For cybersecurity professionals in e mail safety and anti-phishing, the start of 2024 marked the beginning of an evolution.
In January, adoption of the e-mail customary for shielding domains from spoofing by fraudsters — Area-based Messaging Authentication, Reporting and Conformance, or DMARC — took off as corporations ready for the enforcement of mandates by e mail giants Google and Yahoo. DMARC makes use of a site document and different email-focused safety applied sciences to find out whether or not an e mail comes from a server approved to ship messages on behalf of a specific group.
But three months later, the rise in DMARC adoption is already beginning to taper off, and lots of corporations have accomplished solely essentially the most minimal configuration of their domains, corresponding to setting DMARC to flag points quite than quarantine and even reject messages.
Sadly, many organizations stay involved that DMARC is simply one other safety management that, if accomplished fallacious, might break important e mail companies, says Rahul Powar, CEO of Crimson Sift, a risk intelligence supplier.
“Many organizations are rightly concerned that if they go and they do a DMARC policy and it’s not correct, that they could block something that’s really material to the business, such as a massive marketing campaign, or that the CEO’s email won’t land in the right inbox,” he says. “There’s a concern about getting it wrong.”
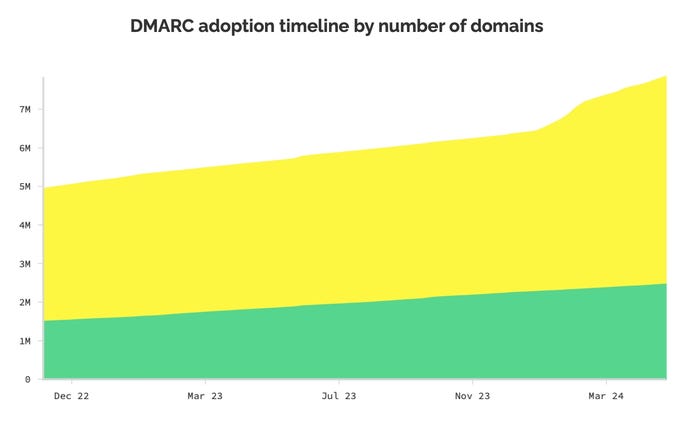
As of the tip of April, about 7.9 million domains have some kind of DMARC document (yellow), however solely 32% are BIMI prepared (inexperienced). Supply: BIMIRadar.com
Nonetheless, DMARC — and the underlying applied sciences of Sender Coverage Framework (SPF) and DomainKeys Recognized Mail (DKIM) — usually are not troublesome to arrange for small or midsize companies which have easy e mail infrastructure via a third-party service, corresponding to Google Workspace or Microsoft 365. Nonetheless, if there are older programs or some segmentation utilizing subdomains, the configuration can get advanced — quick, says Gerasim Hovhannisyan, co-founder and CEO at service supplier EasyDMARC.
“The problem comes when you have legacy systems and multiple sending sources and infrastructure,” he says. “Not only enterprises, but the midmarket can have huge problems during email authentication deployment. It’s straightforward or easy to do at first glance, but if you do something wrong, totally valid emails will be rejected.”
Here’s what to remember when establishing DMARC to your group.
1. SPF Alerts Recipients to Emails From Nonapproved Sources
The primary DNS document that a company must arrange is SPF, a string that lists the IP addresses and domains of the mail servers approved to ship e mail on behalf of the area. This document is often arrange via your area supplier or e mail internet hosting supplier.
A typical SPF document is a DNS TXT document and appears like:
v=spf1 ip4:192.168.1.1 ip4:192.168.2.1 embody:instance.com -all
The “v=spf1” designates the string as an SPF document and is required for all SPF information. The “ip4” fields listing the IP addresses which might be allowed to ship e mail on behalf of the area and might embody community addresses utilizing the slash notation. The “include” tag lists the third-party domains which might be approved to ship e mail for the area, whereas the “-all” flag specifies that each different area shouldn’t be allowed. Different variants, corresponding to “~all,” are doable and specify that mail from different domains are allowed however marked insecure, whereas “+all” permits any server to ship e mail on behalf of the area.
Whereas the SPF document is an effective first step, spammers might exploit the truth that different organizations utilizing a typical third-party server, corresponding to Google’s, can be approved to ship e mail on behalf of each different group utilizing that server.
2. DKIM Makes use of PKI to Confirm E-mail Messages
DKIM solves the issue of a number of tenants on the identical e mail server and provides e mail verification as nicely. The DKIM selector and secret is generated by your e mail supplier after which registered as a TXT document in your DNS service supplier.
A typical DKIM document is a DNS TXT document with a selector — a reputation — corresponding to “[third party]._domainkey” and a price of:
v=DKIM1; okay=rsa; p={public key string}
The “v=DKIM1″‘ designates the TXT string as a DKIM document and is required for all DKIM information. The “k=rsa” designates the kind of encryption used for the public-key information, with RSA because the default and different values, corresponding to Edwards-curve Digital Signature Algorithm (EdDSA), allowed as nicely. The “p=” tag accommodates the public-key information generated by the e-mail service supplier.
As with all public-key encryption infrastructure, organizations ought to make sure that to frequently rotate the keys for his or her area infrastructure, says EasyDMARC’s Hovannisyan.
“We have password management systems or rotating password for other [types of] keys, but we don’t do that with DKIM keys,” he says. “This is something that should be in place and each time something can be broken, you need to have alerting.”
3. DMARC Establishes Insurance policies for E-mail Recipients
Area-based Messaging Authentication, Reporting and Conformance — or DMARC — makes use of the already-established controls of SPF and DKIM and specifies a company’s e mail coverage — not for emails coming into the group, however for emails claiming to be despatched on behalf of the group. Organizations that specify a DMARC document achieve two advantages: They will inform a receiving server what to do with an e mail that fails authentication — corresponding to enable supply, quarantine the message, or reject it — and so they direct the receiving server to generate stories about any messages despatched to the area.
The result’s that a company utilizing DMARC good points visibility into how their area title and model is being utilized by unauthorized events.
A typical DMARC document is a DNS TXT document with a ‘_DMARC’ and a price that could be a string with a variety of fields, corresponding to:
v=DMARC1; p=reject; adkim=s; aspf=s; rua=mailto:[email protected]
On this instance, the ‘v=DMARC1’ is the required identifier, the authentication insurance policies for each SPF and DKIM at set to strict — as designated by the ‘aspf=s’ and ‘adkim=s’ tags — and the DMARC stories are despatched to an organization-specific e mail at a third-party supplier. On this case, the coverage is ready to reject, however corporations can begin with a coverage of ‘none’ to achieve entry to the reporting and transfer to a coverage of ‘quarantine’.
4. Verify Your DMARC Reviews Recurrently and Keep Data
Establishing a DMARC coverage is pretty easy, however utilizing the added info as a part of an email-security and brand-protection program requires an alerting mechanism and common oversight. Usually corporations will simply insert a sound DMARC document of their DNS with a coverage of ‘none’ after which overlook in regards to the added risk intelligence, says EasyDMARC’s Hovannisyan.
“One of the biggest mistakes with DMARCs is [company’s saying] that once it’s done, I don’t need to do anything more,” he says.
As a substitute, corporations ought to superior via the completely different insurance policies, beginning with ‘none,’ however rapidly transferring to ‘quarantine’ after which lastly ‘strict.”‘
While DMARC can be easy to manage for small companies, large enterprises will likely want to adopt a service to manage the configuration of its email infrastructure and make use of the added capabilities.
“For a small deployment, the place you mainly simply have, a Google or an Workplace 365 in your area, it is fairly easy,” says Red Sift’s Powar. “I imply, the spec is kind of easy, however as quickly as you add a bit little bit of complexity — when you begin together with a advertising division, an HR division, or perhaps a procurement division — you are going to discover a whole lot of senders immediately begin to seem out of your infrastructure.”
5. Contemplate BIMI to Improve Belief
Finally, companies have a fourth standard that can help add more trust to their email messages. The Brand Indicators for Message Identification — or BIMI — standard allows companies to register their logo for use in email clients, but only after they have adopted the maximum level of strictness for their DMARC policy.
Whereas nearly three-quarters of huge organizations (73%) have adopted the most basic version of DMARC, the share of those organizations that would pass the most stringent standards vary significantly by nation: 77% of companies in the United States have a strict policy, while only 40% in Germany and 15% in Japan do, according to information from threat-intelligence supplier Crimson Sift. Of all domains, only 3% are considered ready for BIMI, but 32% of the 7.9 million DMARC-enabled domains have strict enough policies to adopt BIMI, in line with the BIMIRadar monitoring website.