What number of occasions have you ever tried to configure a static IP handle for a machine in your community, solely to understand you had no thought what addresses have been already taken? Should you occur to work with a desktop machine, you would all the time set up a community protocol analyzer to seek out out what addresses have been in use. However what in case you’re on a GUI-less server? You definitely gained’t depend on a graphical-based device for scanning IP addresses. Luckily, some very simple-to-use command line instruments can deal with this job.
I’m going to point out you how you can scan your Native Space Community (LAN) for IP addresses in use with two completely different instruments (considered one of which can be put in in your server by default). I’ll reveal on Ubuntu Server.
SEE: Prime Instructions Linux Admins Have to Know (TechRepublic Premium)
The arp command
The primary device we’ll use for the duty is the built-in arp command. Most IT admins are conversant in arp, as it’s used on nearly each platform. Should you’ve by no means used arp (which stands for Deal with Decision Protocol), the command is used to govern (or show) the kernel’s IPv4 community neighbor cache. Should you problem arp with no mode specifier or choices, it should print out the present content material of the ARP desk. That’s not what we’re going to do. As a substitute, we’ll problem the command like so:
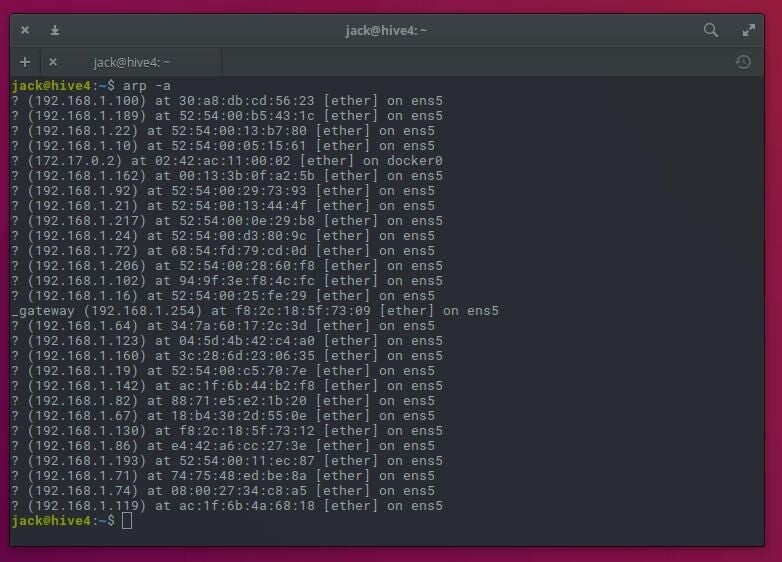
arp -a
The -a choice makes use of an alternate BSD-style output and prints all identified IP addresses discovered in your LAN. The output of the command will show IP addresses in addition to the related ethernet machine.
You now have an inventory of every IP handle in use in your LAN. The one caveat, is that (except you recognize the MAC handle of each machine in your community), you gained’t have a clue as to which machine the IP addresses are assigned. Even with out understanding what machine is related to what handle, you no less than know what addresses are getting used.
NB. The arp command solely works for IPv4. If in case you have IPv6, you’ll want to make use of the command ndp (which stands for Neighbor Discovery Protocol):
ndp -a
It’s straightforward to inform in case you’re utilizing IPv4 or IPv6 addresses. The previous use intervals, the latter use colons. IBM presents an explainer on the topic in order for you extra particulars.
SEE: The way to Add an SSH Fingerprint to Your known_hosts File in Linux (TechRepublic)
Nmap
Subsequent, we use a command that provides extra choices. Stated command is nmap (which stands for Community Mapper). You gained’t discover nmap put in in your Linux machine by default, so we should add it to the system. Open a terminal window (or log into your GUI-less server) and problem the command:
sudo apt-get set up nmap -y
As soon as the set up is accomplished, you’re able to scan your LAN with nmap. To seek out out what addresses are in use, problem the command:
nmap -sP 192.168.1.0/24
Observe: You’ll need to change the IP handle scheme to match yours.
The output of the command, will present you every handle discovered in your LAN.
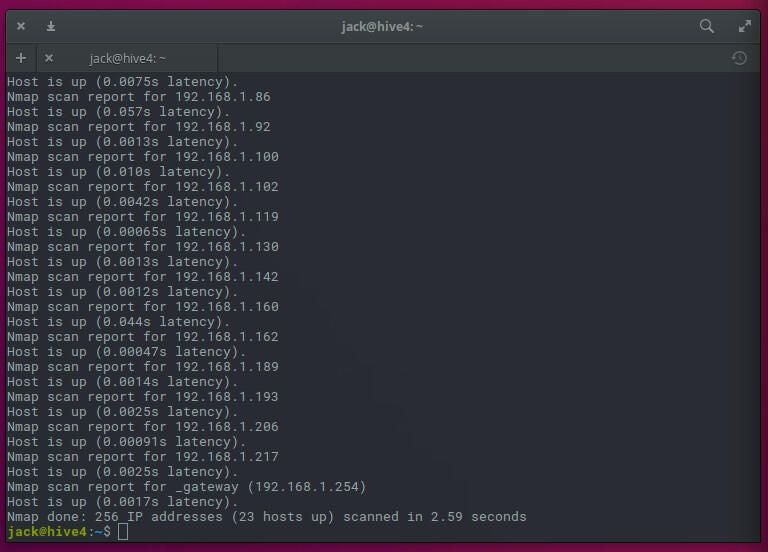
Let’s make nmap extra helpful. As a result of it presents a bit extra flexibility, we are able to additionally uncover what working system is related to an IP handle. To do that, we’ll use the choices -sT (TCP join scan) and -O (working system discovery). The command for that is:
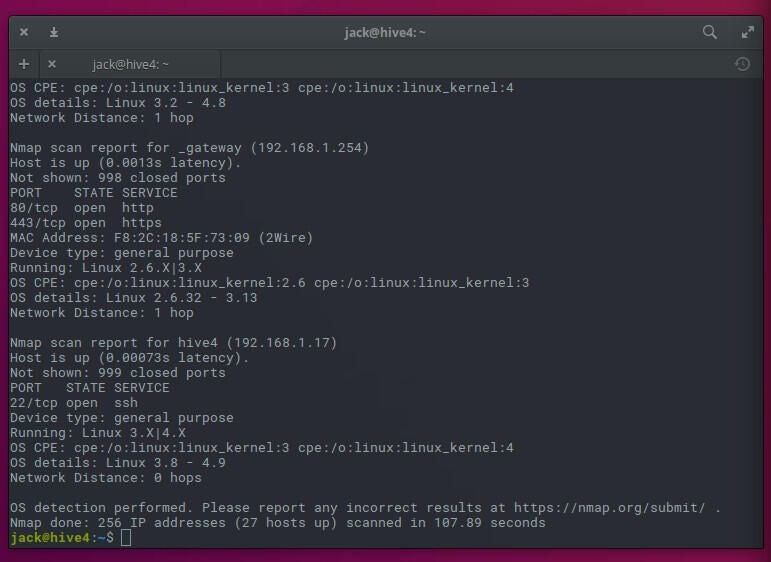
sudo nmap -sT -O 192.168.1.0/24
Relying on the dimensions of your community, this command can take a while. And in case your community is giant, contemplate sending the output of the command to a file like this:
sudo nmap -sT -O 192.168.1.0/24 > nmap_output
You may then view the file with a textual content editor to seek out out what working system is hooked up to an IP handle.
With the assistance of those two easy instructions, you may find IP addresses in your community which might be in use. Now, once you’re assigning a static IP handle, you gained’t by accident assign one already in use. Everyone knows what sort of complications that may trigger.