Created by John Tuckner and the crew at automation and AI-powered workflow platform Tines, the SOC Automation Functionality Matrix (SOC ACM) is a set of strategies designed to assist safety operations groups perceive their automation capabilities and reply extra successfully to incidents.
A customizable, vendor-agnostic instrument that includes lists of automation alternatives, it has been shared and advisable by members of the safety neighborhood since its launch in January 2023, notably by Airbnb engineer Allyn Stott in his BSides and Black Hat speak, How I Realized to Cease Worrying and Construct a Fashionable Detection & Response Program.
The SOC ACM has been in comparison with the MITRE ATT&CK and RE&CT frameworks, with one person saying, “it could be a standard for classification of SOAR automations, a bit like the RE&CT framework, but with more automation focus.” It has been utilized by organizations in Fintech, Cloud Security, and past, as a foundation for assessing and optimizing their safety automation applications.
Right here, we’ll take a more in-depth take a look at how the SOC ACM works, and share how you should utilize it in your group.
What’s the SOC Automation Functionality Matrix?
The SOC Automation Functionality Matrix is an interactive set of strategies that empower safety operations groups to reply proactively to widespread cybersecurity incidents.
It isn’t a listing of particular use instances associated to anyone services or products, however a method to consider the capabilities a corporation may comply with.
It affords a stable basis for novices to know what’s potential with safety automation. For extra superior applications, it serves as a supply of inspiration for future implementations, a instrument to gauge success, and a method to report outcomes.
Whereas the instrument is vendor-agnostic, it pairs nicely with a platform like Tines, which was developed by safety practitioners to assist fellow safety practitioners improve their mission-critical processes by way of workflow automation and AI
How does the SOC Automation Functionality Matrix work?
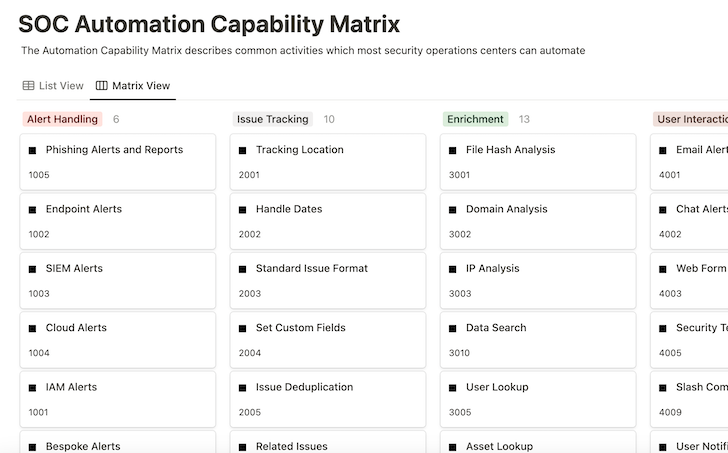
The SOC ACM is cut up into classes that include automation capabilities.
Every functionality contains:
- Description – a short overview of what the aptitude is doing
- Methods – technology-agnostic concepts for how you can implement the aptitude
- Examples – related workflow templates from the Tines library
- References – different analysis contributing to the aptitude
The framework reads from left to proper and prime to backside inside classes. Whereas it’s minimally opinionated about which capabilities deliver essentially the most worth or are simpler to implement, the framework is adaptable to what organizations discover most respected.
Every functionality can stand alone within the matrix, however becoming a member of many capabilities collectively can produce many extra complicated and impactful outcomes.
use the SOC Automation Functionality Matrix
Subsequent, we’ll illustrate how you can use the SOC ACM, taking phishing response as our instance. Many organizations make the most of a number of strategies to search out and analyze suspicious messages to reply appropriately to malicious emails.
To begin, listed below are some processes a routine phishing investigation may embody:
- Obtain a phishing electronic mail or alert
- Ship a notification to the safety crew for processing
- Create a ticket to trace and document the evaluation
- Overview the weather of the e-mail, together with attachments, hyperlinks, and electronic mail message headers
- If suspicious, delete the e-mail and add options to blocklists
- Ship a notification to the recipient with a standing replace
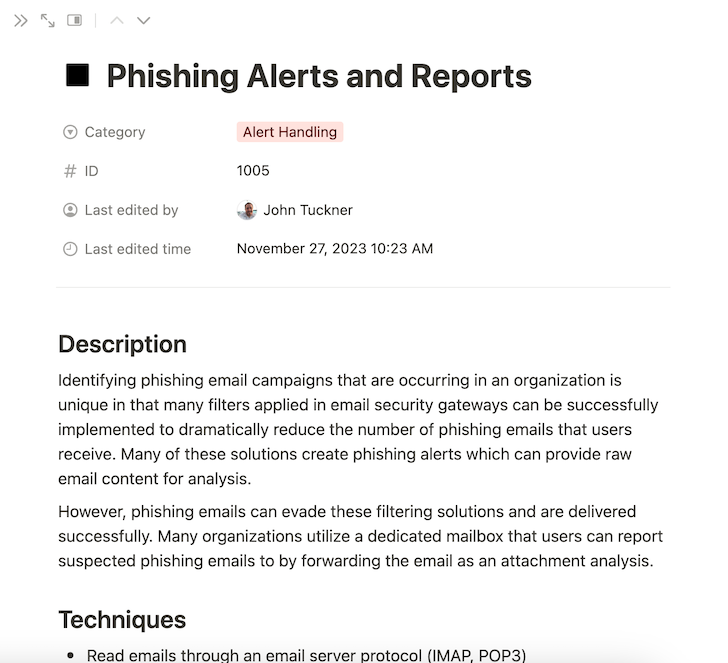
Throughout the matrix functionality, Phishing Alerts seem within the Alert Dealing with part; it mentions that many organizations implement instruments like electronic mail safety gateways to stop suspicious emails from being delivered to inboxes whereas additionally producing alerts of assault campaigns that might be automated.
The aptitude additionally outlines a technique to create a purposeful inbox for customers to simply ahead phishing emails which will have handed by way of the filters. Implementing each of those capabilities affords a possibility to start an automation workflow.
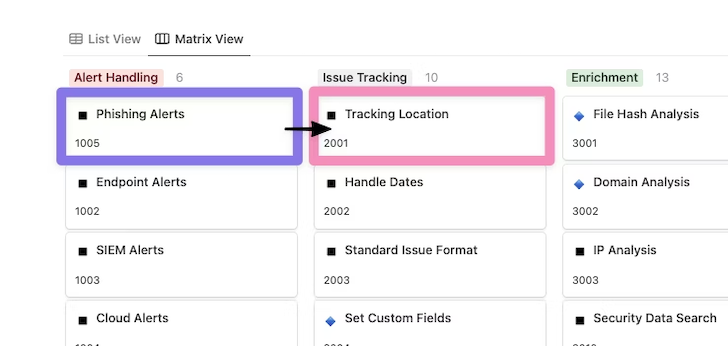
As soon as a suspicious message has been recognized, both by way of the person reporting or generated alert, extra automation capabilities grow to be obtainable. One suggestion is to create a location for monitoring the lifecycle of every alert as quickly as potential.
Using the Monitoring Location functionality within the Difficulty Monitoring part, we are able to establish the place these alerts needs to be recorded, up to date, and reported. Discover how the workflow has now moved between sections of the Automation Functionality Matrix to increase the method.
With the alert and monitoring location selected, we are able to transfer in direction of performing a radical evaluation of the phishing alert in query. Phishing emails generally include probably malicious attachments and suspicious hyperlinks to seize authentication materials and are sometimes despatched from spoofed sources.
Transferring into the Enrichment part, we wish to concentrate on using just a few key capabilities at a minimal: Area Evaluation for any hyperlinks current within the electronic mail physique, File Hash Evaluation/File Evaluation to have a look at any attachments to the e-mail, and E mail Attributes to look deeper into electronic mail headers for indicators of emails from spoofed addresses.
For Enrichment alternatives, the variety of choices for API-driven instruments and providers that can be utilized to offer these capabilities grows exponentially. Some widespread choices embody VirusTotal for recordsdata, URLscan for domains, and EmailRep for sender data. Every of those enrichment outcomes will be recorded within the related monitoring location recognized beforehand to doc the outcomes and supply analysts with a view into the outcomes.
This reveals what number of capabilities from the identical part will be utilized to the identical automation workflow, on this case, to offer as a lot data as potential to analysts.
After enrichment happens, a verdict may be reached already, however extra possible, the difficulty would require a fast evaluation from an analyst. At this level, the Consumer Interplay part turns into crucial.
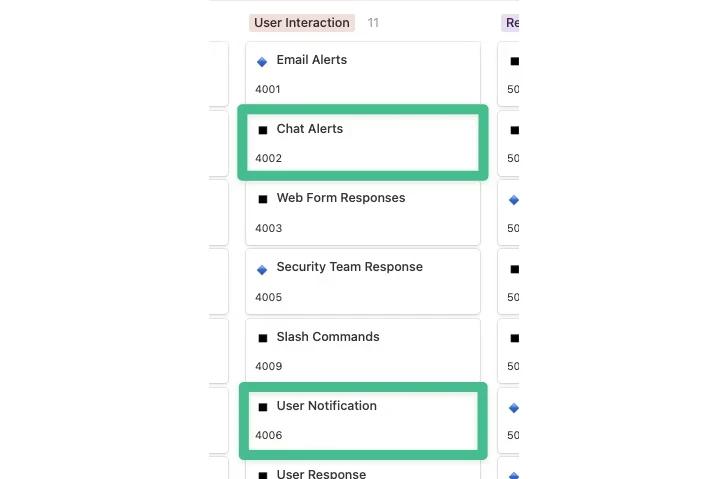
To begin, we are able to use Chat Alerts to inform the safety crew in a Slack channel {that a} phishing electronic mail has arrived and a monitoring concern has been created, with numerous enrichment particulars added as further context is prepared for evaluation.
That takes care of informing the safety crew, however what about updating any customers who may be impacted or who reported the e-mail? Phishing response processes, specifically, are distinctive as a result of many organizations actively prepare customers to report emails they could establish as suspicious. Informing these customers with a assured verdict inside a brief timeframe is an effective way to empower operations akin to getting delicate paperwork signed shortly or stopping mass malware outbreaks.
To do that, we are able to use the Consumer Notification functionality to establish the person who reported the e-mail and supply them with the outcomes of the e-mail evaluation. Within the case of Consumer Interplay, it is not solely about further notification of the safety crew but in addition extending the attain and empowering others with real-time data to make the fitting selections.
At this level, a variety of exercise has taken place, and we now have a variety of data at our disposal. Whereas extra data is all the time useful, appearing on it appropriately is what in the end counts most, ensuing within the remediation part. Lots of the information factors (indicators) we gathered earlier than can be utilized for remediation motion. Relying on how the state of affairs has performed out, we might take a few of the following steps:
- Area blocklist: Add any domains and URLs recognized as suspicious to a blocklist.
- File hash blocklist: Add any file hashes recognized as malicious to a blocklist.
- E mail deletion: Take away emails associated to an assault marketing campaign from inboxes.
- Password invalidation: Change the passwords of any customers discovered to have submitted credentials to a phishing web site.
The important thing to any remediation is realizing what’s potential and beginning small, particularly when using automation to construct confidence. A technique to do that is to offer hyperlinks or buttons that have to be manually clicked to take remediation actions, however in a repeatable method. If you wish to introduce full automation, protecting lists of suspicious domains that may be blocked gives you with nice utility, minor danger, and will be fastened shortly with little general influence when errors happen.
Wanting on the course of end-to-end, we now have utilized the next capabilities to assist automate crucial actions for a lot of cybersecurity groups:
- Phishing alerts
- Monitoring location
- File hash evaluation
- Area evaluation
- E mail attributes
- Chat alerts
- Consumer notification
- Area blocklist
- File hash blocklist
- E mail deletion
- Password invalidation
A big good thing about creating these capabilities in your group to deal with a single course of, akin to phishing, is that many of those capabilities at the moment are obtainable to be reused for extra functions like malware detection or dealing with suspicious logins, making every subsequent automation alternative simpler.
Customizing the matrix
The SOC ACM can also be obtainable on GitHub for many who favor to run it themselves or contribute.
This manner, the SOC ACM will be totally custom-made to suit your wants. This consists of:
- Including new classes and capabilities
- Reorganizing in response to your priorities
- Monitoring automation workflows that align with these capabilities
- Exporting the configuration
- Darkish and light-weight mode
You too can assess completely different environments or completely different organizations otherwise by creating separate boards. For instance, in case your group acquires an organization with completely different capabilities from yours, you should utilize the matrix to visualise that surroundings fully otherwise.
All of this configuration will be saved domestically in your browser for privateness. In addition to exporting the configuration, you possibly can import it to revive previous assessments, all and not using a login account, and with none monitoring.
The SOC ACM as a reporting instrument
Groups accessing the SOC ACM on GitHub may also use the matrix to visually exhibit the place they’re of their automation journey and talk the worth of their automation program to management and different key stakeholders.
Quickly after implementing just a few capabilities, groups will perceive which capabilities they’re using most, the related actions, and their worth, akin to time saved or diminished response time. This allows them to share outcomes with related groups and determine what to prioritize subsequent.
Case research: monitoring time saved and executions to point out worth with the SOC ACM
On the Tines Roadshow: San Francisco, the creator of the SOC Automation Functionality Matrix, John Tuckner, shared how he labored with a Fintech firm to evaluate and improve their automation program utilizing the matrix. They advised Tuckner, “The Automation Capability Matrix helps us organize our workflows, identify which workflows are saving us the most time, and highlight future areas of opportunity.”
Highlights:
- 25 capabilities carried out and tagged
- 10 workflows using Slack slash instructions with 2,000 executions
- Ship multifactor immediate workflows ran 721 instances for six.5 hours of time financial savings per thirty days
Suggestions:
- Take a look at managing lists of IOCs for response capabilities, “IP list,”https://thehackernews.com/2024/02/”domain list,” and “hash list.”
- Doc and spotlight the efforts made in time saved when using case administration.
Future state – what they’re going to do otherwise:
- Tackling distributed alerting, person interplay by way of Slack
- Consumer notification
- Consumer response
- Updating safety Slack channel and incident reporting to make use of a Slack bot and route stories and asks to the proper subteam
- Notify emergency assets
- Timed escalations
- Slash instructions
- Add extra response actions by way of Tines automation by way of our Slack bot
- Artifact gathering
- Disabling MFA machine
- Asset lookup (not simply endpoints, want to incorporate cloud belongings)
The SOC Automation Functionality Matrix is a helpful useful resource for groups in any respect phases of their automation journey, offering inspiration for his or her subsequent automation builds and a method to evaluate their automation program.
If you would like to discover the SOC Automation Functionality Matrix in additional element, you will discover it on Notion, hosted by the Tines crew.