The Chinese language state-sponsored hacking group Volt Hurricane has begun to rebuild its “KV-Botnet” malware botnet after it was disrupted by regulation enforcement in January, in response to researchers from SecurityScorecard.
Volt Hurricane is a Chinese language state-sponsored cyberespionage menace group that’s believed to have infiltrated vital U.S. infrastructure, amongst different networks worldwide, since a minimum of 5 years in the past.
Their major technique entails hacking SOHO routers and networking units, reminiscent of Netgear ProSAFE firewalls, Cisco RV320s, DrayTek Vigor routers, and Axis IP cameras, to put in customized malware that establishes covert communication and proxy channels and preserve persistent entry to focused networks.
In January 2024, the U.S. authorities introduced the disruption of Volt Hurricane’s botnet, which concerned wiping malware from contaminated routers.
Though Volt Hurricane’s preliminary revival try in February failed, stories of the menace actors exploiting a zero-day vulnerability in August indicated that the menace group remained very a lot alive.
In keeping with a report by SecurityScorecard, Volt Hurricane has began to rebuild its botnet by concentrating on outdated Cisco and Netgear routers and has compromised a major variety of units in simply over a month.
These routers are compromised utilizing MIPS-based malware and webshells that talk over non-standard ports, making detection more difficult.
Supply: SecurityScorecard
Volt Hurricane is again in motion
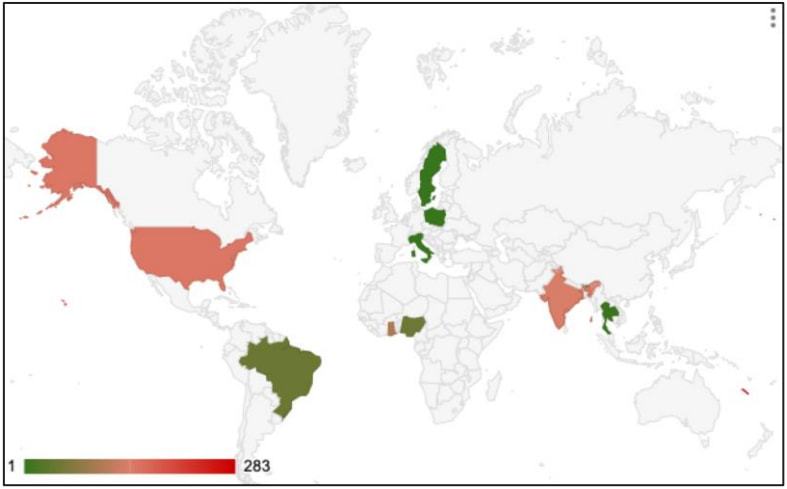
SecurityScorecard stories that, since September, Volt Hurricane has returned by way of a brand new community of compromised units primarily situated in Asia.
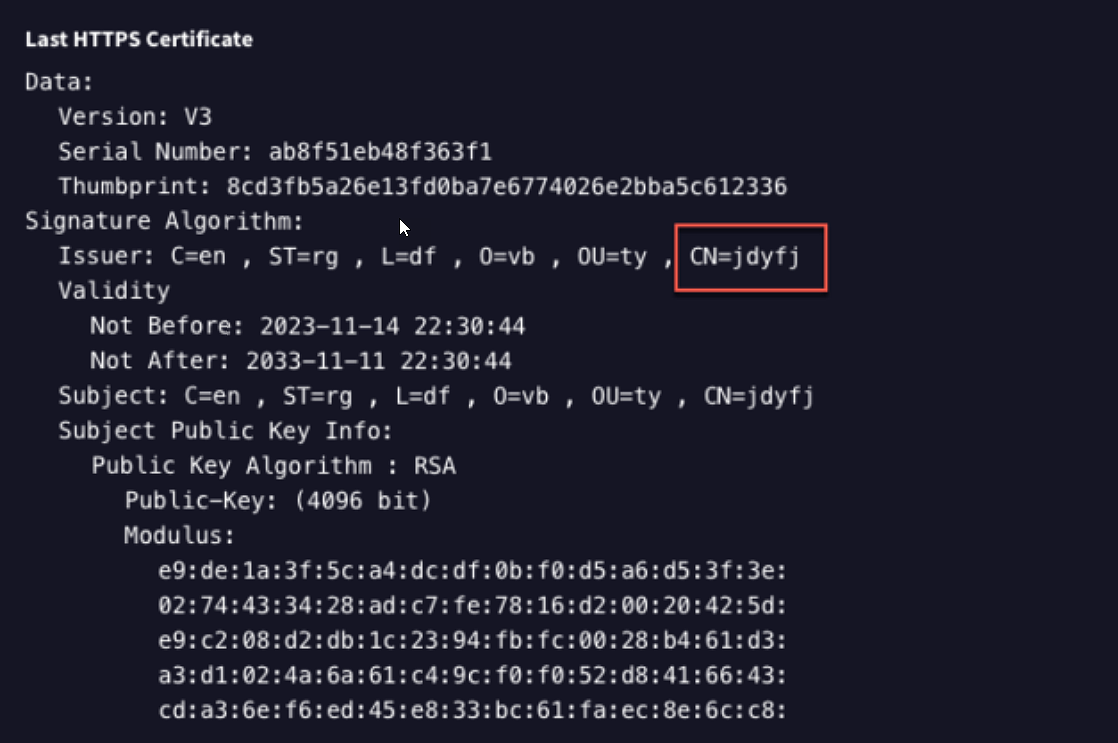
The KV-Botnet, additionally dubbed ‘JDYFJ Botnet’ by SecurityScorecard because of the self-signed SSL certificates seen within the compromised units, makes an attempt to primarily compromise Cisco RV320/325 and Netgear ProSafe collection units.
Supply: SecurityScorecard
SecurityScorecard’s STRIKE Crew researchers say that, in simply 37 days, Volt Hurricane has compromised roughly 30% of all internet-exposed Cisco RV320/325 units. Nonetheless, it’s not recognized right now how the units are breached.
“We don’t know specifically what weakness or flaw is being exploited. However with the devices being end of life, updates are no longer provided,” the researchers advised BleepingComputer.
Additionally, the researchers advised BleepingComputer that they haven’t any perception into what malware is used within the revived botnet. Nonetheless, they famous that among the similar units that have been contaminated earlier than the crackdown joined the cluster once more.
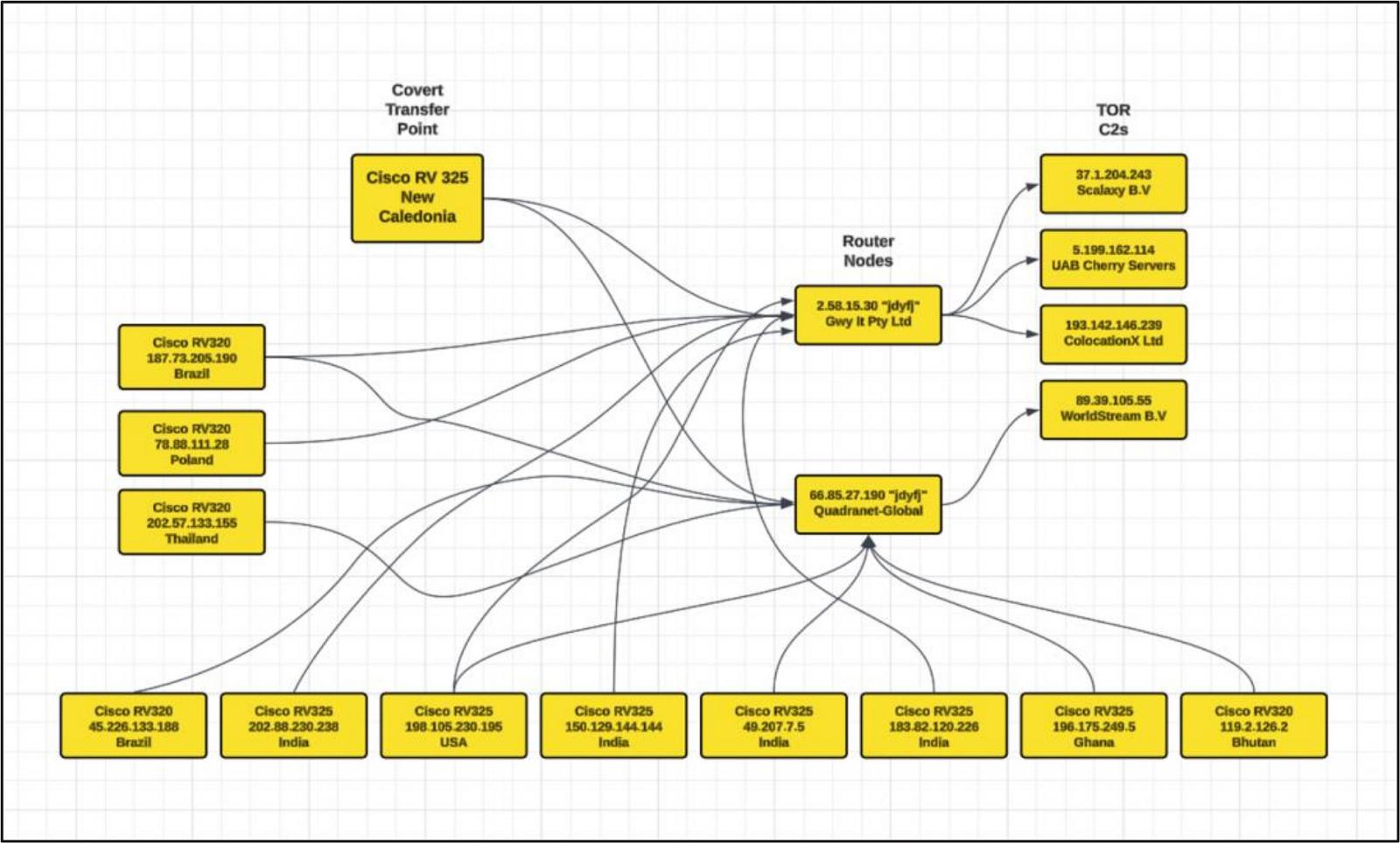
The primary operation of the KV-Botnet seems to be obfuscating malicious actions by routing visitors by way of the compromised official infrastructure.
The botnet’s command servers are registered on Digital Ocean, Quadranet, and Vultr, to realize a extra numerous and resilient community.
Apparently, Volt Hurricane makes use of a compromised VPN machine situated within the Pacific island of New Caledonia as a bridge that routes visitors between Asia-Pacific and America, appearing as a stealthy hub.
Commenting on this alternative, SecurityScorecard advised BleepingComputer that it is possible a geography-based determination from the menace actors.
Supply: SecurityScorecard
The noticed exercise signifies Volt Hurricane’s return to international operations, and though the size of the botnet is nowhere close to earlier iterations, the Chinese language hackers are sure to push ahead with continued persistence.
To guard towards this menace, older and unsupported router units needs to be changed with newer fashions, positioned behind firewalls, distant entry to admin panels shouldn’t be uncovered to the web, and default admin account credentials needs to be modified.
If you’re utilizing newer SOHO routers, you should definitely set up the most recent firmware because it turns into accessible to repair recognized vulnerabilities.