In an organization, who owns the cloud? It’s not all the time clear. Possibly a greater query is: who’s liable for the cloud’s value? That reply is all the time the top of Operations. This particular person might be titled as ‘DevOps,’ or working a ‘Platform’ crew – the title doesn’t matter. That is the particular person whose job it’s to verify there’s a cloud atmosphere that 1) is very accessible for improvement initiatives, 2) is sufficiently architected for present and future efficiency wants, and three) prices about as a lot to run as the corporate thought it might value to run.
Operations: all of the possession, not one of the management
Today, this particular person is in a little bit of a bind.
Think about: you’re a price heart, however you’re feeding what’s perceived because the heartbeat of revenue for many firms (new software program improvement). Your foremost grievance from above you is about value. Price comes from cloud belongings being spun up. The revenue heart (dev) is creating new belongings on a regular basis – they must, the enterprise needs them to; there’s no downward stress on useful resource use for them. And you’ve got little to zero management over them utilizing new sources. Oftentimes, you discover out about new service utilization afterwards – when the cloud invoice comes. So a very powerful factor the upper ups are asking you to do is countermanded by what they’re asking another person to do, and you may’t exert management earlier than utilization happens. That’s not a great scenario.
The cloud is inherently tough to stock or management
How we bought right here is not any thriller: the explanation to maneuver to cloud was the inherent dynamism, the fast availability and scalability of recent sources and companies. To the enterprise, this was intoxicating. So was the speedy enlargement of companies from the cloud service suppliers. It’s not a webpage with S3 and cloudfront anymore. Main CSPs (AWS, Azure, GCP) have over 600+ companies, and so they all include new distinctive permissions. Areas have exploded as effectively – AWS alone has 34 areas and 108 availability zones. CSPs launch new stuff often sufficient that in case you common it out, you see 17 new sorts of cloud permissions per day. Do you utilize all of them? Good luck monitoring in case you do.
The cloud operations particular person is tasked with holding prices down and holding issues safe. However downstream of that, the ops particular person wants readability and order. Most operations folks don’t have an correct cloud stock. It’s not attainable whenever you in all probability inherited the infrastructure you’re managing, and also you don’t have a governor on new sources. There’s not an correct stock of cloud sources. There’s a lot to trace and an excessive amount of utilization occurs with out the particular person liable for utilization ever figuring out. What’s sorely lacking: guardrails stopping unknown utilization earlier than it occurs.
Right here’s a spot to start out: what in case you may simply flip off cloud companies and areas that you recognize you don’t use?
A attainable management level: Companies and Areas
As an Ops particular person, if you end up on this mess, you’ve gotten a number of choices:
- Painstakingly stock each cloud asset.
- Decide to a continuing maintenance of recent companies. Try to preempt utilization if deemed out of scope or risk-inducing.
- Cease the bleeding, let folks use what they want, however set central guardrails round that. Future-proof towards additional unsanctioned utilization with ‘default deny’ and approval system.
Up to now, most Ops of us have tried some mixture of #1 and #2. It’s pure to really feel the pull of attending to an correct cloud manifest, if solely you had a little bit extra time to maintain cleansing up and documenting it. Possibility 3 hasn’t been accessible, as a result of there’s no clear solution to centralize controls that doesn’t threaten to interrupt code. There’s not even cloud-specific a manner to verify companies are turned ‘off’ in case you’re not utilizing them – actually no solution to flip them off for everybody not utilizing them presently.
But we are able to unlock choice 3 if we consider it as a permissions drawback. It begins with the straightforward motion of turning off companies you don’t use.
Permission, not forgiveness
A standard state of affairs: a scorching new AI service has come on-line. The enterprise is keen to see how it may be included into present choices. As standard, a developer will first mess around with it, attempting it out in a sandbox atmosphere. Operations hasn’t vetted it, has no thought what it can value, and won’t be notified when it will get turned on. What if we are able to cease the utilization proper there – as a substitute of the ops lead discovering out about post-usage, they get requested for permission to make use of it. If we give the Operations lead an ‘off’ button for the brand new service, and arrange a manner for the developer to request entry to the service. That manner, the ops particular person is aware of precisely what it’s and what utilization to anticipate.
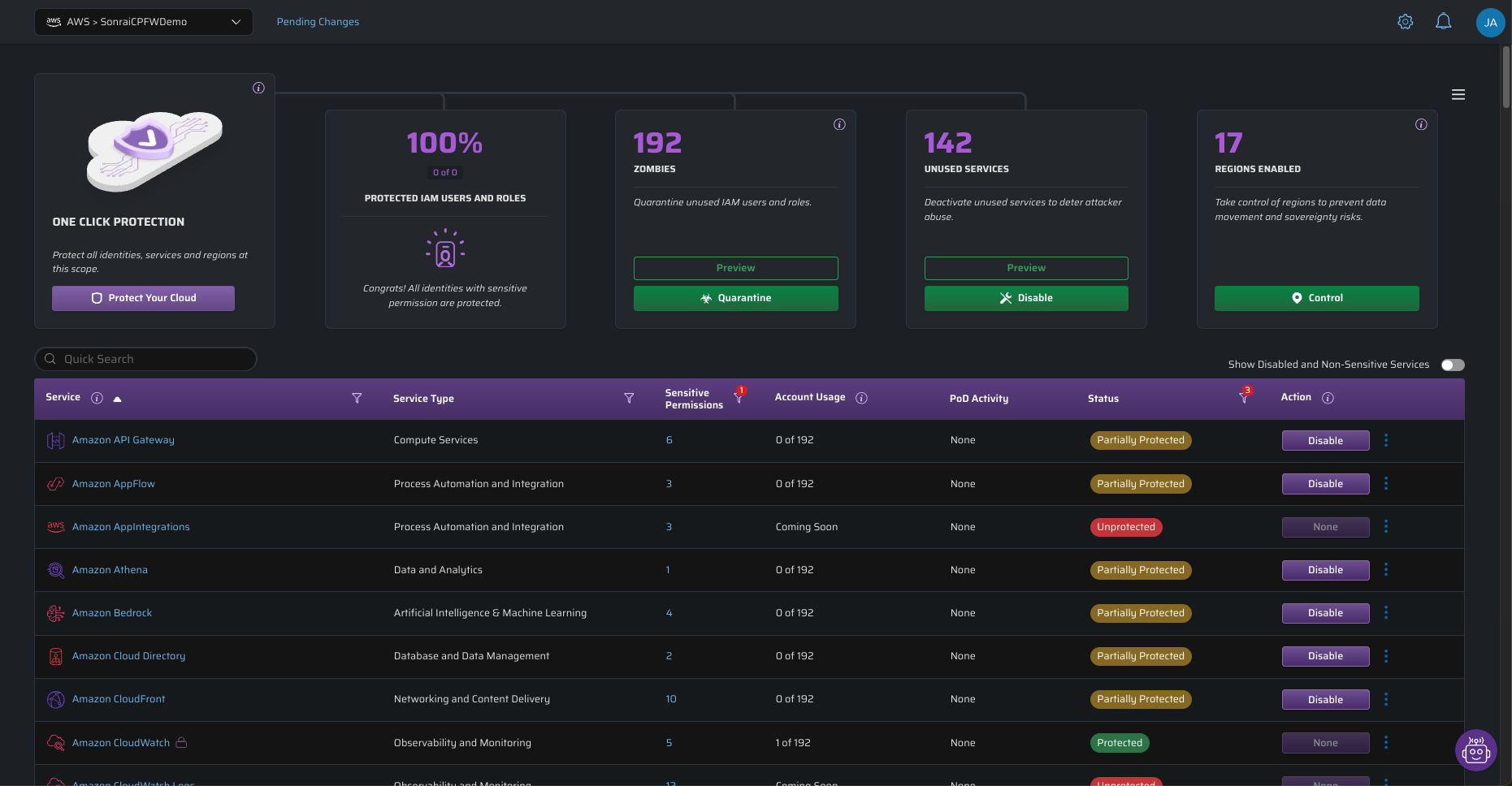
The identical goes for availability areas. Should you’re a US-based firm without having for AWS’s APAC-Tokyo area, why make it accessible? It’s simply one other place for rogue utilization to occur – to not point out any information sovereignty violations that you could fear about.
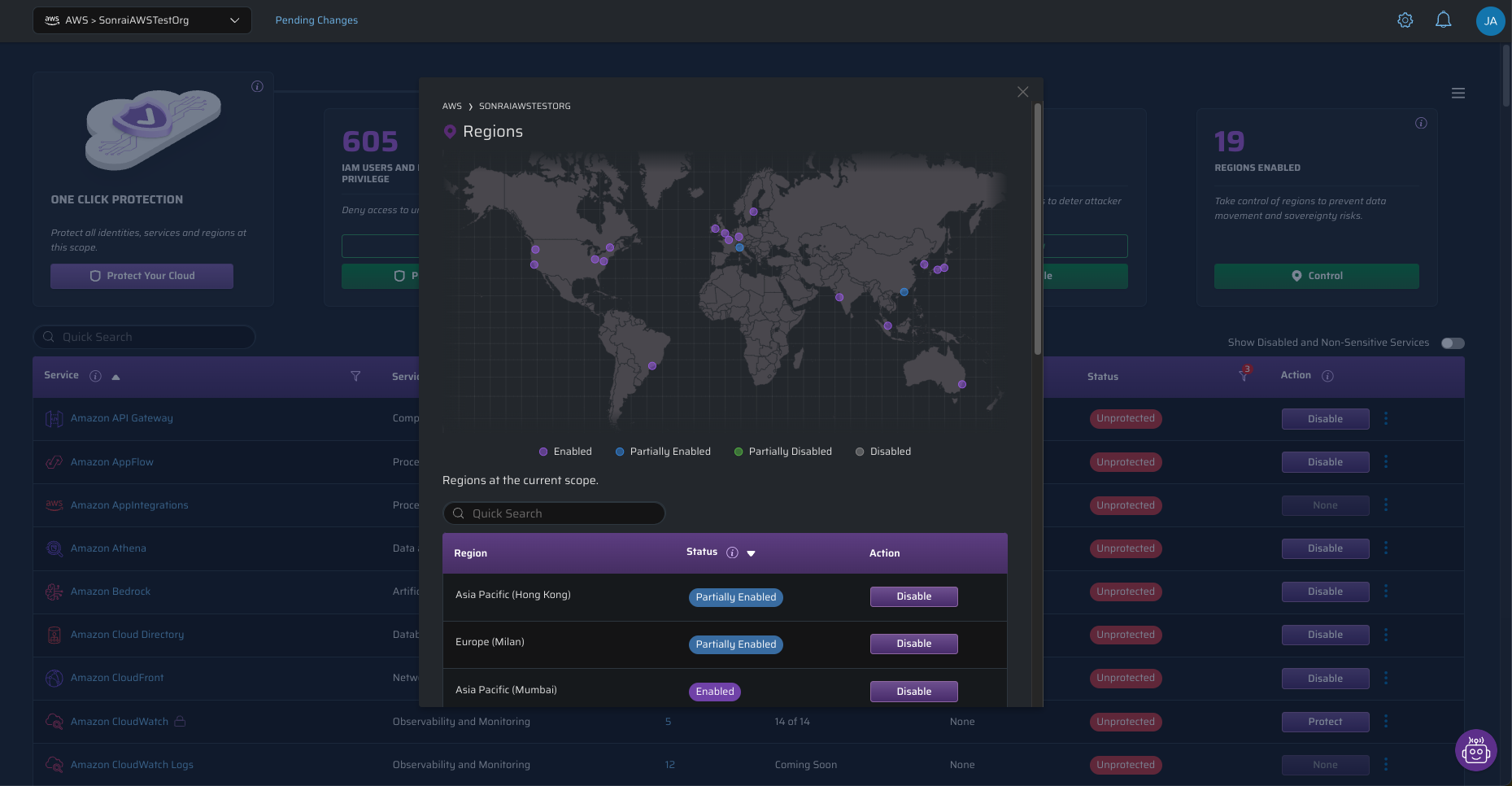
Sonrai’s Cloud Permissions Firewall offers you these controls. Wish to disable new AI companies? Hit that disable button, and so they’re restricted at no matter scope (org, OU, accounts) you establish. Wish to solely flip off delicate permissions (aka, actions that may possible be utilized in an assault)? Hit the Shield button. The purpose is: it’s a central management for companies that’s within the possession of the cloud proprietor, as a substitute of each developer selecting how and when companies get utilized.
When somebody does need to open up use of a service, there’s a easy, ChatOps-integrated course of for them doing so.
How permissions are a part of FinOps
Along with simply turning companies off to regulate utilization earlier than it occurs, having a centralized permissions management offers you a solution to examine how unseen utilizations came about.
Monitoring down rogue prices in your invoice begins in the identical place you look to show off companies. You’ll be capable of see if the service that incurred the cost is protected, and if any identification has exempted standing to make use of delicate permissions in it.
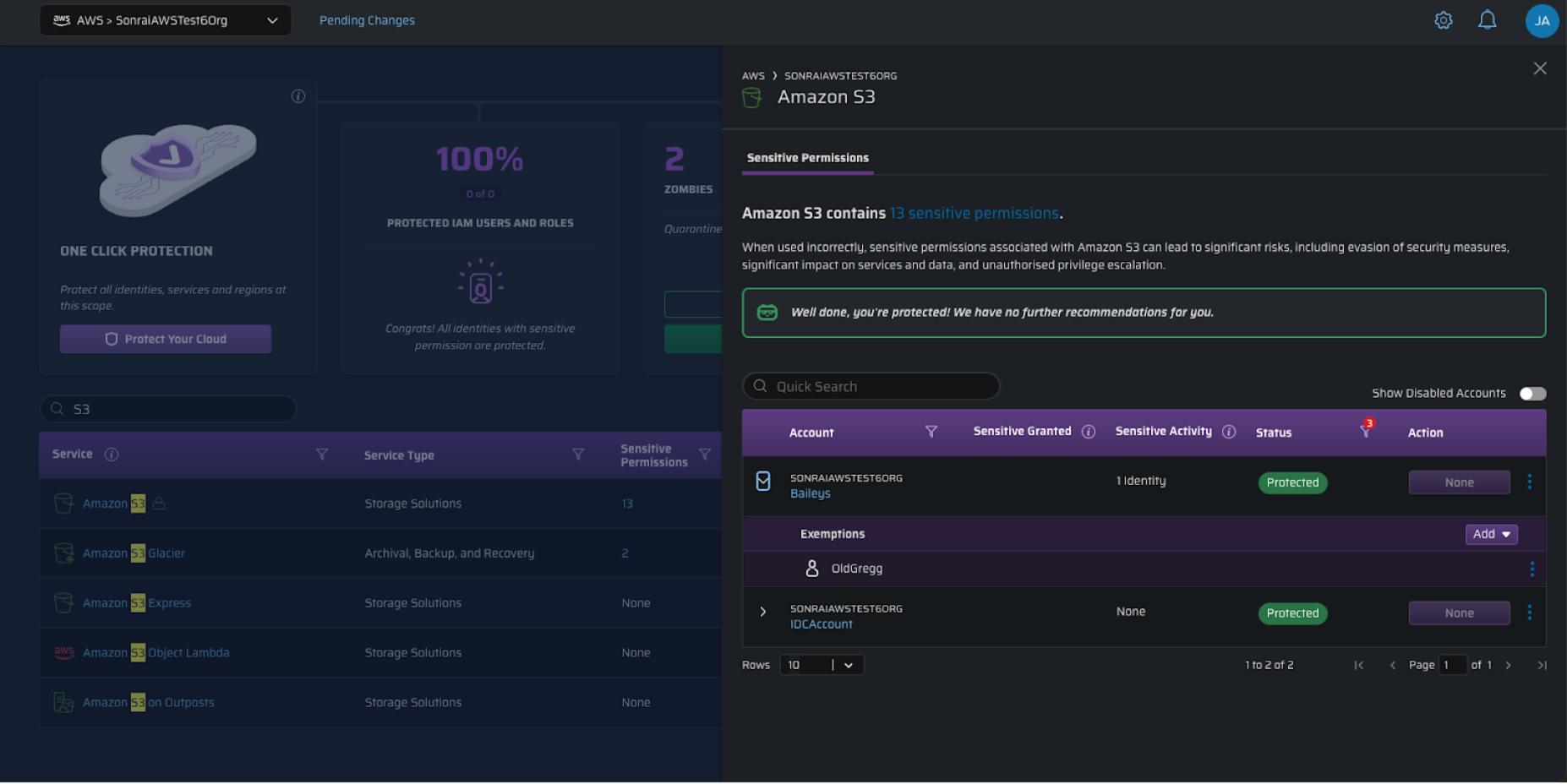
Now now we have the ARN to lookup in our repo to see what this was linked to, and why they used it. You’ve additionally bought an auditable historical past to see if the person requested this entry, who granted it, and when. Whereas the first good thing about this safety is to scale back threat, it additionally offers us a spot to see who can use what. If we do get sudden utilizations, we are able to rapidly examine who’s possible liable for it.
The tip of chaos begins with the ‘off’ button
Anybody liable for working the platform has been mired in an issue begotten of an excessive amount of scale and complexity. Whereas the cloud is undeniably advanced, options to utilization and threat management don’t must be. In our makes an attempt to be extra forward-thinking, cloud professionals – distributors included – have mistaken complexity for robustness. Shifting left, democratized management, developer-led safety – these are all trendy ideas we are able to proceed to bake into our cloud technique. However centralization of easy guardrails, like whether or not a service or a area is accessible, are essential to be within the management of whoever is liable for the platform. You may nonetheless provide straightforward strategies of requesting entry, however finally, the operations particular person is in management. Up till now, cloud instruments have struggled balancing the competing priorities of time-to-production and asset management. Giving some common sense on/off buttons to the operations lead for unused companies and areas is an effective begin in direction of controlling the cloud chaos with out slowing something down.

