Fortinet and Mandiant investigated the mass exploitation of FortiManager gadgets through CVE-2024-47575, impacting 50+ methods throughout industries. Risk actor UNC5820 used the flaw for information theft and unauthorized entry.
Fortinet and Google’s Mandiant collaborated in October 2024 to research the mass exploitation of FortiManager home equipment throughout 50+ probably compromised gadgets throughout numerous industries as a consequence of CVE-2024-47575.
This vulnerability, which permits attackers to execute arbitrary code on compromised FortiManager gadgets, has been actively exploited by a risk group tracked by Mandiant as UNC5820.
FortiManager is a centralized administration answer by Fortinet that allows organizations to handle and configure a number of Fortinet safety gadgets, reminiscent of FortiGate firewalls, from a single interface.
In response to their weblog put up, the assault started on June 27, 2024, and continued by September 22, 2024, with additional information exfiltration and potential persistence makes an attempt. The risk actor exploited the FortiManager vulnerability, utilizing inbound and outbound connections, file creation, and modification to realize unauthorized entry and steal delicate data.
Their major goal appears to be stealing configuration information from compromised FortiManager gadgets. This information included detailed details about managed Fortinet gadgets, usernames, and FortiOS256-hashed passwords.
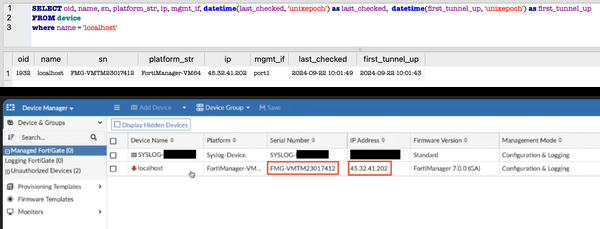
Risk actors exploited weak FortiManager gadgets by connecting to IP tackle 45.32.41.202 on port 541. They staged configuration recordsdata containing vital information about managed gadgets in a compressed archive named /tmp/.tm.
Shortly after, outbound community site visitors was noticed, with various vacation spot IP addresses throughout incidents. In a single case, the risk actor’s gadget was registered with the compromised FortiManager, suggesting an try to determine long-term entry.
The report gives an in depth timeline of noticed attacker exercise, together with particular dates, instances, and community site visitors particulars. This will help establish potential compromises inside your personal surroundings.
Tim Peck, Senior Risk Researcher, Securonix weighed in on the scenario, urging corporations to put in patches.
“The risk posed by CVE-2024-47575 is significant, especially for large enterprises due to its potential for remote code execution. Damages can range from unauthorized access and data theft to critical disruptions,” Tim warned.
“Affected organizations should apply the October 24 patch, review access logs for suspicious activity, and ensure a strong incident response plan. This vulnerability underscores the need for timely patching, network segmentation, and continuous monitoring.”
This assault marketing campaign explains the pattern of cybercriminals leveraging zero-day vulnerabilities to realize unauthorized entry to delicate methods. Up to now, we’ve got seen comparable assaults concentrating on different vital infrastructure parts, reminiscent of routers, firewalls, and industrial management methods.
The exploitation of this FortiManager vulnerability is especially regarding because of the widespread use of FortiGate gadgets in enterprise environments. These gadgets are sometimes used to guard vital infrastructure and information, making them a beneficial goal for attackers.
Potential mitigation measures embrace limiting entry to the FortiManager admin portal to approved inner IP addresses, limiting communication to solely permitted FortiGate gadgets, and denying registration makes an attempt from unknown gadgets.
Google Cloud gives detection guidelines for Google SecOps Enterprise+ clients, and organizations can develop customized SIEM searches primarily based on offered IOCs and monitor FortiManager logs for suspicious exercise.
RELATED TOPICS
- CISA and Fortinet Warns of New FortiOS Zero-Day Flaws
- Hackers Exploiting Crucial Flaws in Fortinet VPN – FBI-CISA
- Hackers dump login Particulars of Fortinet VPN customers in plain-text
- Hackers leak login credentials of weak Fortinet SSL VPNs
- Fortinet Confirms Information Breach as Hacker Leaks 440GB of Information