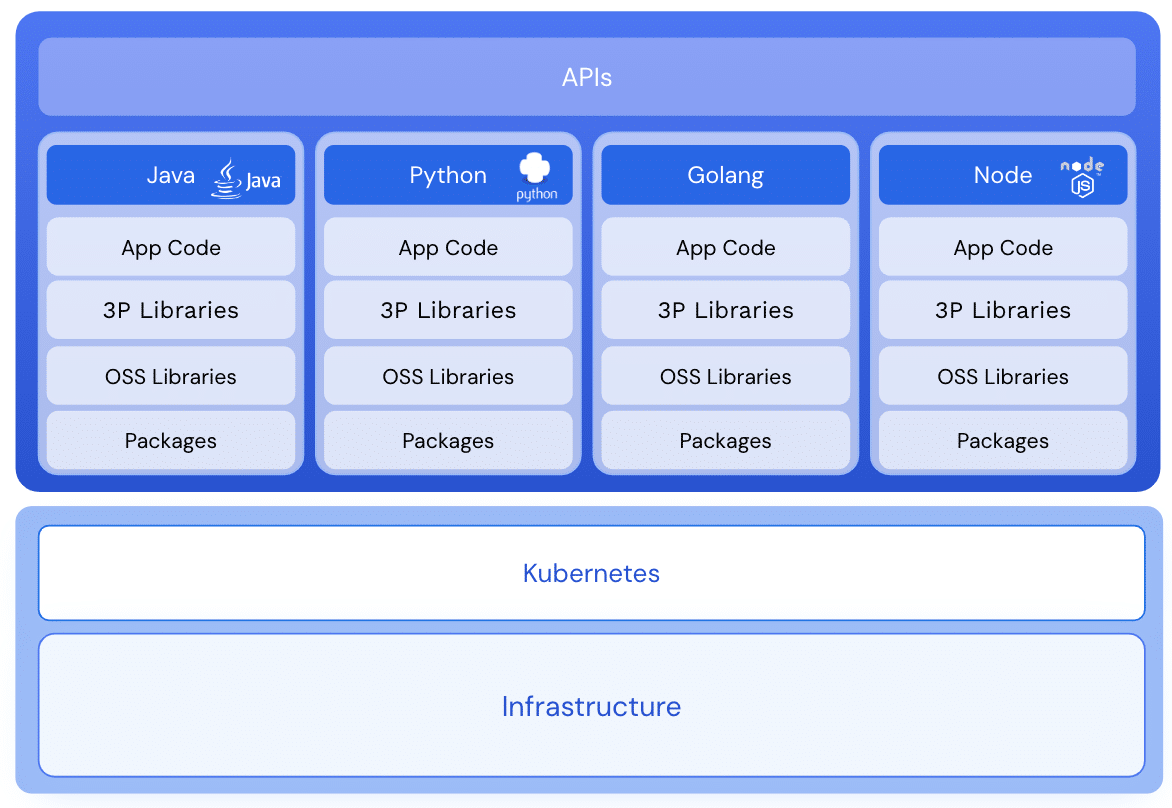
Relating to understanding utility threat and detecting refined threats concentrating on functions, context is king. Traceable is purpose-built to offer essentially the most full safety context on APIs by capturing, correlating, and analyzing each API transaction. By partnering with Wiz, we additional lengthen our knowledge benefit with cloud safety context, powering higher-fidelity menace detection and threat based mostly prioritization for cloud native functions.
We introduced the primary section of our integration final 12 months, bringing Wiz knowledge into Traceable, and are excited to announce a brand new section that pushes Traceable’s API safety context into the Wiz platform.
Part 1: Wiz Cloud Context in Traceable
Traceable AI has been one of many early expertise companions with Wiz for the WIN program, offering prospects with the mixed capabilities of the Wiz Cloud Native Utility Safety Platform (CNAPP) and Traceable’s API Safety Platform. The primary section of the combination helped our joint prospects obtain the next targets:
- Full Code to Cloud Risk Correlation: Correlate API threats recognized by Traceable with cloud context round Kubernetes and VM deployments from Wiz
- Forestall Information Loss at API layer: Information loss mapping with cloud context to guard delicate knowledge throughout API Request/Response and cloud storage layers
- Scale simply and securely: Computerized mapping of APIs to cloud deployments by Traceable to find out the place compromised cloud belongings reside.
Part 2: Bi-directional Integration Brings Traceable API Context into Wiz
The following section of the combination takes full menace correlation to the subsequent stage with the flexibility to push Traceable menace detections into Wiz Cloud occasions and the highly effective Wiz Safety graph. This fully modifications the best way APIs might be protected with cloud context and menace correlation is feasible in a single console inside the Wiz platform. Since most fashionable APIs are deployed within the public cloud right now, the important thing container and VM stage correlation is achieved with the capabilities of the eBPF expertise that Traceable invested in early.
Key options and advantages for our joint prospects with this expanded integration embody:
Correlate real-time API threats from Traceable with Wiz Points for deeper context and streamlined investigation
Wiz identifies and prioritizes Points in cloud environments based mostly on a number of threat and menace components. Traceable leverages Wiz Points to offer Safety groups with cloud infrastructure context when remediating an energetic menace detected on their APIs. Pushing API runtime menace detections to Wiz helps enrich Wiz’s menace detection capabilities and contribute as proof to Wiz Points. These are particularly helpful for privilege escalation, injection assaults and arbitrary code execution based mostly exploits like Log4 Shell and Spring4 Shell.
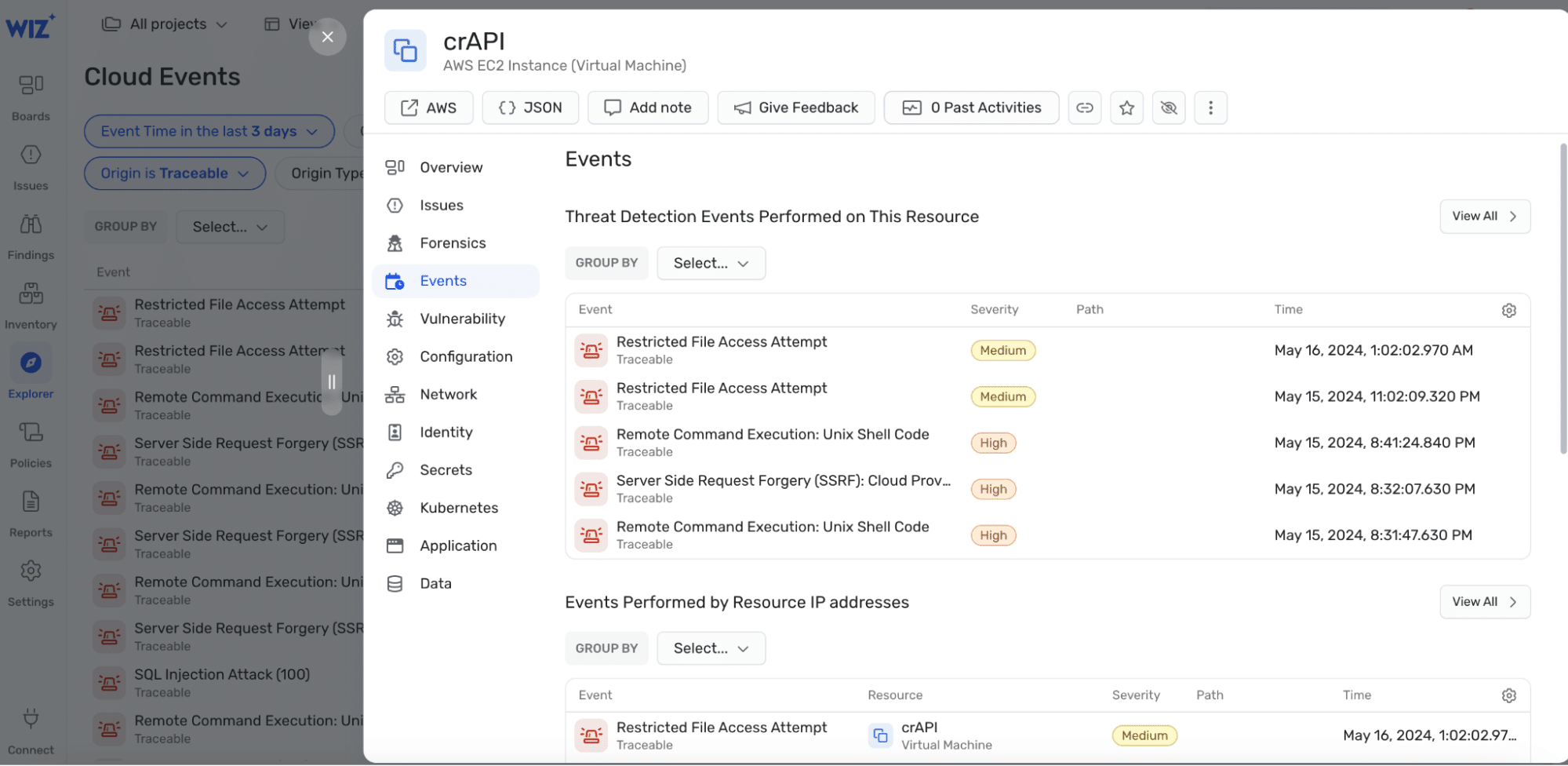
Prioritize API vulnerabilities based mostly on probability of exploitation
Wiz scans cloud environments and creates an entire stock of cloud belongings, interdependencies, and dangers related to these belongings. Traceable helps deployment modes like eBPF which has underlying cloud belongings particulars that allow it to question Wiz’s API to tug stock, API misconfigurations, and points. Correlating these insights with threats seen on the APIs offers infosec groups with particulars on assault paths due for particular person or mixed dangers.
Visualize assaults on Wiz Safety Graph for Incident Response
When a safety incident happens, it’s crucial that Incident Response groups have the ability to shortly and precisely assess the potential influence of a compromised useful resource similar to a VM or container and pinpoint the basis explanation for how the safety breach occurred. Wiz’s key improvements on this space are complemented with Traceable’s inherent capabilities round actual time menace detection for unparalleled poisonous mixture evaluation.
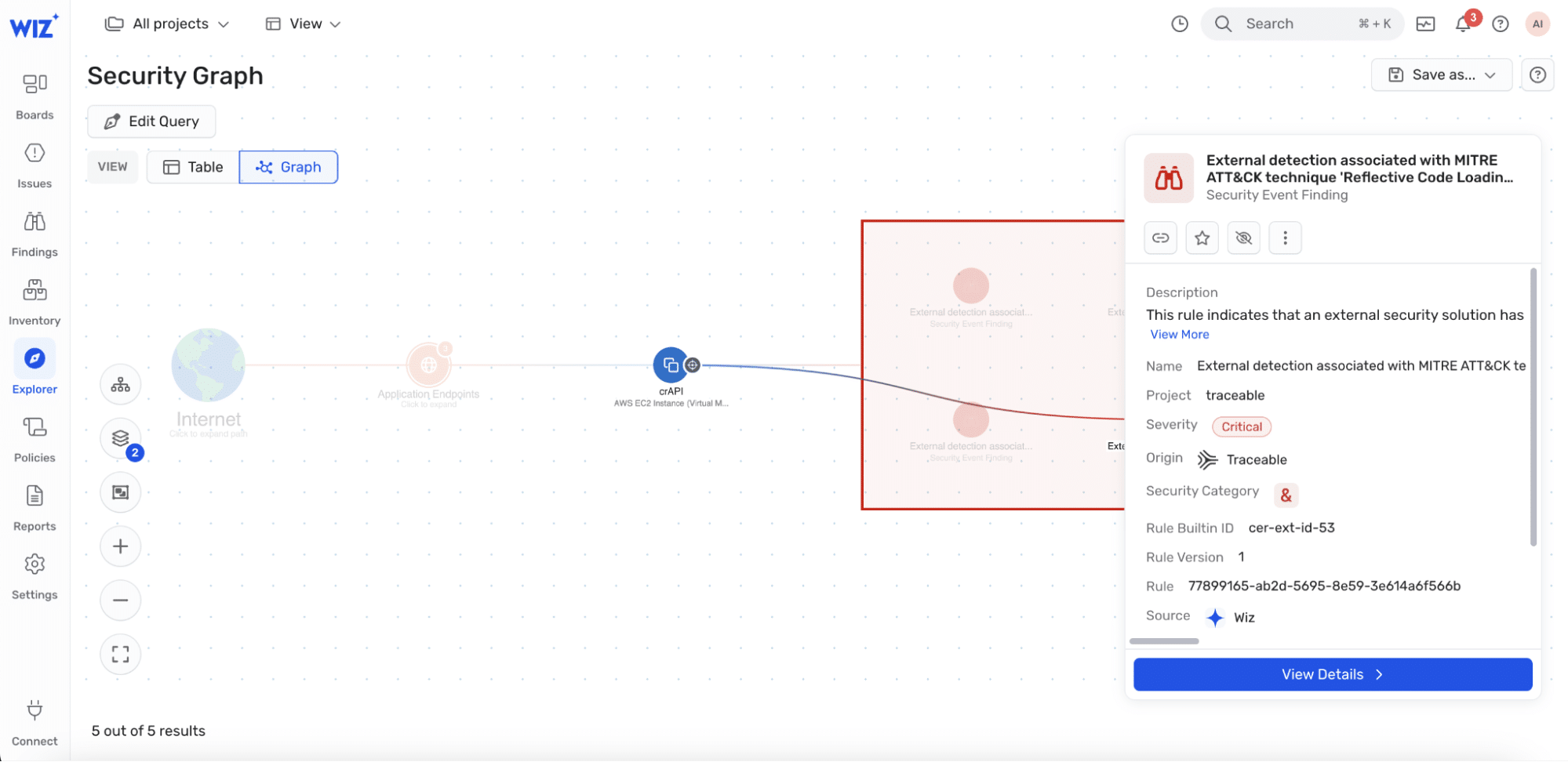
Forensics and Root Trigger Evaluation
Pinpointing the basis explanation for a safety incident in complicated cloud deployments which span VMs, containers, serverless, and so forth. might be like discovering a needle in a haystack. For Kubernetes Namespaces, Wiz has open-sourced the blast radius calculation technique and launched NamespaceHound to detect violations, Traceable’s platform has full protection for menace detections starting from AuthN/AuthZ based mostly assaults to privilege escalation to path manipulation based mostly assaults. That correlated with behavioral baselines permits for full menace looking and forensics which enhances Wiz’s capabilities properly.
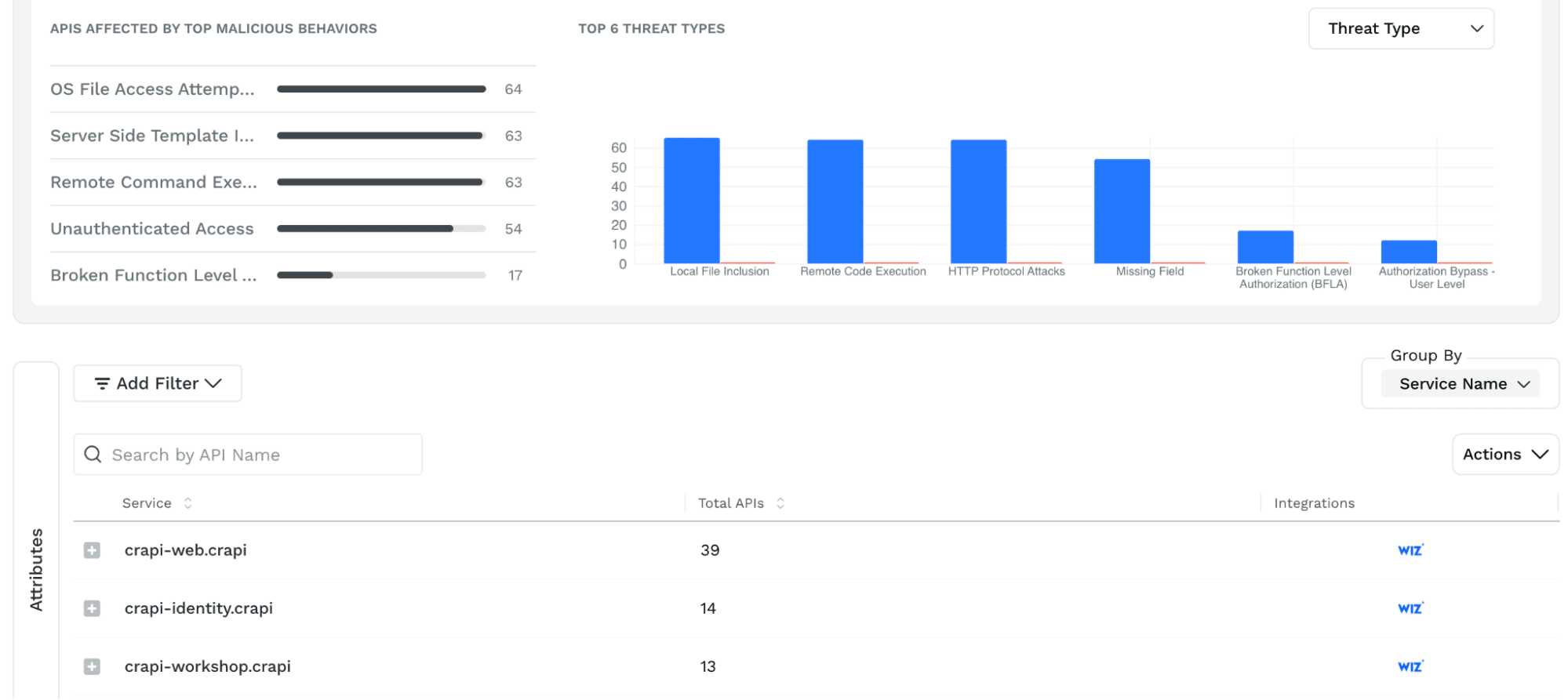
In conclusion, Traceable empowers safety groups to proactively assess and repair safety points in APIs to determine menace exercise. With in depth safety context, menace intel, and broad and deep knowledge assortment and evaluation Traceable delivers an information benefit in defending APIs throughout cloud environments. Wiz offers prospects the flexibility to robotically gather essential proof when a cloud useful resource could have been compromised. Collectively Traceable and Wiz present highly effective safety context, prioritization, and remediation capabilities to guard your functions from code to cloud.
To unlock the facility of correlated cloud and API safety context with Traceable and Wiz, schedule a demo right now.
About Traceable
Traceable is the business’s main API Safety firm serving to organizations obtain API safety in a cloud-first, API-driven world. Traceable is the one contextually-informed answer that powers full API safety – API discovery and posture administration, API safety testing, assault detection and menace looking, and assault safety anyplace your APIs stay. Traceable allows organizations to reduce threat and maximize the worth that APIs convey to their prospects. To study extra about how API safety can assist your corporation, go to https://www.traceable.ai/.