Key Factors
- Refined Provide chain assault: The Twister Money open supply challenge was compromised with malicious JavaScript code inserted by a developer.
- Impression: Customers who performed transactions utilizing the focused Twister Money challenge by IPFS gateways had been unknowingly impacted for a few months.
- Discovery: The compromise, found by Safety researcher Gas404, marks the second main safety situation for Twister Money inside a yr, emphasizing the significance of group vigilance in decentralized finance.
- Ongoing dangers in decentralized finance: This incident highlights the persistent challenges in making certain security and belief in decentralized platforms.
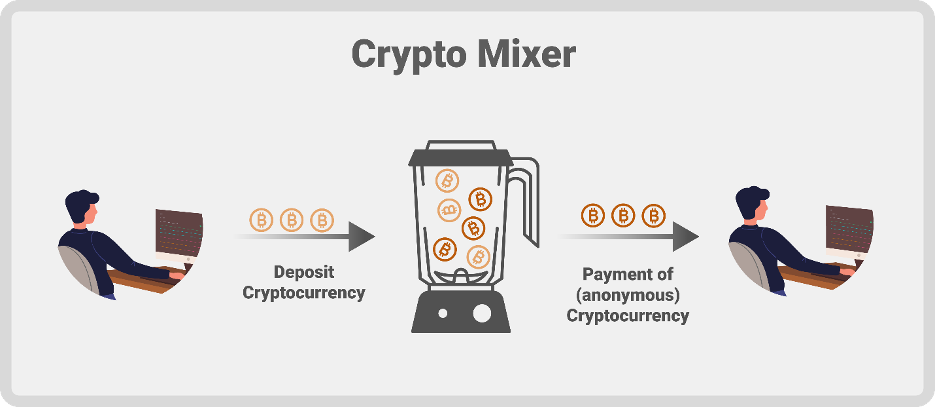
What’s Twister Money?
Twister Money is a decentralized privateness answer constructed on the Ethereum blockchain, providing customers non-custodial and nameless transactions. Functioning as a cryptocurrency mixer, it offers a mechanism to obfuscate the origins and locations of digital asset transfers, enhancing person privateness and safety. Whereas Twister Money has confronted scrutiny for its potential misuse in illicit actions, similar to cash laundering notably by entities like North Korean hackers, it stays an revolutionary device within the realm of decentralized finance.
In 2022, The unique Twister Money service encountered challenges attributable to U.S. authorities sanctions, impacting its utilization amongst sure person demographics. Regardless of this setback, the challenge’s open-source codebase has fostered the emergence of latest impartial mixing providers.
The Compromise of the Open Supply Twister Money
Twister Money not too long ago fell sufferer to a classy assault. This assault was executed by a misleading contribution by a developer, who secretly embedded malicious JavaScript code inside the challenge’s person interface. This code was designed to covertly seize and ship customers’ non-public deposit notes to an unauthorized exterior server. Deposit notes in Twister Money act like non-public keys, essential for accessing and managing funds inside the service.
This exploit particularly focused customers accessing Twister Money by IPFS gateways, like ipfs.io and cf-ipfs.com. These gateways are used to enter the decentralized internet the place Twister Money operates. The malicious code was cleverly hid inside a governance proposal by the developer, making it very difficult for a median person to detect.
The code labored by encoding these non-public deposit notes and sending them to the exploiter’s server below the guise of routine perform calls. This meant that every time a person engaged with sure capabilities of Twister Money, their non-public data was leaked with out their data.
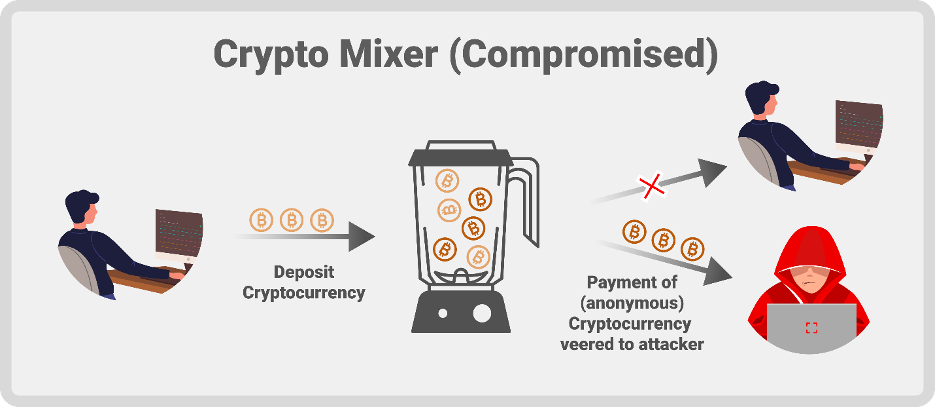
The invention of this malicious code was credited to a safety researcher often known as Gas404, and in line with their findings, all Twister Money servers deployed on the IPFS community since January 1 of this yr had been believed to be impacted.
Within the aftermath of the sanctions imposed on Twister Money, the unique web site of the service was seized. Nevertheless, the open-source codebase of Twister Money continued to exist independently, resulting in the emergence of latest, shadowy mixing providers utilizing the identical basis. This incident of backdoor code implantation marks the second main safety breach that Twister Money has endured over the previous yr, with a earlier occasion in Could of the earlier yr the place a hacker briefly seized management of the challenge’s governance.
When it comes to the affect, the precise extent of the funds compromised on this newest breach nonetheless stays unsure.
Conclusion
The Twister Money open-source challenge compromise highlights critical considerations in regards to the security of decentralized finance platforms and the trustworthiness of builders. It serves as a stark reminder that we can’t merely assume open-source tasks are immune from malicious actions. The notion that “someone else is checking” can typically result in a false sense of safety. Importantly, this incident illustrates how attackers wish to leverage provide chain assaults to compromise delicate functions and networks. It underscores the significance of thorough safety audits, vetting of code and contributions, even from seemingly reliable sources, and the necessity to shield towards provide chain vulnerabilities. For customers, it is a reminder to be vigilant in regards to the platforms they use and to know the related dangers. Clearly, preserving safety and belief in decentralized platforms stays a difficult however very important job.