
As we speak over at Resonance Safety I’m going to have a look at one of many extra uncommon methods through which your strategy to laptop safety can result in a rise in public consciousness of your organization.
There are a lot of motivations for beginning an organization: turning into rich, doing one thing fascinating and helpful, and leaving some type of legacy or mark on historical past are three of the principle ones that spring to thoughts.
About that legacy: think about having the title of your company hooked up to a file representing one of the vital vital hacks of the twenty first century!
That’s fairly notable, however in all probability not what the founders of 1 explicit firm have been searching for with their startup.
We gained’t rock you
In the midst of the 2000s, RockYou, Inc. was doing effectively as a widget-maker for social media firms like MySpace and Fb. Nonetheless, again in 2009, it suffered an information breach through which a hacker found an SQL database server with an unpatched ten-year-old bug, the database containing over 32 million usernames and passwords for consumer accounts.
That’s proper — 32 million usernames, and their related passwords. For comparability, that’s about 10% of the lively month-to-month customers that Fb had on the time.
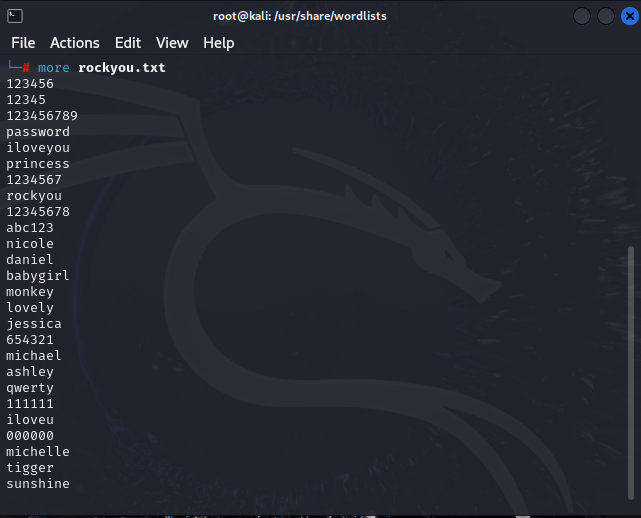
The passwords have been saved in plain textual content.
Mud in your face, massive shame
Not solely did RockYou initially fail to inform their customers, but it surely subsequently launched a falsified official assertion claiming that the breach was much less extreme than it was.
To be clear: it was a really, very critical breach.
A decade and a half in the past, folks have been far worse at password safety than they’re now. Password managers have been nearly exceptional, for some unexplained weird purpose some websites blocked the usage of password managers for unspecified “security reasons”, and two-factor authentication was just about solely reasonably priced and obtainable to enterprise customers.
As a result of folks have been informed to not write down their passwords, this meant that many of the leaked credentials have been getting used on different web sites. In spite of everything, who of their proper thoughts goes to memorize twenty or thirty totally different random passwords? Because of this, websites corresponding to banks, on-line shops, well being databases, social media, supposedly personal on-line journals, and on-line video games held accounts utilizing the identical passwords.
The legacy
For years the complete listing of RockYou passwords has been obtainable to obtain by anybody. It’s sometimes present in a file referred to as rockyou.txt , and there are many GitHub repositories on the market the place yow will discover it.
In Kali Linux, a Linux distribution designed and produced particularly for penetration testing, the RockYou textual content file is included throughout the set up by default.
Conclusion
Simply think about — with somewhat little bit of safety carelessness, you can also take your modestly profitable firm and within the strategy of destroying it, permit its title to stay on ceaselessly.
Have we realized something since 2009? Not at all times.
For instance: in 2017 it was revealed that an outdated social media website referred to as LiveJournal, courting again to the 90s (however nonetheless operating to today), suffered a breach through which 26 million distinctive usernames, electronic mail addresses, and plaintext passwords have been extracted. It took them till 2019 to confess to the breach.
That’s proper — passwords have been nonetheless being saved in plaintext in 2017, and I’d wager good cash on there being extra websites out are doing the identical, though we’re a decade and a half on from the unique RockYou breach.
I predict that the leakage of passwords will solely finish as soon as we cease utilizing passwords, and begin utilizing improved techniques corresponding to safety keys and self-managed id for our authentication techniques.
Within the meantime, it’s a must to assume that any password you present to a web site will ultimately be leaked, subsequently:
- use a password supervisor to generate lengthy, random, distinctive passwords in your accounts,
- shield entry to the password supervisor with two-factor authentication, and
- make certain the password you utilize in your password supervisor has by no means been used anyplace else.
Submit-script
Don’t run off and search for a web site that permits you to enter your password and see if it was ever revealed in a breach! I can assure it is going to be a phishing website. As a substitute, I like to recommend HaveIBeenPwned, the place you may kind in your electronic mail deal with, and retrieve a listing of the businesses and web sites which have managed to leak your credentials to the darkish net by way of unhealthy safety practices. Another choice is the Resonance Knowledge Leak Detector, which screens in case your credentials have been leaked 24/7 and robotically notifies you.
About Resonance Safety
Resonance Safety is a curated platform for end-to-end cybersecurity services. It capabilities as a concierge in your group’s end-to-end cyber-security wants, aggregating useful safety choices into one platform to unfold consciousness on what it takes to safe your know-how stack end-to-end.
I’m Keir Finlow-Bates, typically often known as Blockchain Gandalf, and am primarily a blockchain researcher and inventor. I began on this journey in late 2010 by inspecting the unique Bitcoin code, and have been obsessive about blockchain ever since.
I’m additionally the creator of two books on the subject: Transfer Over Brokers Right here Comes The Blockchain, explaining blockchain, and Evil Tokenomics, illustrating by way of sensible examples how web3 scams work. Yow will discover extra at my web site: Thinklair.com
