Container safety has skilled important transformation over the previous decade. From the emergence of foundational instruments like Docker to the maturation of orchestration platforms resembling Kubernetes, the container safety panorama appears to be like completely different than it did even a couple of years in the past. With Gartner predicting 95% of organizations will likely be operating containerized purposes in manufacturing by 2028, it’s clear that container safety goes to be a key precedence for many organizations transferring ahead. The fast evolution of know-how has not solely pushed developments in containerization however has additionally created alternatives for assaults focusing on containers and cloud-native infrastructure. Attackers are in a position to automate their reconnaissance and different techniques as a result of uniformity of cloud suppliers’ APIs and architectures, executing assaults in lower than 10 minutes. Organizations must rethink their strategy to cloud container safety and workload safety or danger being outpaced by these assaults.
A New Regular Brings New Challenges
In fashionable software growth, containers are shortly changing into a well-liked device for builders, offering quite a few benefits together with improved agility and scalability. They supply builders with flexibility to replace a particular container or microservice as a substitute of your entire software, enormously dashing the tempo of innovation. The convergence of cloud migration and widespread adoption of DevOps practices has pushed containerization as a prevailing pattern, empowering organizations to streamline their operations and enhance the tempo of latest releases.
Whereas adoption will increase yearly, containers are nonetheless a comparatively younger know-how, with many firms nonetheless within the early levels of their containerization journey. The ever-evolving know-how ecosystem surrounding containers, together with Kubernetes, introduces fixed shifts and updates, and growth groups and infrastructure expanded sooner than safety groups. In consequence, there’s a common shortage of cloud-native safety expertise and experience wanted to successfully safe these environments. We have now additionally seen builders more and more shoulder safety tasks as organizations embrace DevSecOps methods. Containers provide many benefits for innovation and agility, however in addition they develop the potential assault floor, posing a problem for safety groups attempting to steadiness safety and velocity.
Two Sides Of Container Safety
As container know-how continues to mature, two key safety traits have emerged over the previous few years. The primary revolves round key dangers getting obscured by the infinite noise and alerts created by many safety instruments. Beneath the DevSecOps mannequin, builders are sometimes accountable for fixing vulnerabilities within the code packages they deploy however discover themselves overwhelmed by the sheer quantity of alerts. Our analysis discovered that of cloud workloads with essential or excessive severity vulnerabilities, just one.2% are exploitable, have a repair, and are literally in use by the appliance.The variety of new cloud-related CVEs elevated by almost 200% in 2023, and the sharing of open supply container pictures has left safety groups going through a lot of essential and high-severity container vulnerabilities. The problem many organizations face lies in discerning which of those dangers even have a excessive likelihood of exploitation and which will be deprioritized. The very last thing any developer or safety staff desires is to waste useful time sifting by way of a protracted record of safety findings, solely to find that many are inconsequential.
The second main pattern is the spectacular velocity at which cloud assaults now transfer. As extra firms have shifted to cloud-native purposes, attackers have tailored to leverage the structure upon which these apps are constructed. After discovering an exploitable asset, malicious actors want solely minutes to execute an assault and begin inflicting harm. The preliminary levels of cloud assaults will be closely automated, and attackers are arising with all types of subtle methods to disguise their presence. In simply the previous yr, we’ve noticed quite a few assaults the place a malicious actor gained preliminary entry by way of a vulnerability in a container picture or open supply software program dependency, together with the well-known SSHD backdoor in XZ Utils. As soon as infiltrating the surroundings, attackers can simply transfer laterally – whether or not from workload to cloud or vice versa – trying to find credentials or delicate information to use for revenue.

A Trendy Method To Cloud Container Safety And Workload Safety
Because the container safety panorama evolves, organizations wish to strike a steadiness between prevention and protection. Initially, many utilized completely different instruments to safe their containers than they used for different components of their cloud infrastructure. Nevertheless, container threats now typically cross cloud domains, making this segmented strategy gradual and outdated. The shortage of communication between these instruments ends in viewing container safety in isolation. Whereas an remoted device would possibly detect a malicious actor breaching a susceptible container, the post-escape assault path stays obscured. A extra strong strategy is to make use of a unified platform that connects the dots throughout your broad cloud infrastructure to thwart and reply to threats with agility. Already, quite a few enterprises have began this journey in direction of consolidating cloud safety. Within the 2023 Gartner® Market Information for Cloud-Native Software Safety Platforms (CNAPP), Gartner predicts this pattern will proceed, forecasting that by 2025, 60% of enterprises may have consolidated cloud workload safety platform (CWPP) and cloud safety posture administration (CSPM) capabilities to a single vendor or CNAPP. Container safety falls squarely into this class of CWPP and safety leaders and practitioners might want to sustain with this modification because the boundaries between domains throughout the cloud start to blur.
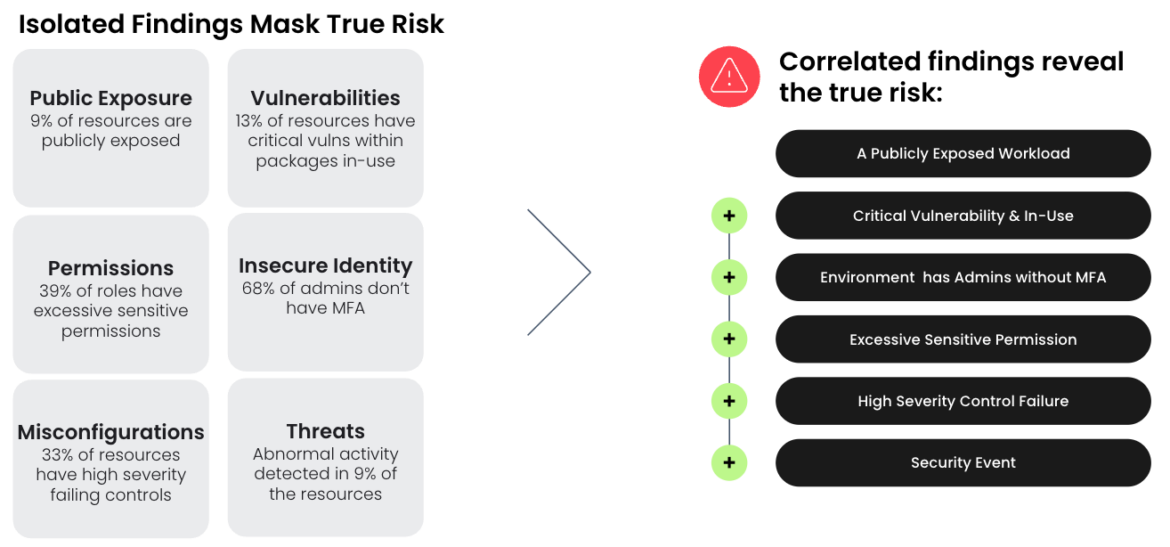
To adapt to this new regular, organizations must rethink their strategy to container safety. Regardless of the evolving risk panorama, the basic problem stays the identical: safety and developer groups should catch vulnerabilities in container pictures and detect threats at runtime. However now, they have to strategy this problem with a unique lens. Within the fashionable surroundings, container safety and workload safety want cloud context to be actually efficient. Correlating container findings with context throughout the cloud is important to getting the total image of how an attacker can exploit your surroundings. Armed with this context, groups can deal with energetic real-time danger of their group and examine containers as half of a bigger story.
Container safety and workload safety sometimes encompasses use circumstances like risk detection and response, vulnerability administration, and Kubernetes safety posture administration (KSPM). These components stay essential, however this new strategy integrates them with findings like real-time configuration modifications, dangerous identification habits, and cloud log detections. These different findings are often related to CSPM however have gotten related for container safety. Combining these elements with real-time contextual insights on vulnerabilities and container threats paints a complete image of potential assault paths all through a consumer’s surroundings. Solely specializing in containers might reveal an preliminary breach however fails to unveil the extent of injury or anticipate the attacker’s subsequent transfer. So long as your group has workloads operating within the cloud, this extra cloud context offers nice worth.
Bringing The Finest Of Agent And Agentless To Workload Safety
The easiest way to attain this steadiness of safety and velocity combines agent-based and agentless methods. There may be an ongoing debate over whether or not agent-based or agentless approaches are simpler, with agentless instrumentation changing into a well-liked strategy because of its ease of deployment and fast time to worth. Because of this, many safety groups want to implement an agentless strategy wherever doable. Whereas there are advantages to each approaches, the best options will combine each for complete visibility. For containers, brokers present deeper runtime visibility and real-time detection for sooner time to discovery. Sadly, it’s not at all times doable to deploy them universally because of useful resource constraints.
In these circumstances, leveraging agentless instrumentation to complement brokers ensures full breadth of protection throughout your infrastructure. For container safety, deploying brokers strategically lets you prioritize vulnerabilities based mostly on in-use packages and detect threats in actual time – capabilities that aren’t doable with a solely agentless strategy. Supplementing this with agentless deployments allows fast primary vulnerability scanning throughout all containers. As beforehand highlighted, integrating cloud context into workload safety – typically achieved by way of agentless means – is an effective way to anticipate and fight stay assaults. This strategy not solely tackles the normal challenges related to container safety and workload safety but additionally offers a full image and wealthy context to deal with probably the most important dangers. Each approaches deliver clear advantages to container safety, however this new strategy of implementing agentless the place doable to complement the deeper insights from brokers brings the very best of each worlds.
Safety Should Proceed To Adapt
The rise of containerization and cloud-native purposes, together with the advances made by attackers, has introduced us to a difficult level for workload safety. On this fixed chess recreation, safety groups should stay proactive and adaptable, constantly evolving their defenses or danger being breached by rising threats.
In the end, organizations that adapt the quickest will likely be greatest geared up to detect assaults that strike with out warning in a matter of minutes. As boundaries between cloud domains proceed to change into much less outlined and the market strikes in direction of consolidation, the flexibility to attach occasions throughout your complete cloud infrastructure will likely be key to defending your belongings and mitigating danger.
