after Hunt contacted customers listed within the databases, together with cybersecurity researcher Scott Helme, who permitted BleepingComputer to share his uncovered report.
9887370, internetarchive@scotthelme.co.uk,$2a$10$Bho2e2ptPnFRJyJKIn5BiehIDiEwhjfMZFVRM9fRCarKXkemA3PxuScottHelme,2020-06-25,2020-06-25,internetarchive@scotthelme.co.uk,2020-06-25 13:22:52.7608520,N0NN@scotthelmeNNN
Helme confirmed that the bcrypt-hashed password within the information report matched the brcrypt-hashed password saved in his password supervisor. He additionally confirmed that the timestamp within the database report matched the date when he final modified the password in his password supervisor.
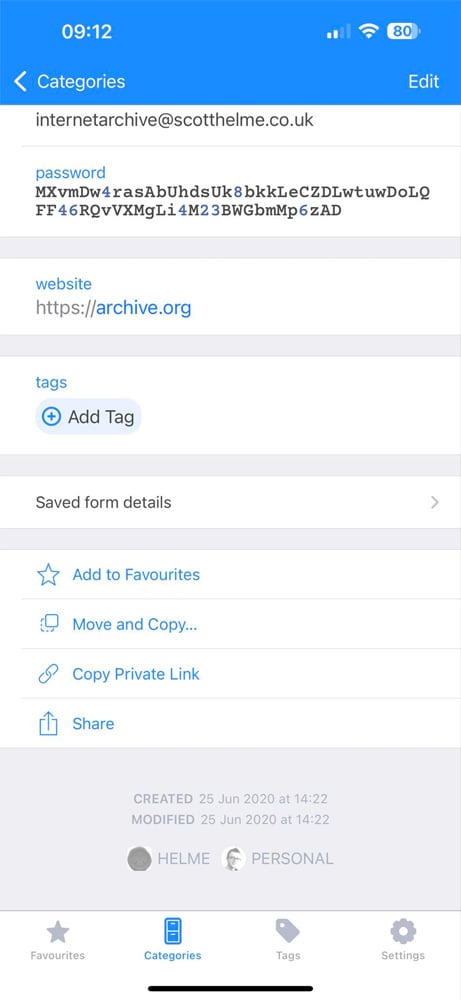
Supply: Scott Helme
Hunt says he contacted the Web Archive three days in the past and started a disclosure course of, stating that the information can be loaded into the service in 72 hours, however he has not heard again since.
It’s not recognized how the menace actors breached the Web Archive and if every other information was stolen.
Earlier at the moment, the Web Archive suffered a DDoS assault, which has now been claimed by the BlackMeta hacktivist group, who says they are going to be conducting extra assaults.
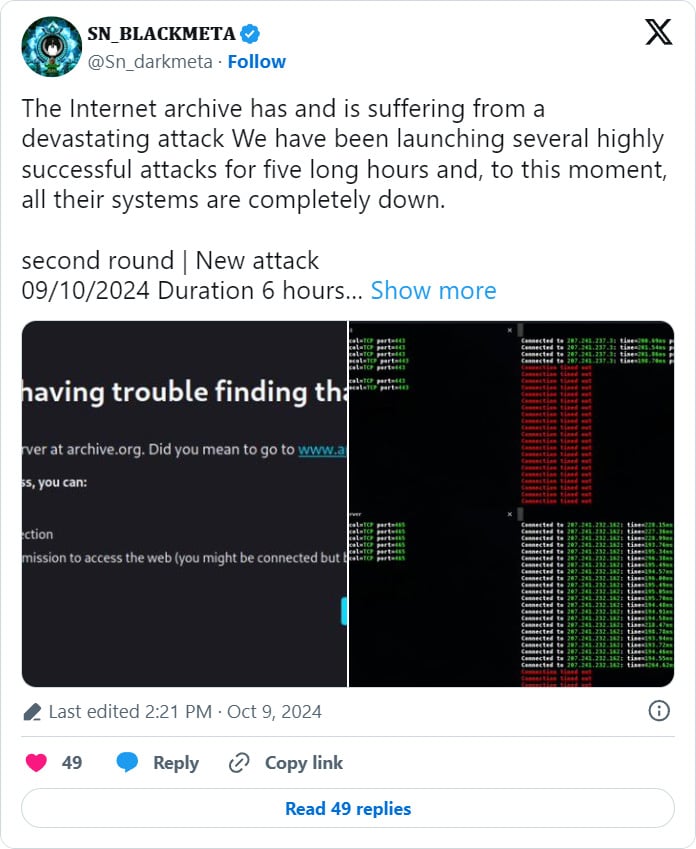
BleepingComputer contacted the Web Archive with questions concerning the assault, however no response was instantly accessible.
