The favored Ultralytics YOLO11 AI mannequin was compromised in a provide chain assault to deploy cryptominers on units working variations 8.3.41 and eight.3.42 from the Python Bundle Index (PyPI)
Ultralytics is a software program growth firm specializing in laptop imaginative and prescient and synthetic intelligence (AI), particularly in object detection and picture processing.
It is best identified for its “YOLO” (You Solely Look As soon as) superior object detection mannequin, which may shortly and precisely detect and determine objects in video streams in actual time.
Ultralytics instruments are open-source and are utilized by quite a few tasks spanning a variety of industries and purposes.
The library has been starred 33,600 occasions and forked 6,500 occasions on GitHub, and it has had over 260,000 over the previous 24 hours from PyPI alone.
Ultralytics YOLO11 compromised
Yesterday, Ultralytics 8.3.41 and eight.3.42 have been launched to PyPi, and customers who put in the compromised variations immediately or as a dependency found {that a} cryptominer was deployed. For Google Colab accounts, house owners bought flagged and banned resulting from “abusive activity.”
Ultralytics is a dependency of each SwarmUI and ComfyUI, who each confirmed that contemporary installs of their libraries would have led to the set up of the miner.
When put in, the compromised library installs and launches an XMRig Miner at ‘/tmp/ultralytics_runner‘ to hook up with a minin pool at “connect.consrensys[.]com:8080”.

ource: Floresce
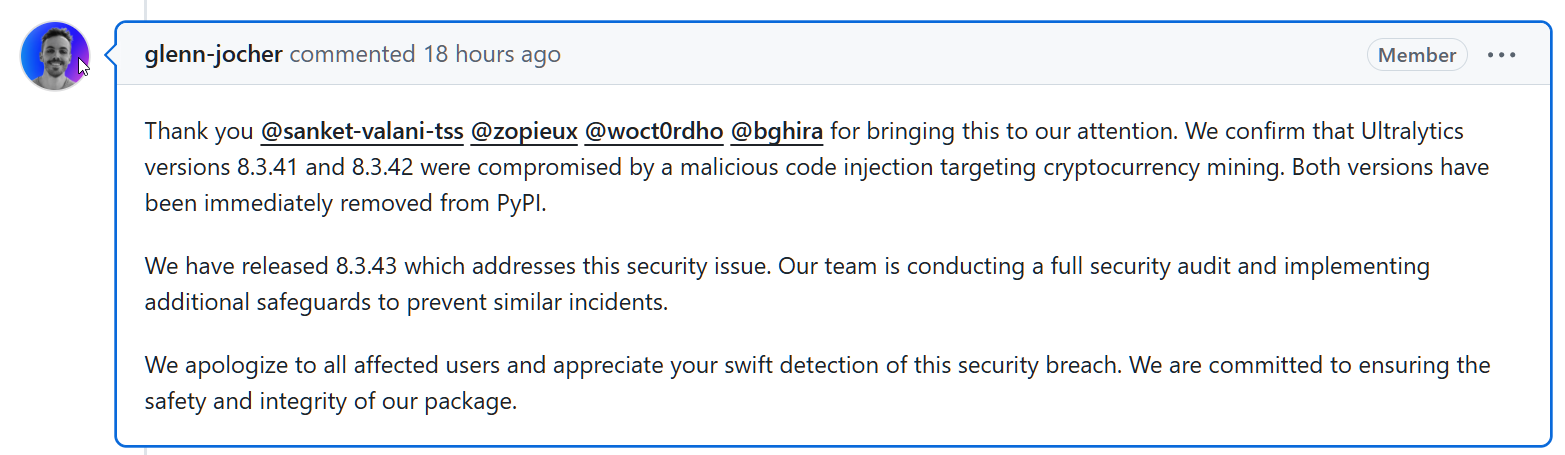
Ultralytics founder and CEO Glenn Jocher confirmed that the difficulty solely impacts these two compromised variations, which have already been pulled and changed with a clear 8.3.43 model.
“We confirm that Ultralytics versions 8.3.41 and 8.3.42 were compromised by a malicious code injection targeting cryptocurrency mining. Both versions have been immediately removed from PyPI,” Jocher posted to GitHub.
“We have released 8.3.43 which addresses this security issue. Our team is conducting a full security audit and implementing additional safeguards to prevent similar incidents.”
Supply: BleepingComputer
The builders are at the moment investigating the foundation trigger, and potential vulnerabilities within the Ultralytics construct atmosphere to find out the way it was breached.
Nevertheless, Jocher commented that the compromise seems to originate from two malicious PRs [1, 2]with code injection within the department names submitted by a consumer in Hong Kong.
Whether or not the malicious code solely carried out crypto mining or compromised non-public consumer knowledge stays unclear, and the group remains to be awaiting a proper advisory relating to the breach that can present clarifications on all particulars.
Out of an abundance of warning, those that downloaded a malicious model of Ultralytics ought to carry out a full system scan.
BleepingComputer has contacted Ultralytics to touch upon the state of affairs and study extra about how the provision chain compromise was achieved, however we’re nonetheless awaiting a response.
