A stealthy Linux malware named ‘sedexp’ has been evading detection since 2022 through the use of a persistence method not but included within the MITRE ATT&CK framework.
The malware was found by danger administration agency Stroz Friedberg, an Aon Insurance coverage firm, and allows its operators to create reverse shells for distant entry and to additional the the assault.
“At the time of this writing, the persistence technique used (udev rules) is not documented by MITRE ATT&CK,” the researchers notice, highlighting that sedexp is a sophisticated menace that hides in plain web site.
Persisting through udev guidelines
‘udev‘ is a tool administration system for the Linux kernel liable for dealing with gadget nodes within the /dev listing, which comprises information that symbolize the {hardware} elements avaialble on the system comparable to storage drives, community interfaces, and USB drives.
Node information are dynamically created and eliminated when the person connects/disconnects units, whereas udev additionally handles the loading of acceptable drivers.
Udev guidelines are textual content configuration information that dictate how the supervisor ought to deal with sure units or occasions, positioned in ‘/and so forth/udev/guidelines.d/’ or ‘/lib/udev/guidelines.d/.’
These guidelines comprise three parameters that specify its applicability (ACTION== “add”), the gadget title (KERNEL== “sdb1″), and what script to run when the desired circumstances are met (RUN+=”/path/to/script”).
The sedexp malware provides the next udev rule on compromised techniques:
ACTION=="add", ENV{MAJOR}=="1", ENV{MINOR}=="8", RUN+="asedexpb run:+"
This rule triggers each time a brand new gadget is added to the system, checking if its main and minor numbers match ‘/dev/random,’ which is loaded upon system boot and used as a random quantity generator by a number of apps and system processes.
The ultimate rule element (RUN+= “asedexpb run:+”) executes the malware’s script ‘asedexpb,’ so by setting /dev/random as a precondition, the attackers make sure the malware is run often.
Most significantly, /dev/random is a vital system element on Linux that safety options don’t monitor. Therefore, its abuse ensures evasion for the malware.
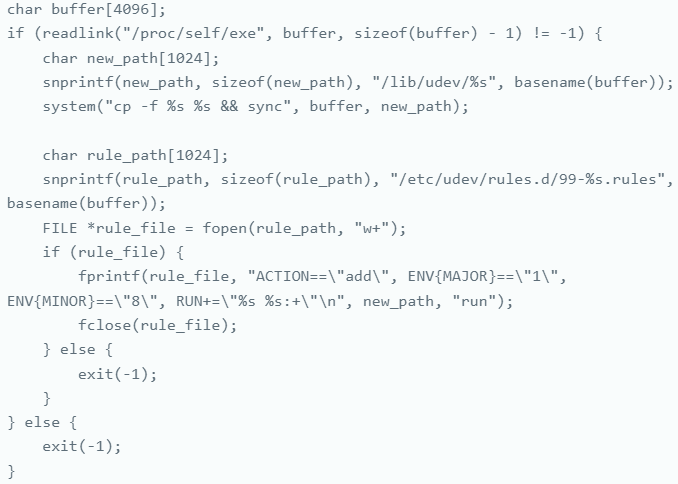
Supply: Aon
Main operational capabilities
The malware names its course of’ kdevtmpfs,’ which mimics a legit system course of, additional mixing in with regular actions and making it more durable to detect utilizing typical strategies.
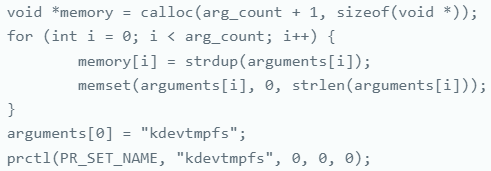
Supply: Aon
Relating to its operational capabilities, the malware makes use of both forkpty or pipes and a forked new course of to arrange a reverse shell for the attacker to remotely entry the contaminated gadget.
Sedexp additionally employs reminiscence manipulation methods to cover any file containing the string “sedexp” from commonplace instructions like ‘ls’ or ‘discover,’ concealing its presence on the system.
It might probably additionally modify reminiscence contents to inject malicious code or alter the conduct of present apps and system processes.
The researchers point out that the malware has been used within the wild since not less than 2022. They discovered it current in lots of on-line sandboxes and with out being detected (on VirusTotal solely two antivirus engines flag as malicious the three sedexp samples obtainable within the report).
Based on Stroz Friedberg, the malware has been used to cover bank card scraping code on an online server compromised internet servers, indicating involvement in financially motivated assaults.
