Beware Macro! Ukrainian customers and cyberinfrastructure are being hit by a brand new malware marketing campaign during which hackers are utilizing a multi-stage malware technique to ship the Cobalt Strike.
A latest cyberattack focusing on Microsoft Home windows-based endpoints in Ukrainian has been found by Fortinet’s FortiGuard Labs the place attackers leverage a malicious Excel file to deploy Cobalt Strike, a infamous instrument used for post-exploitation actions.
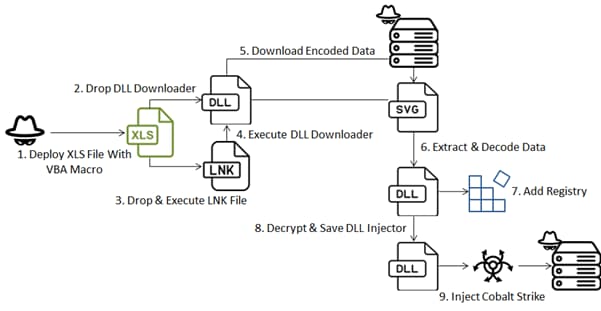
On this assault, an apparently innocent Excel file is embedded with a VBA (Visible Fundamental for Purposes) macro, a scripting language utilized in Microsoft Workplace purposes. The attacker makes use of a multi-stage malware technique to ship the “Cobalt Strike” payload and set up communication with a command and management server.
The malicious Excel doc incorporates Ukrainian components to lure customers into enabling its macros. The macro deploys a HEX-encoded DLL downloader, which executes the DLL (Dynamic Hyperlink Library) file utilizing a shell command.
The DLL file, additionally disguised as a innocent part, is the important thing to deploying Cobalt Strike. The downloader examines course of names for particular strings associated to evaluation instruments and antivirus software program, terminates this system if it detects an identical course of, and executes the decoded file utilizing “rundll32.exe”.
As per FortiGuard Labs’s report, The DLL Injector, “ResetEngine.dll,” is answerable for decrypting and injecting the ultimate payload. It makes use of “NtDelayExecution” to evade detection of malicious actions inside sandboxes after which, it decrypts the ultimate payload utilizing an AES algorithm. The code then injects the decrypted information into itself and makes use of varied APIs to execute the ultimate Cobalt Strike.
In your info, Cobalt Strike is a robust instrument that permits attackers to realize a foothold inside a compromised system, steal delicate information, deploy further malware, and set up community persistence.
Fortinet researchers found a geolocation test inside the VBA code, making certain the payload is just downloaded on methods positioned in Ukraine. This focused strategy signifies a well-orchestrated operation with a particular aim in thoughts.
This isn’t the primary time a malicious Excel file was used to focus on Ukraine in recent times as a result of ongoing geopolitical scenario. In 2022, FortiGuard Labs reported a marketing campaign utilizing a malicious Excel doc to ship a Cobalt Strike loader, whereas Ukraine’s Laptop Emergency Response Workforce confirmed UAC-0057’s involvement in an assault utilizing a malicious XLS file to deploy PicassoLoader and Cobalt Strike Beacon.
This latest assault additional highlights the evolving ways of cybercriminals and the significance of sturdy cybersecurity measures. Customers needs to be cautious of enabling macros in Excel information, particularly from unknown sources and use dependable endpoint safety software program that may detect and forestall malicious macros.
RELATED TOPICS
- RomCom RAT Targets Professional-Ukraine Friends at NATO Summit
- UAC-0099 Used Outdated WinRAR Flaw in New Assault on Ukraine
- Google, Microsoft and Oracle generated most vulnerabilities
- AcidRain Linux Malware Variant “AcidPour” Focusing on Ukraine
- Microsoft Workplace Most Exploited Software program in Malware Assaults