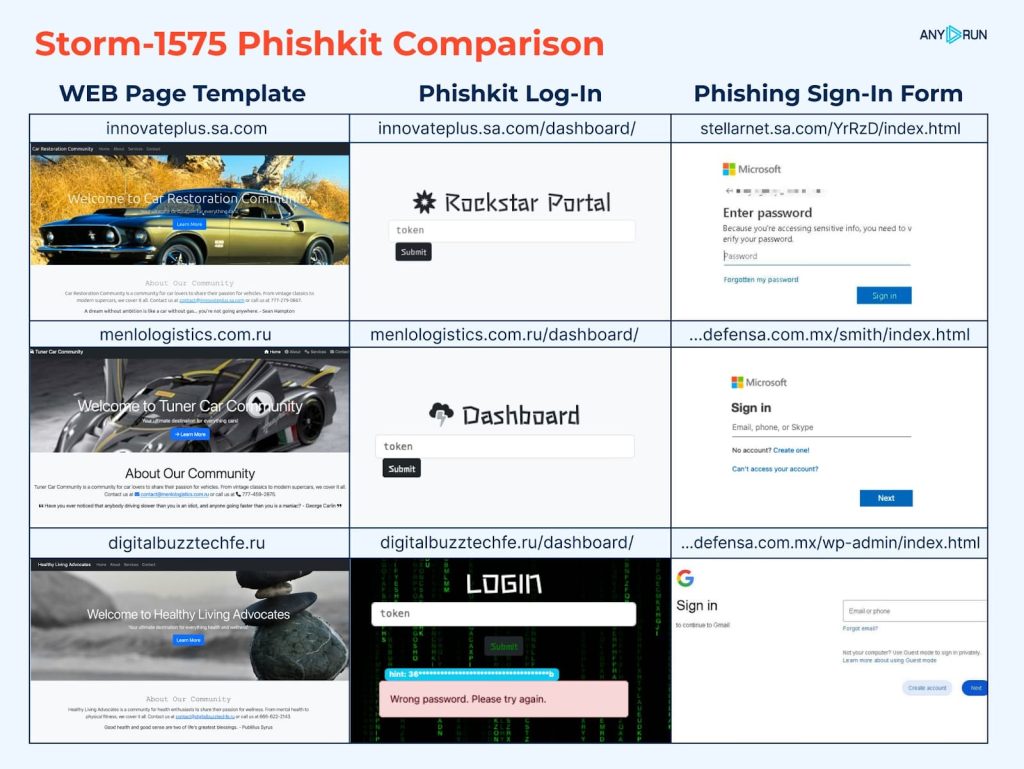
The Storm-1575 group is understood for steadily rebranding its phishing infrastructure. Lately, ANY.RUN analysts recognized the deployment of latest login panels, that are a part of the risk actor’s ongoing efforts to compromise customers’ Microsoft and Google accounts.
Storm-1575’s New Login Panels
Via evaluation of their options, the staff was capable of hyperlink login panels to Storm-1575. Amongst different issues, the panels share:
- Phishing domains
- Random panel web page headers
- Use of web site templates to masks servers
- Panel token verification request, the identical font, and the panel URL
The panels even have their distinctive options:
- Goal Accounts: Microsoft vs. Google
- Verification: Cloudflare for Microsoft, arithmetic CAPTCHA for Google
- Encryption: Sturdy AES CryptoJS for Microsoft, weak obfuscation for Google
The findings verify that these panels are operated by Storm-1575, a bunch that beforehand used the identical infrastructure with different phishing platforms resembling DadSec, Phoenix Panel, and Rockstar2FA Portal.
Easy methods to Proactively Uncover New Storm-1575 Assaults
To remain forward of Storm-1575’s newest phishing techniques, cybersecurity professionals can use ANY.RUN’s Menace Intelligence Lookup.
This highly effective platform affords a centralized repository of risk knowledge from ANY.RUN’s malware sandbox classes, allow customers to research rising threats with entry to indicators of compromise, community exercise, and file behaviours.
One instance of Storm-1575’s phishing infrastructure is the area menlologistics.com. By submitting this area to the TI Lookup platform, customers can uncover key particulars about its malicious exercise.
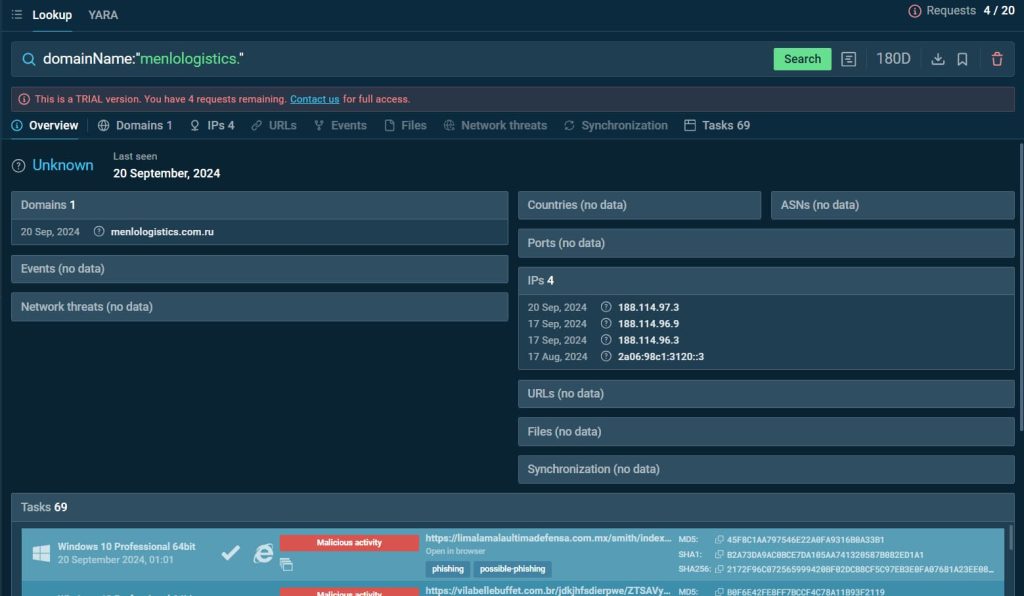
A search question for domainName:”menlologistics.” revealed 4 related IP addresses and 69 sandbox classes in ANY.RUN, most of which had been linked to phishing actions.
Analysts may also examine by risk title utilizing threatName:”storm1575″, granting direct entry to any recorded session the place this risk was detected within the ANY.RUN sandbox.
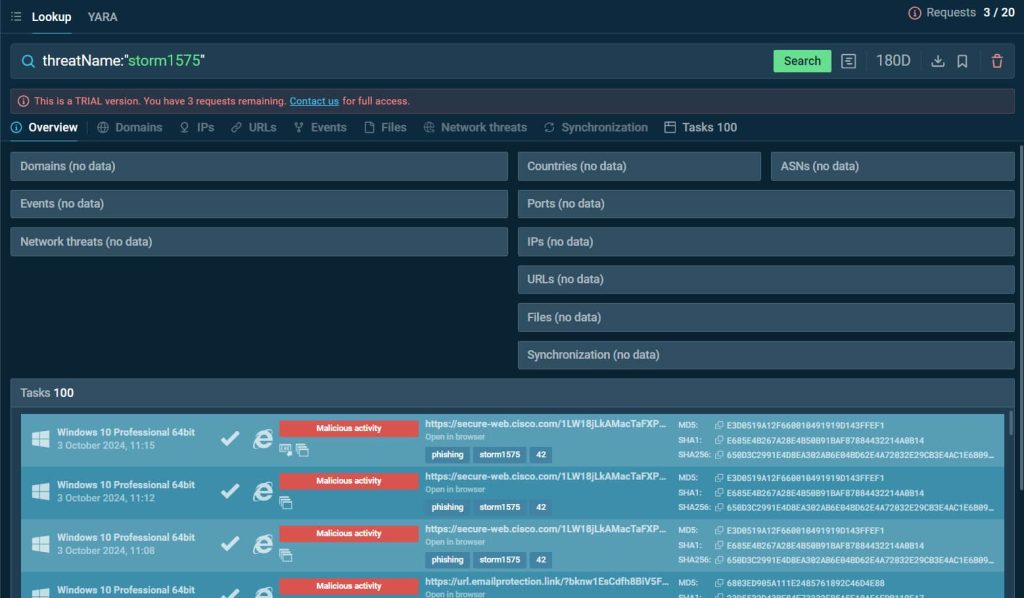
This integration between TI Lookup and the sandbox supplies a complete view of the risk panorama, enabling customers to evaluation real-time phishing techniques and infrastructure in motion.
ANY.RUN Menace Intelligence Portal
In case you’re trying to improve your risk intelligence capabilities, discover ANY.RUN’s TI portal to achieve deeper insights into the world of cyber threats and strengthen your defences.
Take a look at ANY.RUN’s Menace Intelligence Lookup to see the way it can enhance your threat-hunting efforts.
RELATED TOPICS
- Evaluation of Prime Infostealers: Redline, Vidar and Formbook
- PythonAnywhere Cloud Platform Abused for Internet hosting Ransomware
- Tycoon and Storm-1575 Linked to Phishing Assaults on US Faculties
- ANY.RUN Upgrades Menace Intelligence to Establish Rising Threats
- StormBamboo APT Targets ISPs, Spreads Malware by way of Software program Updates