KEY POINTS
- Cybersecurity researchers at ReversingLabs discovered that hackers used malicious code to mix the Ultralytics AI library to mine cryptocurrency.
- Hackers exploited the library’s construct system and injected XMRig mining software program into updates 8.3.41 and eight.3.42.
- The assault used GitHub Actions Script Injection and pretend pull requests to realize entry to the system.
- With over 60 million downloads, the compromised library posed a danger, although the harm was restricted to mining.
- Builders and customers should confirm software program updates and sources to keep away from related incidents.
The most recent analysis from ReversingLabs (RL) shared with Hackread.com, reveals {that a} well-liked AI library referred to as “Ultralytics“ has been secretly mining cryptocurrency for another person. This follows the current discovery of the malicious aiocpa Python bundle, which was spreading an infostealer.
On December 4th, an replace (model 8.3.41) for Ultralytics hit the Python Bundle Index (PyPI), a repository for Python software program. Nonetheless, one thing else additionally hit the repository: Hackers had infiltrated the mission’s construct atmosphere, which prepares the software program for launch.
The content material within the GitHub repository didn’t match the content material of the matching PyPI bundle, as malicious actors compromised the construct atmosphere and injected malicious code after the code evaluate course of was accomplished.
The tampered code downloaded a program referred to as XMRig, a cryptocurrency miner. The worst half, in keeping with RL’s report, is that even a supposed “fix” (model 8.3.42) launched the following day was additionally contaminated.
That’s as a result of the mission’s maintainers didn’t find the compromise, leading to model 8.3.42, meant to handle the incident and function a secure improve, containing the identical malicious code. A clear model, 8.3.43, was launched on the identical day, resolving this provide chain assault.
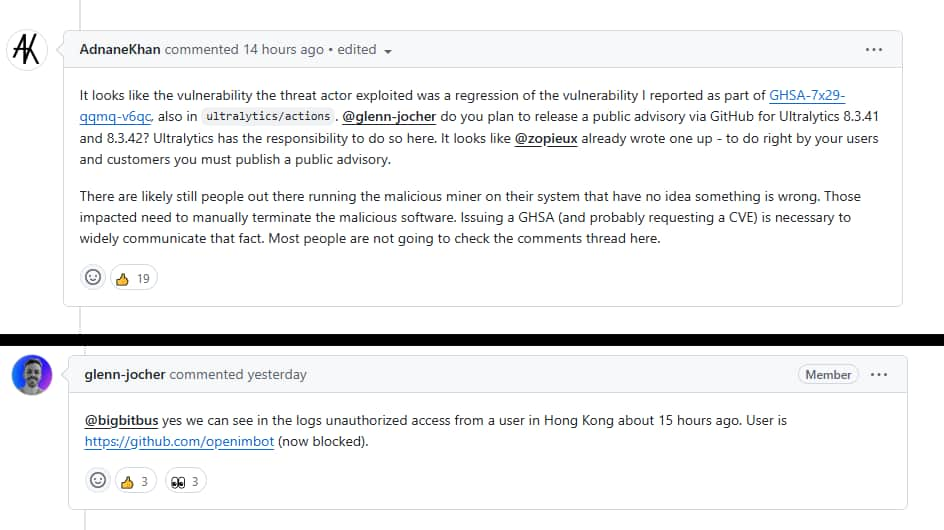
In case you’re questioning how the hackers obtained in, it began with exploiting a GitHub Actions Script Injection to enter the construct atmosphere of a trusted npm bundle, @solana/web3.js. This injection allowed a malicious actor to create a fork of any repository utilizing ultralytics/actions and craft a pull request from a department with injection payload code in its title.
Subsequent, two maliciously crafted pull requests, #18018 and #18020, have been designed to allow backdoor entry to the compromised atmosphere. The person account behind this pull request, openimbot, and the distant connection established after the execution of the malicious payload have been initiated from Hong Kong, based mostly on info supplied by ultralytics maintainers. By creating pretend pull requests with cleverly crafted titles, actors tricked the system into working their malicious code.
Affect: 60 million downloads and 30,000 GitHub stars
This assault had the potential to influence thousands and thousands contemplating that Ultralytics boasts over 60 million downloads and 30,000 GitHub stars, indicating its widespread use. Fortunately, the harm appears restricted to cryptocurrency mining.
Nonetheless, this incident reveals how weak software program provide chains will be. Malicious actors might have simply injected extra harmful code, like backdoors or distant entry instruments. This implies, builders should be cautious in any respect levels to guard AI tasks.
It additionally reveals the significance of software program safety, emphasizing the necessity for builders to double-check code modifications from untrusted sources, and customers to obtain software program from trusted sources and preserve it up to date.