SUMMARY
- BT Group Ransomware Assault: British telecom big BT Group’s Conferencing division was hit by a ransomware assault by Black Basta, resulting in sure servers being taken offline.
- Stolen Knowledge: Black Basta claims to have stolen 500 GB of delicate knowledge, together with monetary, company, and private data, and threatened to leak it except a ransom is paid.
- Firm Response: BT Group acknowledged the assault was confined to particular elements of its Conferencing platform, with core providers unaffected, and is working with authorities to research.
- Black Basta’s Strategies: The group makes use of superior ways like electronic mail bombing and social engineering via platforms like Microsoft Groups to achieve preliminary entry.
- International Ransomware Menace: Black Basta has focused over 500 organizations, affecting vital infrastructure sectors, emphasizing the necessity for strong cybersecurity measures.
Days after the ransomware assaults on the NHS Hospitals in the UK, British telecommunications big BT Group has fallen sufferer to a ransomware assault launched by the infamous Black Basta gang. The assault particularly focused the corporate’s Conferencing enterprise division, forcing the corporate to take sure servers offline as a precautionary measure.
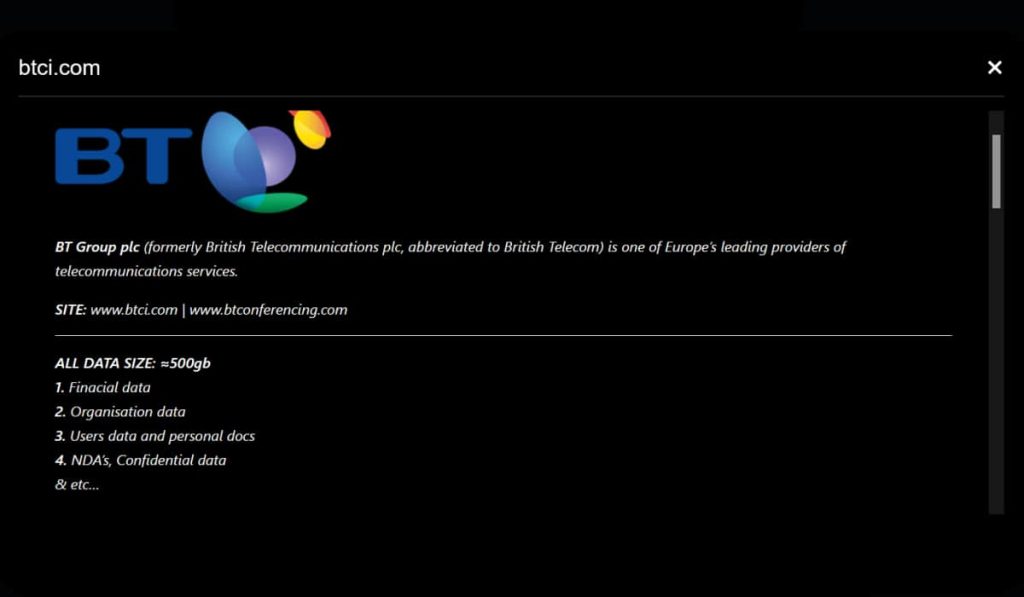
Whereas BT Group has downplayed the severity of the assault, claiming restricted affect on its providers and buyer knowledge, Black Basta paints a much more alarming image. The ransomware gang asserts that they efficiently stole a staggering 500 gigabytes of delicate data. As an proof, the group has launched screenshots of stolen paperwork and folder listings.
The menace actors added BT’s btci.com and btconferencing.com domains to their knowledge leak web site, threatening to publicly launch the stolen data, which incorporates monetary, company, and even private knowledge akin to passport copies, except a ransom is paid. Nevertheless, the precise quantity of the ransom has not been disclosed.
BT Group has confirmed to Hackread.com that it’s actively investigating the incident and cooperating with related authorities. The corporate has emphasised that the assault was confined to particular components of the Conferencing platform and that core providers stay operational.
“We identified an attempt to compromise our BT Conferencing platform. This incident was restricted to specific elements of the platform, which were rapidly taken offline and isolated.”
“We’re continuing to actively investigate all aspects of this incident, and we’re working with the relevant regulatory and law enforcement bodies as part of our response,” BT Group’s spokesperson acknowledged.
Black Basta has focused over 500 organizations globally previously two years, concentrating on 12 out of 16 vital infrastructure sectors, with victims together with Ascension Healthcare, Hyundai Europe, Capita, Yellow Pages Canada, and Dish.
The group, a ransomware-as-a-service (RaaS) variant rising in 2022 after the Russian invasion of Ukraine and the downfall of Conti, has had important impacts on the worldwide economic system, based on the FBI and CISA’s (PDF) advisory titled “#StopRansomware: Black Basta.”
Analysis reveals that Black Basta, has been refining its social engineering strategies. The group usually initiates assaults by bombarding victims with emails from numerous mailing lists, creating a way of urgency and confusion.
“Recent techniques include email bombing—a tactic used to send a large volume of spam emails—to aid social engineering over Microsoft Teams and trick victim end users into providing initial access via remote monitoring and management (RMM) tools,” CISA’s up to date advisory revealed.
This social engineering ploy usually leads victims to grant distant entry to their units, permitting the hackers to deploy malware and steal delicate data.
The incident reminds us that ransomware assaults stay a constant menace, even for big, well-resourced organizations. Subsequently, companies should spend money on superior cybersecurity measures to guard delicate knowledge and preserve enterprise continuity.
RELATED TOPICS
- US, UK Navy Social Community “Forces Penpals” Leaks PII Knowledge
- Qilin Ransomware Leaks 400GB of NHS, Affected person Knowledge on Telegram
- Russian Midnight Blizzard Breached UK Residence Workplace by way of Microsoft
- Main UK Safety Supplier Leaks Trove of Guard and Suspect Knowledge
- China Suspected in Cyberattack on UK’s Ministry of Defence (MoD)