The Pc Emergency Response Workforce of Ukraine (CERT-UA) experiences a few new marketing campaign dubbed “SickSync,” launched by the UAC-0020 (Vermin) hacking group in assaults on the Ukrainian protection forces.
The risk group is linked to the Luhansk Individuals’s Republic (LPR) area, which Russia has occupied nearly in its entirety since October 2022. The hacker’s actions generally align with Russia’s pursuits.
The assault makes use of the respectable file-syncing software program SyncThing together with malware referred to as SPECTR.
Vermin’s obvious motive is to steal delicate data from navy organizations.
Assault particulars
The assault begins with a phishing e mail despatched to the goal, carrying a password-protected RARSFX archive named “turrel.fop.wolf.rar.”
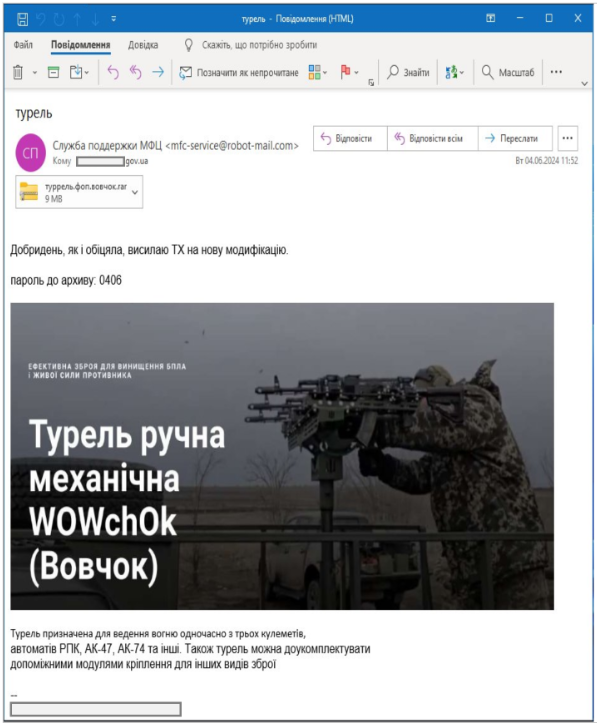
Supply: CERT-UA
Upon launching the file, it extracts a PDF (“Wowchok.pdf”), an installer (“sync.exe”), and a BAT script (“run_user.bat”). The BAT executes sync.exe, which accommodates SyncThing and SPECTR malware, together with the required libraries.
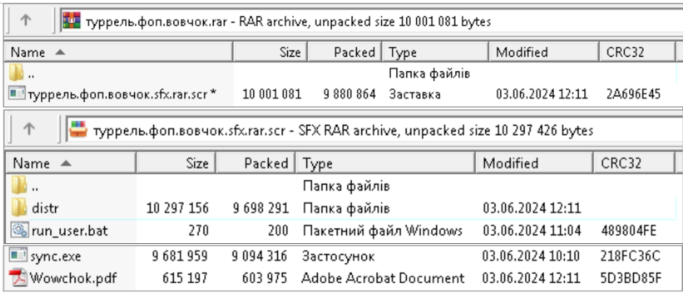
Supply: CERT-UA
SyncThing establishes a peer-to-peer connection for information synchronization, which is used for stealing paperwork and account passwords.
The respectable software is modified with new listing names and scheduled duties to evade identification, whereas the element that shows a window when it is energetic has been eliminated.
SPECTR is a modular malware that has the next capabilities:
- SpecMon: Calls PluginLoader.dll to execute DLLs containing the “IPlugin” class.
- Screengrabber: Takes screenshots each 10 seconds when particular program home windows are detected.
- FileGrabber: Makes use of robocopy.exe to repeat information from consumer directories akin to Desktop, MyPictures, Downloads, OneDrive, and DropBox.
- Usb: Copies information from detachable USB media.
- Social: Steals authentication information from numerous messengers like Telegram, Sign, Skype, and Component.
- Browsers: Steals information from browsers together with Firefox, Edge, and Chrome, specializing in authentication information, session data, and searching historical past.
Information stolen by SPECTR is copied into subfolders throughout the ‘%APPDATApercentsyncServe_Sync’ listing and subsequently transferred by syncing to the risk actor’s system.
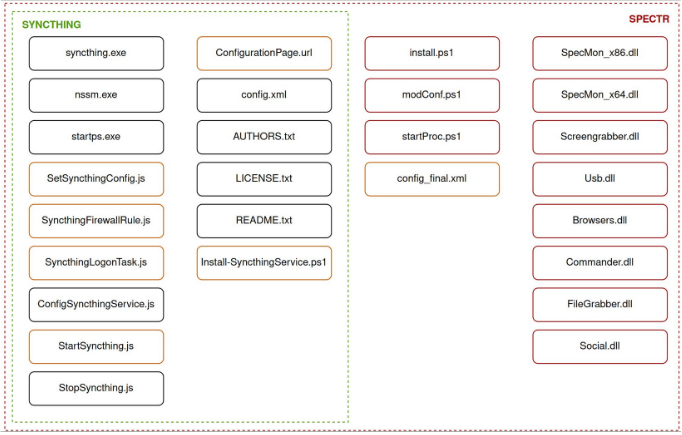
Supply: CERT-UA
CERT-UA believes Vermin determined to make use of a respectable software for information exfiltration to cut back the probability of safety techniques flagging the community site visitors as suspicious.
The cybersecurity company notes that any interplay with SyncThing’s infrastructure (e.g., *.syncthing.internet) ought to be sufficient to think about a system compromised and launch an investigation to detect and uproot the an infection.
