Telegram fastened a zero-day vulnerability in its Home windows desktop software that could possibly be used to bypass safety warnings and robotically launch Python scripts.
Over the previous few days, rumors have been circulating on X and hacking boards about an alleged distant code execution vulnerability in Telegram for Home windows.
Whereas a few of these posts claimed it was a zero-click flaw, the movies demonstrating the alleged safety warning bypass and RCE vulnerability clearly present somebody clicking on shared media to launch the Home windows calculator.
Telegram shortly disputed these claims, stating that they “can’t confirm that such a vulnerability exists” and that the video is probably going a hoax.
Nonetheless, the following day, a proof of idea exploit was shared on the XSS hacking discussion board explaining {that a} typo within the supply code for Telegram for Home windows could possibly be exploited to ship Python .pyzw recordsdata that bypass safety warnings when clicked.
This brought on the file to robotically be executed by Python with out a warning from Telegram prefer it does for different executables, and was presupposed to do for this file if it wasn’t for a typo.
To make issues worse, the proof of idea exploit disguised the Python file as a shared video, together with a thumbnail, that could possibly be used to trick customers into clicking on the pretend video to look at it.
In an announcement to BleepingComputer, Telegram rightfully disputes that the bug was a zero-click flaw however confirmed they fastened the “issue” in Telegram for Home windows to forestall Python scripts from robotically launching when clicked. This was a server-side repair, which we clarify within the subsequent part
“Rumors about the existence of zero-click vulnerabilities in Telegram Desktop are inaccurate. Some “consultants” recommended to “disable computerized downloads” on Telegram — there have been no points which may have been triggered by computerized downloads.
Nonetheless, on Telegram Desktop, there was a difficulty that required the person to CLICK on a malicious file whereas having the Python interpreter put in on their laptop. Opposite to earlier studies, this was not a zero-click vulnerability and it may have an effect on solely a tiny fraction of our person base: lower than 0.01% of our customers have Python put in and use the related model of Telegram for Desktop.
A server-side repair has been utilized to make sure that even this subject not reproduces, so all variations of Telegram Desktop (together with all older ones) not have this subject.”
❖ Telegram
BleepingComputer requested Telegram how they know what software program is put in on person’s Home windows units, as such a information isn’t talked about of their Privateness Coverage.
The Telegram vulnerability
The Telegram Desktop consumer retains monitor of a listing of file extensions related to dangerous recordsdata, comparable to executable recordsdata.
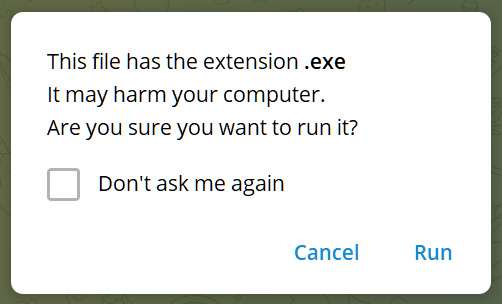
When somebody sends certainly one of these file varieties in Telegram, and a person clicks on the file, as a substitute of robotically launching within the related program in Home windows, Telegram first shows the next safety warning.
“This file has the extension .exe. It may harm your computer. Are you sure you want to run it?,” reads the Telegram warning.
Supply: BleepingComputer
Nonetheless, unknown file varieties shared in Telegram will robotically be launched in Home windows, letting the working system determine what program to make use of.
When Python for Home windows is put in, it would affiliate the .pyzw file extension with the Python executable, inflicting Python to execute the scripts robotically when the file is double-clicked.
The .pyzw extension is for Python zipapps, that are self-contained Python applications contained inside ZIP archives.
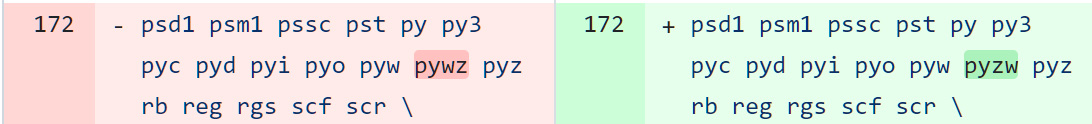
The Telegram builders have been conscious that some of these executables ought to be thought of dangerous and added it to the listing of executable file extensions.
Sadly, after they added the extension, they made a typo, coming into the extension as ‘pywz‘ somewhat than the right spelling of ‘pyzw‘.
Supply: BleepingComputer.com
Due to this fact, when these recordsdata have been despatched over Telegram and clicked on, they have been robotically launched by Python if it was put in in Home windows.
This successfully permits attackers to bypass safety warnings and remotely execute code on a goal’s Home windows system if they will trick them into opening the file.
To masquerade the file, researchers devised utilizing a Telegram bot to ship the file with a mime kind of ‘video/mp4,’ inflicting Telegram to show the file as a shared video.
If a person clicks on the video to look at it, the script will robotically be launched by way of Python for Home windows.
BleepingComputer examined this exploit with cybersecurity researcher AabyssZG, who additionally shared demonstrations on X.
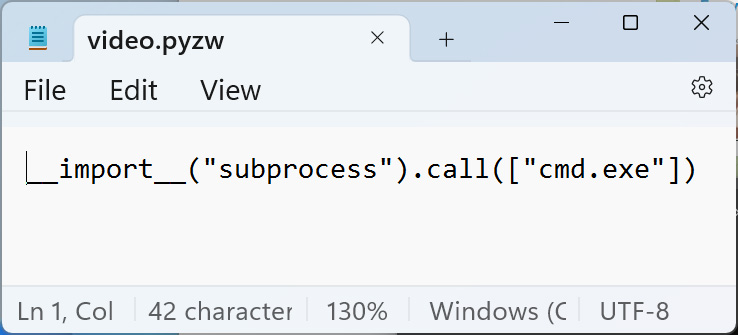
Utilizing an older model of Telegram, BleepingComputer acquired ‘video.pywz’ file from the researcher disguised as a mp4 video. This file merely incorporates Python code to open a command immediate, as proven under.
Supply: BleepingComputer
Nonetheless, as you may see under, whenever you click on on the video to look at it, Python robotically executes the script, which opens the command immediate. Be aware that we redacted the video thumbnail because it’s barely NSFW.
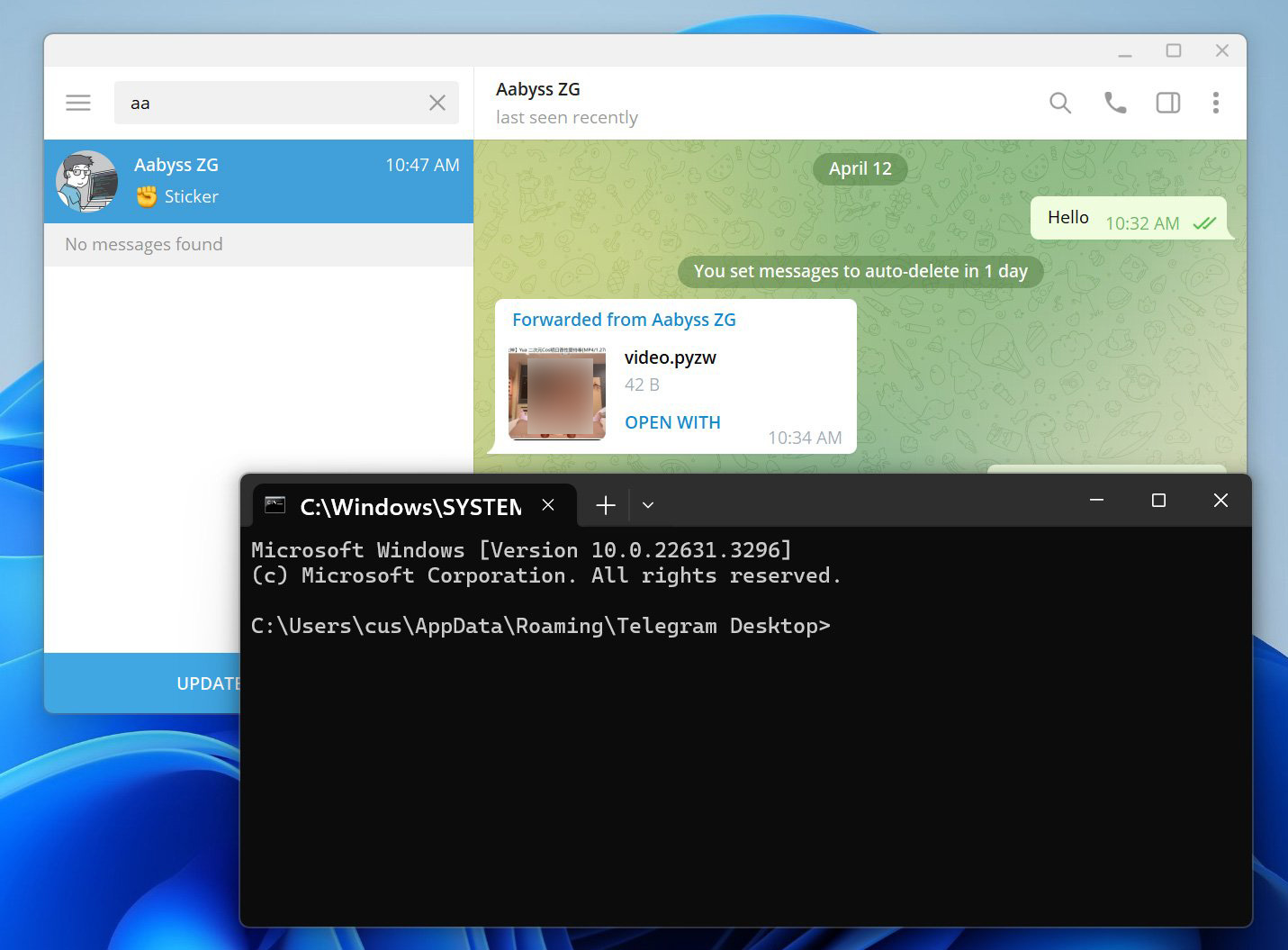
Supply: BleepingComputer
The bug was reported to Telegram on April tenth, and so they fastened it by correcting the extension spelling within the ‘data_document_resolver.cpp’ supply code file.
Nonetheless, this repair doesn’t look like dwell as of but, because the warnings don’t seem whenever you click on on the file to launch it.
As a substitute, Telegram utilized a server-side repair that appends the .untrusted extension to pyzq recordsdata, that when clicked, will trigger Home windows to ask what program you want to use to open it, somewhat than robotically launching in Python.
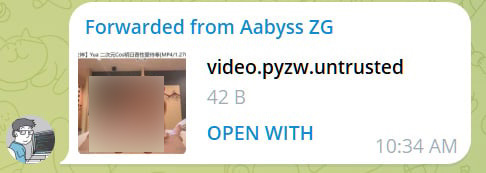
Supply: BleepingComputer
Future variations of the Telegram Desktop app ought to embody the safety warning message somewhat than appending the “.untrusted” extension, including a bit extra safety to the method.
