Earlier this yr, Mandiant Consulting’s incident response crew tracked an assault by a China-linked espionage group again to the compromise of an edge machine in its consumer’s community, however as a result of the equipment is a closed system, the sufferer of the assault needed to request a forensic picture from the maker of the community equipment.
Two months later, the consumer continues to be ready.
This issue in detecting — after which investigating — compromises of edge home equipment highlights why many nation-state attackers are more and more concentrating on firewalls, e mail gateways, VPNs, and different units, says Charles Carmakal, CTO for Mandiant Consulting at Google Cloud. The menace teams not solely evade detection longer, however even when defenders get wind of the assault, investigating the incident is way more tough.
It is an issue that Mandiant offers with “all the time,” he says.
“We have much better telemetry for Windows computers today, mostly because of the maturity of EDR [endpoint detection and response] solutions,” Carmakal says. “The telemetry on edge devices … is often completely nonexistent. To be able to triage and forensically examine the device, you’ve got to get a forensic image, but you can’t just open up the device and pull the hard drive out.”
Espionage attackers’ shift to exploiting edge units is without doubt one of the main tendencies that Google Cloud’s Mandiant Consulting noticed in 2023, based on the M-Tendencies 2024 report printed on April 23. Total, the corporate tracked and reported on greater than two dozen campaigns and international occasions in 2023 associated to its investigations.
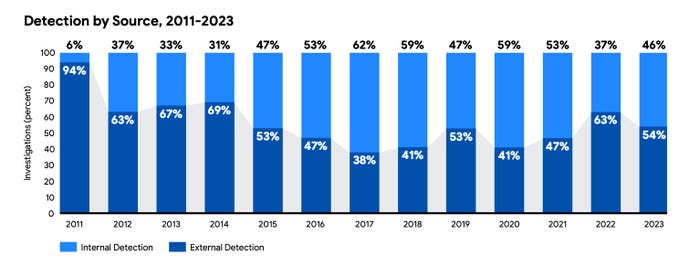
The period of time an attacker is energetic on a compromised techniques earlier than detection, generally known as dwell time, continued to shrink — to 10 days in 2023, down from 16 days the earlier yr. Ransomware accounted for 23% of Mandiant’s investigations in 2023, up from 18% in 2022. Corporations grew to become conscious of most incidents (54%) as a result of a 3rd social gathering — typically the attacker themselves, within the case of ransomware — notified the sufferer.
With ransomware typically notifying victims, exterior detection rose to 54%. Supply: Google Cloud’s Mandiant
Attackers Transfer to Much less Seen Environments
Whereas edge units require educated attackers to compromise and management them, these high-availability environments additionally normally provide their very own utilities and options to cope with native codecs and performance. By “living off the land” and utilizing the built-in capabilities, attackers can construct extra dependable malware and nonetheless run much less danger of being detected, due to the shortage of visibility defenders have into the inner operations of the units.
“[M]any of these devices are put through rigorous testing regimes by the manufacturer during development to ensure their stability,” Mandiant said within the report. “China-nexus malware developers take advantage of the built-in functionality included in these systems … leveraging native capabilities [that can] reduce the overall complexity of the malware by instead weaponizing existing features within that have been rigorously tested by the organization.”
In a single incident, Mandiant consultants found the BoldMove backdoor malware, Chinese language attackers crafted to contaminate a Fortinet machine, disabling two logging options and permitting the attacker to stay undetected for an extended interval. BoldMove was created particularly for Fortinet environments.
Incident response efforts are additionally typically hampered by the shortage of quick access for consultants and defenders to the underlying working system. With no solution to analyze the underlying code to hunt out compromised units, incident responders typically can’t decide the basis reason for a compromise, says Mandiant’s Carmakal.
“Some vendors refuse to give forensic images, [which] I understand … because they have a lot of intellectual property on the device,” he says. “Companies need to understand the scope and extent of a compromise, and if it starts on a network device, and you need to look into that.”
Exploit Use Rises, Extra Knowledge Leak Websites
Attackers have doubled down on utilizing exploits because the preliminary entry level for assaults, with 38% of assaults Mandiant investigated the place it may decide an preliminary vector beginning with an exploit. Phishing, a distant second place, accounted for 17% of the preliminary actions in an assault. Operating a detailed third, prior compromises inadvertently left exploitable accounted for 15% of all preliminary entry vectors.
“Attackers continue to leverage effective tactics to gain access to target environments and conduct their operations,” the Mandiant report said. “While the most popular infection vectors fluctuate, organizations must focus on defense-in-depth strategies. This approach can help mitigate the impact of both common and less frequent initial intrusion methods.”
Lastly, Mandiant investigators have additionally seen information leak websites (DLS) enhance over time, which now account for greater than a 3rd (36%) of all financially motivated assaults.