Intro
You’re a safety skilled who has been given the duty of managing and mitigating the big selection of vulnerabilities throughout the open supply software program your group makes use of. In a really perfect world, you’d have the time, vitality, and sources obligatory to right away start addressing and fixing each one in every of these vulnerabilities instantly – together with all the brand new ones coming in.
Nevertheless, actuality is sort of completely different. Nobody has all the mandatory sources readily at their disposal. The variety of vulnerabilities in open supply software program is insurmountable. The fact is that it could take an unprecedented period of time, manpower, and monetary sources to sort out each vulnerability.
The one viable answer is to prioritize. So, how do you successfully prioritize your efforts?
Having the proper instruments in your vulnerability administration toolbox is important. That is the place the Exploit Prediction Scoring System (EPSS) is available in.
Understanding EPSS: Enhancing Vulnerability Administration
Developed by the Discussion board of Incident Response and Safety Groups (FIRST) [1], EPSS [2] supplies a data-driven strategy to predicting the chance of a vulnerability being exploited within the wild throughout the subsequent 30 days. By leveraging this industry-recognized normal, organizations could make knowledgeable selections and allocate their restricted sources rather more effectively.
At its core, EPSS is a chance rating starting from 0 to 1 (0 to 100%). A better rating signifies a larger chance of a vulnerability being exploited. However how is that this rating calculated, and what elements does it take into account?
EPSS considers a variety of data, together with:
- Vendor
- Vulnerability age
- References
- Vulnerability description
- Widespread Weak point Enumeration (CWE)
- CVSS metrics
- Varied exploit lists (e.g., CISA KEV, Google Mission Zero, Pattern Micro’s Zero Day Initiative)
By analyzing this knowledge[LZ1] [RG2] and monitoring exploitation exercise by way of varied strategies, resembling honeypots, IDS/IPS sensors, and host-based detection, EPSS supplies a nuanced understanding of the urgency and impression of vulnerabilities. It makes use of machine studying to detect patterns and connections between vulnerability knowledge and exploitation actions gathered over time.
Deciphering EPSS Scores
EPSS knowledge is refreshed every day and gives two key metrics: chance and percentiles.
Chance represents the chance of a vulnerability being exploited within the wild throughout the subsequent 30 days, whereas the percentile signifies the proportion of vulnerabilities which have a rating equal to, or decrease than, a selected vulnerability’s rating.
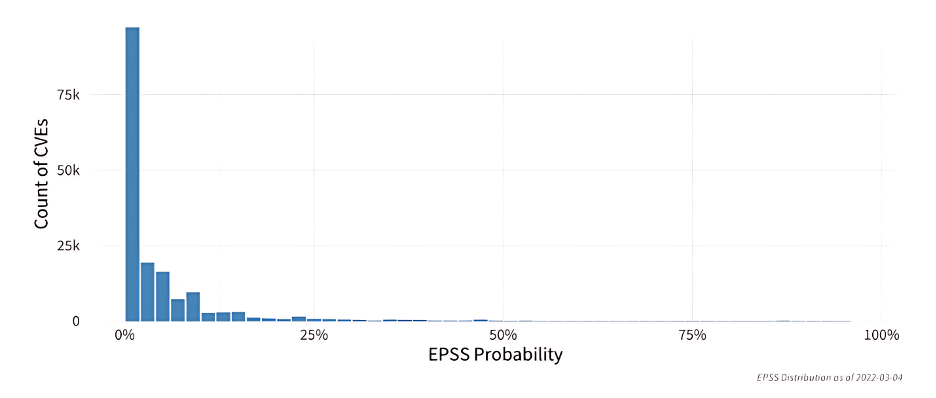
For instance, an EPSS chance of simply 0.10 (10%) rests at concerning the 88th percentile – that means that 88% of all CVEs are scored decrease. These percentiles are derived from chances and provide insights into how a selected EPSS chance compares to all different scores – all the opposite CVEs.
The determine under reveals the chance distribution of EPSS scores for over 170,000 vulnerabilities as of March 2022. It illustrates that the majority vulnerabilities rating under 10%, indicating a world measure of vulnerability exploitation within the wild.
Limitations and Issues
Whereas EPSS is a strong device, it’s important to know its limitations and use it together with different exploitability metrics and menace intelligence. Some key factors to remember:
- EPSS scores are based in gathered knowledge, which suggests they’ll change over time which might introduce errors.
- If there may be proof {that a} vulnerability is being actively exploited, that info ought to supersede EPSS, as EPSS is pre-threat intel, and subsequently could lag behind stay incidents.
- The mannequin solely produces scores based mostly on accessible knowledge, which relies solely on disclosed and recognized incidents – public availability for info the mannequin itself are acknowledged limitations.
- EPSS is a threat administration mannequin – simply because a vulnerability has been exploited prior to now doesn’t assure future exploitation and, conversely, simply because a vulnerability has been recognized for some time and never actively exploited doesn’t assure it is not going to surge quickly.
EPSS Rating vs. CVSS: Understanding the Distinction
EPSS and CVSS (Widespread Vulnerability Scoring System) are each measures to assist organizations handle vulnerabilities, however they serve completely different functions.
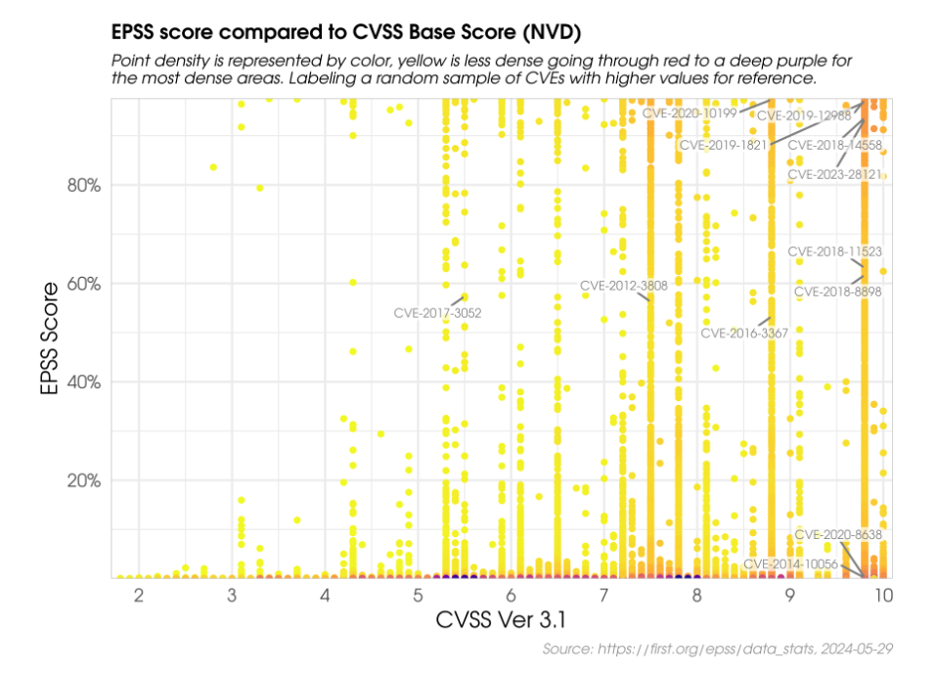
EPSS goals to foretell the chance of a vulnerability being exploited, utilizing a forward-looking and probabilistic strategy. In distinction, CVSS evaluates the severity of a vulnerability by assessing its traits and potential impression, with a descriptive and deterministic strategy.
The graph under reveals the comparability between CVSS and EPSS scores for a pattern of CVEs.
EPSS Worth in Prioritizing Remediation and Threat Administration
EPSS must be handled as one facet of the general vulnerability administration image, complementing different elements like CVSS.
FIRST compares two methods, one prioritizing CVEs with CVSS 7 and better, and one other prioritizing CVEs with EPSS of 0.1 and better.
They in contrast:
Effort – The proportion of vulnerabilities being prioritized for remediation
Effectivity – How effectively sources had been spent by measuring the % of prioritized vulnerabilities that had been exploited.
Protection – The % of exploited vulnerabilities that had been prioritized, calculated because the variety of exploited vulnerabilities prioritized (TP – accurately prioritized) divided by the whole variety of exploited vulnerabilities (TP + FN – accurately prioritized + incorrectly delayed).
By prioritizing vulnerabilities with an EPSS of 0.1 and better, organizations can considerably cut back their remediation effort whereas bettering effectivity.
In addition they analyzed EPSS and CVSS scores to know their correlation [3]. The evaluation confirmed that attackers don’t completely goal essentially the most impactful or easiest-to-exploit vulnerabilities, difficult the belief that they solely give attention to essentially the most extreme ones. Subsequently, it’s beneficial to make use of a mix of things to successfully prioritize which vulnerabilities to patch first.
EPSS at Checkmarx
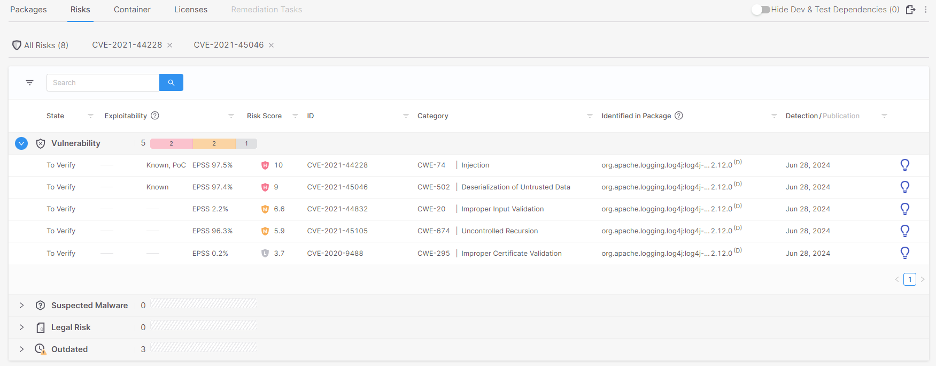
At Checkmarx, we perceive the significance of efficient vulnerability administration. That’s why Checkmarx Clients utilizing the Checkmarx One Platform can leverage the built-in EPSS scores for faster and simpler threat triaging and remediation.
EPSS enhances our current array of exploitability metrics which embody however will not be restricted to:
- KEV (Identified Exploited Vulnerability): A vulnerability cataloged by CISA as a Identified Exploited Vulnerability, indicating that it poses a extreme and imminent menace.
- POC (Proof of Idea): A Proof of Idea for exploiting the vulnerability is obtainable within the wild, making it straightforward for menace actors to implement an exploitation of this vulnerability.
- Exploitable Path: This characteristic analyzes whether or not your supply code supplies a path that may be exploited by a selected vulnerability. Checkmarx SCA leverages SAST’s skill to scan the precise venture code itself in parallel with scanning the manifest file, validating whether or not the susceptible open-source packages are known as out of your proprietary code and whether or not the susceptible strategies are utilized by your code. This allows you to give attention to the remediation of actively exploitable vulnerabilities. Exploitable Path additionally identifies which traces in your venture code attain the susceptible technique within the susceptible package deal and reveals you the complete path to the vulnerability.
By combining these instruments, our prospects can obtain a complete view of their vulnerability panorama and take proactive measures to mitigate dangers with excessive potential to be exploited by malicious actors.
The next shows how EPSS, and different exploitability metrics, are built-in into Checkmarx’ product.
Conclusion
Staying forward of present threats requires a proactive and data-driven strategy. EPSS gives organizations a beneficial device to prioritize their vulnerability administration efforts successfully. By leveraging EPSS alongside different exploitability metrics, safety professionals could make knowledgeable selections, allocate sources effectively, and strengthen their total safety posture.
At Checkmarx, we’re dedicated to offering our prospects with essentially the most complete and cutting-edge vulnerability administration options and empowering organizations to navigate the complicated panorama of open-source vulnerabilities with confidence and precision.
References
[1] FIRST: https://www.first.org/
[2] EPSS: https://www.first.org/epss/
[3] EPSS: Person Information, Utilizing EPSS and CVSS Collectively https://www.first.org/epss/user-guide