Cybersecurity researchers have found a number of campaigns concentrating on Docker Hub by planting thousands and thousands of malicious “imageless” containers over the previous 5 years, as soon as once more underscoring how open-source registries may pave the best way for provide chain assaults.
“Over four million of the repositories in Docker Hub are imageless and have no content except for the repository documentation,” JFrog safety researcher Andrey Polkovnichenko stated in a report shared with The Hacker Information.
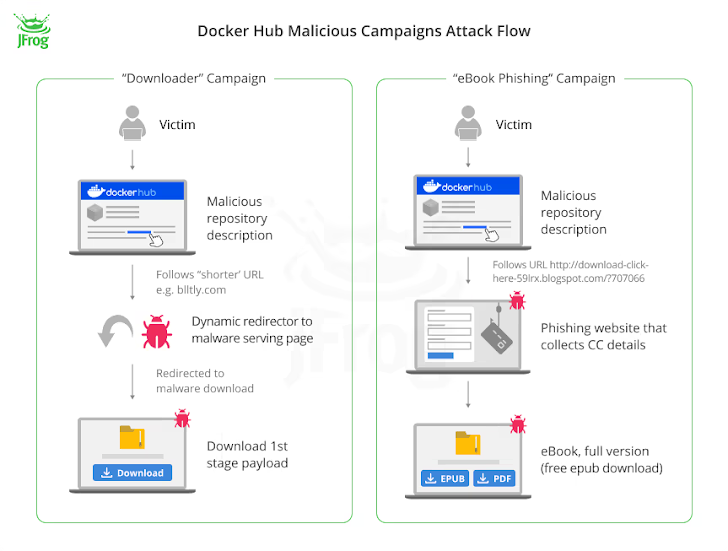
What’s extra, the documentation has no connection in any respect to the container. As a substitute, it is a net web page that is designed to lure customers into visiting phishing or malware-hosting web sites.
Of the 4.79 million imageless Docker Hub repositories uncovered, 3.2 million of them are stated to have been used as touchdown pages to redirect unsuspecting customers to fraudulent websites as a part of three broad campaigns –
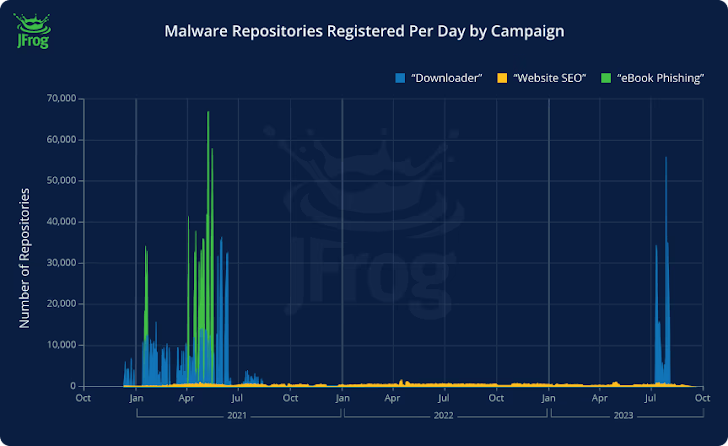
- Downloader (repositories created within the first half of 2021 and September 2023), which advertises hyperlinks to purported pirated content material or cheats for video video games however both straight hyperlinks to malicious sources or a respectable one which, in flip, incorporates JavaScript code that redirects to the malicious payload after 500 milliseconds.
- E-book phishing (repositories created in mid-2021), which redirects customers trying to find e-books to a web site (“rd.lesac.ru”) that, in flip, urges them to enter their monetary info to obtain the e-book.
- Web site (1000’s of repositories created each day from April 2021 to October 2023), which incorporates a hyperlink to a web-based diary-hosting service referred to as Penzu in some instances.
The payload delivered as a part of the downloader marketing campaign is designed to contact a command-and-control (C2) server and transmit system metadata, following which the server responds with a hyperlink to cracked software program.
Alternatively, the precise aim of the web site cluster is at the moment unclear, with the marketing campaign additionally propagated on websites which have a lax content material moderation coverage.
“The most concerning aspect of these three campaigns is that there is not a lot that users can do to protect themselves at the outset, other than exercising caution,” Shachar Menashe, senior director of safety analysis at JFrog, stated in a press release shared with The Hacker Information.
“We’re essentially looking at a malware playground that in some cases has been three years in the making. These threat actors are highly motivated and are hiding behind the credibility of the Docker Hub name to lure victims.”
With risk actors taking painstaking efforts to poison well-known utilities, as evidenced within the case of the XZ Utils compromise, it is crucial that builders train warning with regards to downloading packages from open-source ecosystems/
“As Murphy’s Law suggests, if something can be exploited by malware developers, it inevitably will be, so we expect that these campaigns can be found in more repositories than just Docker Hub,” Menashe stated.