A risk actor tracked as TA547 has focused dozens of German organizations with an data stealer known as Rhadamanthys as a part of an invoice-themed phishing marketing campaign.
“This is the first time researchers observed TA547 use Rhadamanthys, an information stealer that is used by multiple cybercriminal threat actors,” Proofpoint mentioned. “Additionally, the actor appeared to use a PowerShell script that researchers suspect was generated by a large language model (LLM).”
TA547 is a prolific, financially motivated risk actor that is recognized to be lively since at the least November 2017, utilizing e-mail phishing lures to ship a wide range of Android and Home windows malware corresponding to ZLoader, Gootkit, DanaBot, Ursnif, and even Adhubllka ransomware.
Lately, the group has developed into an preliminary entry dealer (IAB) for ransomware assaults. It has additionally been noticed using geofencing tips to limit payloads to particular areas.
The e-mail messages noticed as a part of the most recent marketing campaign impersonate the German firm Metro AG and comprise a password-protected ZIP file containing a ZIP archive that, when opened, initiates the execution of a distant PowerShell script to launch the Rhadamanthys stealer immediately in reminiscence.
Curiously, the PowerShell script used to load Rhadamanthys contains “grammatically appropriate and hyper particular feedback” for every instruction in this system, elevating the chance that it might have been generated (or rewritten) utilizing an LLM.
The alternate speculation is that TA547 copied the script from one other supply that had used generative AI know-how to create it.
“This campaign represents an example of some technique shifts from TA547 including the use of compressed LNKs and previously unobserved Rhadamanthys stealer,” Proofpoint mentioned. “It additionally gives perception into how risk actors are leveraging seemingly LLM-generated content material in malware campaigns.”
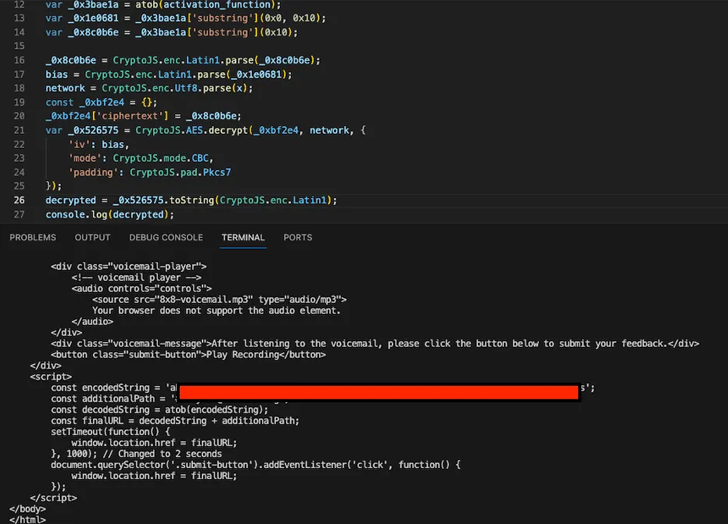
The event comes as phishing campaigns have additionally been banking on unusual ways to facilitate credential-harvesting assaults. In these emails, recipients are notified of a voice message and are directed to click on on a hyperlink to entry it.
The payload retrieved from the URL is closely obfuscated HTML content material that runs JavaScript code embedded inside an SVG picture when the web page is rendered on the goal system.
Current inside the SVG information is “encrypted data containing a second stage page prompting the target to enter their credentials to access the voice message,” Binary Protection mentioned, including the web page is encrypted utilizing CryptoJS.
Different email-based assaults have paved the best way for Agent Tesla, which has emerged as a horny possibility for risk actors on account of it “being an affordable malware service with multiple capabilities to exfiltrate and steal users’ data,” in accordance with Cofense.
Social engineering campaigns have additionally taken the type of malicious adverts served on engines like google like Google that lure unsuspecting customers into downloading bogus installers for well-liked software program like PuTTY, FileZilla, and Room Planner to finally deploy Nitrogen and IDAT Loader.
The an infection chain related to IDAT Loader is noteworthy for the truth that the MSIX installer is used to launch a PowerShell script that, in flip, contacts a Telegram bot to fetch a second PowerShell script hosted on the bot.
This PowerShell script then acts as a conduit to ship one other PowerShell script that is used to bypass Home windows Antimalware Scan Interface (AMSI) protections in addition to set off the execution of the loader, which subsequently proceeds to load the SectopRAT trojan.
“Endpoints can be protected from malicious ads via group policies that restrict traffic coming from the main and lesser known ad networks,” Jérôme Segura, principal risk researcher at Malwarebytes, mentioned.